Fb customers are more and more turning into targets of a classy phishing method that bypasses typical safety measures.
With over three billion lively customers on the platform, Fb represents a lovely goal for attackers in search of to compromise accounts and harvest private credentials.
The first goal of those assaults stays clear: steal login credentials to hijack accounts, unfold fraudulent schemes, steal delicate information, and commit identification fraud throughout sufferer networks.
Within the second half of 2025, a noticeable surge in Fb phishing campaigns emerged, using varied strategies to deceive customers.
Amongst these methods, one technique stands out for its technical sophistication and effectiveness.
Pretend legislation agency electronic mail (Supply – Trellix)
The menace panorama has shifted dramatically, with attackers transferring past easy malicious hyperlinks towards extra superior approaches that exploit person belief and familiarity with reliable login processes.
Trellix analysts recognized and documented this rising menace after observing elevated phishing exercise focusing on the platform.
The researchers famous that attackers have been implementing superior social engineering ways mixed with technical evasion measures to maximise their success charges.
This statement marks an essential evolution in Fb-targeted assaults, indicating that menace actors are investing in additional refined methodologies to bypass conventional safety consciousness coaching.
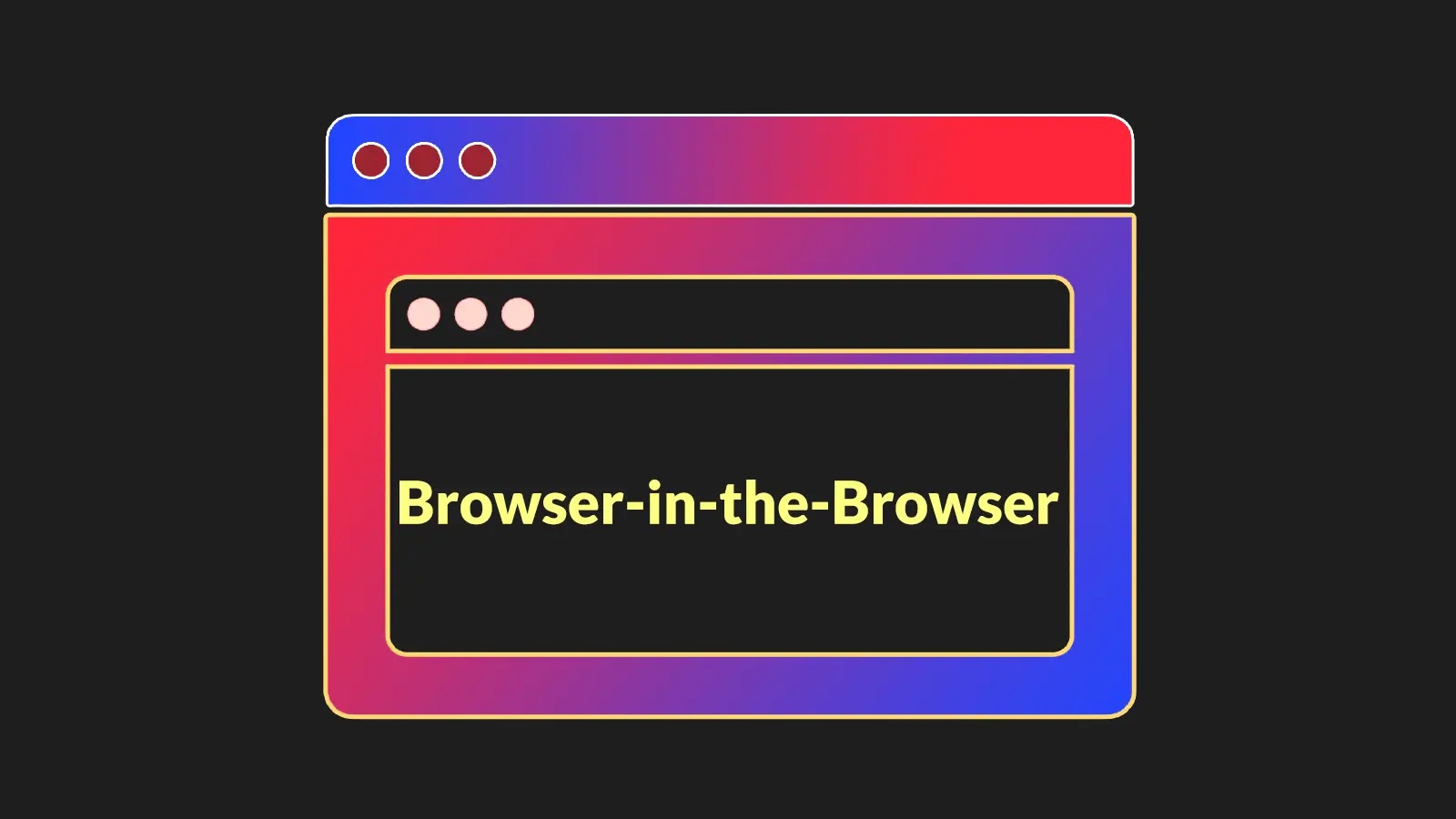
Browser-in-the-Browser (BitB) method
The Browser-in-the-Browser (BitB) method represents probably the most notable innovation in these campaigns.
This technique works by creating a very custom-built faux window that exists totally throughout the sufferer’s reliable browser window, making it almost unimaginable to differentiate from real authentication pop-ups.
The method exploits customers’ familiarity with login home windows, capitalizing on their expectation to see such prompts when accessing the platform.
The assault sequence usually begins with a phishing electronic mail disguised as communication from a legislation agency, containing a faux authorized discover about an infringing video and a Fb login hyperlink.
Pretend captcha immediate (Supply – Trellix)
The hyperlink makes use of shortened URLs that redirect to faux Meta CAPTCHA pages, including extra layers of deception.
When customers work together with these pages, they encounter what seems to be a reliable Fb login pop-up window. Nonetheless, analyzing the underlying code reveals the malicious nature of the assault.
Unauthorized login alert themed Fb phishing (Supply – Trellix)
The Fb URL is hardcoded throughout the faux interface, creating a wholly fraudulent authentication atmosphere.
The sophistication of this strategy lies in how attackers abuse reliable infrastructure. Risk actors host phishing pages on trusted cloud platforms like Netlify and Vercel, leveraging their status to bypass safety filters.
Vercel hosted Fb phishing (Supply – Trellix)
URL shortening providers masks the precise vacation spot, offering extra anonymity.
This mixture of technical sophistication and social engineering represents a major escalation in Fb phishing ways, requiring customers to take care of heightened vigilance past commonplace safety practices.
Observe us on Google Information, LinkedIn, and X to Get Extra InsQtant Updates, Set CSN as a Most popular Supply in Google.