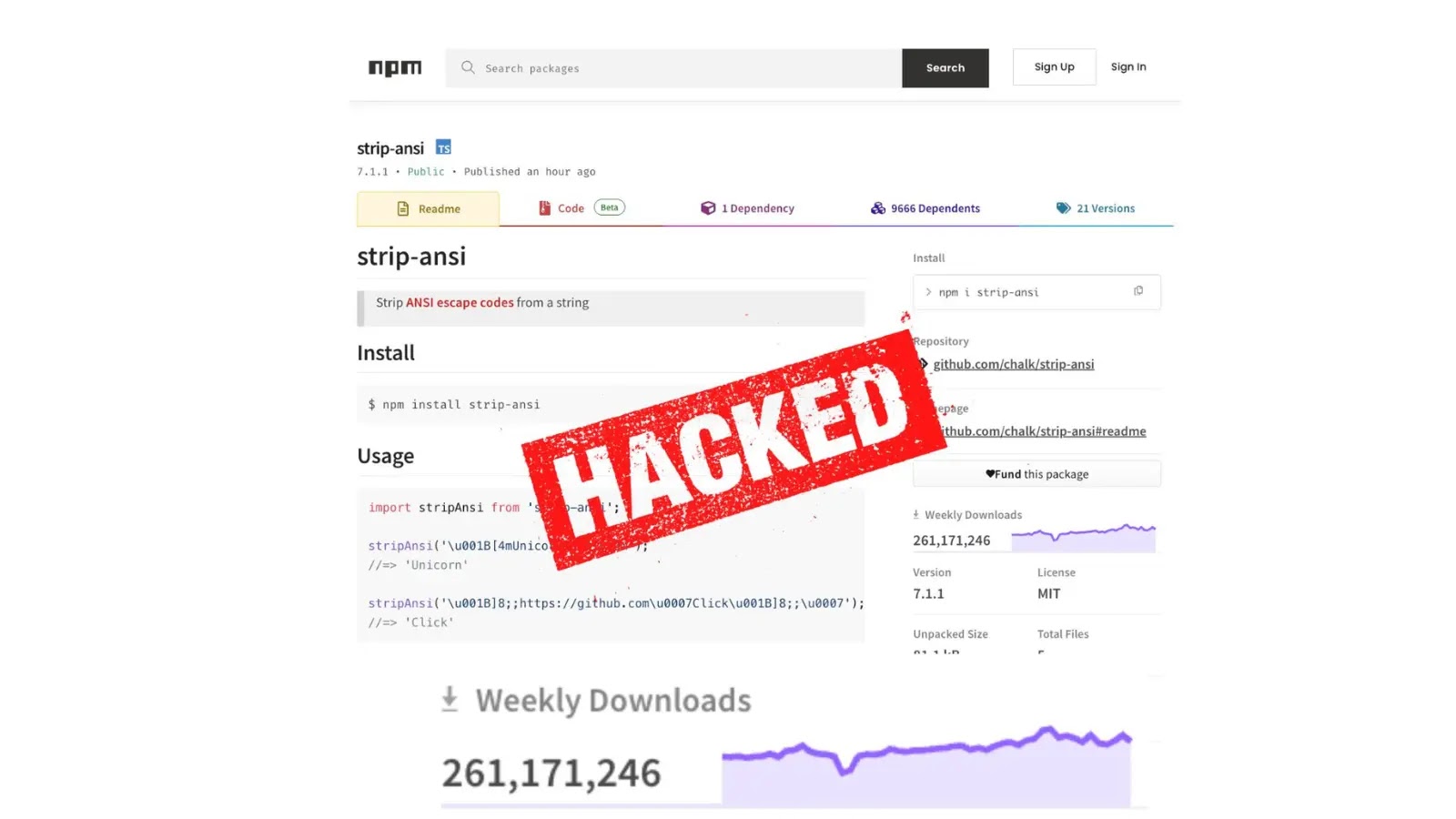
Within the largest provide chain assault, hackers compromised 18 widespread npm packages, which collectively account for over two billion downloads per week. The assault, which started on September eighth, concerned injecting malicious code designed to steal cryptocurrency from customers.
The compromised packages embrace extensively used libraries reminiscent of chalk, debug, ansi-styles, and supports-color. The malicious code was added in new variations of those packages and was engineered to execute on the client-side of internet sites utilizing them.
The malware silently intercepts cryptocurrency and Web3 actions throughout the browser, manipulating pockets interactions and rewriting fee locations to redirect funds to attacker-controlled accounts.
Common npm Packages Hacked
The malware operates as a classy in-browser interceptor, concentrating on each community visitors and application-level APIs. It achieves this by hooking into core browser features like fetch XMLHttpRequest, in addition to interfaces for widespread crypto wallets for Ethereum, Solana, and different blockchains, Akidio noticed.
The malicious code works in a collection of steps:
Injection and Hooking: It embeds itself into the browser atmosphere and takes management of features associated to net requests and pockets communications.
Scanning for Delicate Knowledge: The malware actively scans community responses and transaction particulars for patterns matching cryptocurrency pockets addresses for numerous blockchains, together with Bitcoin, Ethereum, Solana, Tron, Litecoin, and Bitcoin Money.
Rewriting Pockets Addresses: Upon discovering a legit deal with, the malware replaces it with a look-alike deal with from a hardcoded record belonging to the attackers. That is carried out utilizing string-matching algorithms to make the swap much less noticeable to the person.
Hijacking Transactions: The code alters transaction parameters earlier than the person indicators them. Which means that even when the person interface shows the right recipient deal with, the signed transaction will route funds or grant token approvals to the attackers.
The maintainer of the compromised packages revealed they fell sufferer to a phishing assault. An electronic mail, seemingly from npm help, was despatched from the area npmjs.assist, tricking the developer into revealing their credentials, in accordance with a Hacker Information put up.
This area was registered solely three days earlier than the assault on September 5, 2025.
Phishing Mail compromised the developer
The maintainer turned conscious of the compromise and commenced taking steps to take away the malicious variations of the packages. Nevertheless, on the time of the report, at the least one package deal, simple-swizzle, remained compromised.
The incident additionally revealed that the identical attackers could have compromised one other package deal, proto-tinker-wc, utilizing related strategies.
The next desk lists the affected packages and the compromised variations:
PackageMalicious Versionbackslash0.2.1chalk-template1.1.1supports-hyperlinks4.1.1has-ansi6.0.1simple-swizzle0.2.3color-string2.1.1error-ex1.3.3color-name2.0.1is-arrayish0.3.3slice-ansi7.1.1color-convert3.1.1wrap-ansi9.0.1ansi-regex6.2.1supports-color10.2.1strip-ansi7.1.1chalk5.6.1debug4.4.2ansi-styles6.2.2
Discover this Story Attention-grabbing! Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates.