Cellular safety continues to face important challenges as refined malware campaigns evolve to bypass conventional defenses. The Triada Trojan, a persistent risk to Android customers for almost a decade, has resurfaced with a extremely coordinated operation concentrating on promoting networks.
This newest marketing campaign leverages trusted infrastructure to distribute malicious payloads, complicating detection efforts.
By embedding itself inside respectable visitors flows, the malware has efficiently compromised a major variety of units, highlighting the fragility of the digital promoting ecosystem.
The attackers have demonstrated exceptional adaptability, shifting their techniques from easy id fraud to advanced account takeovers.
Within the early phases, they utilized solid paperwork to bypass verification protocols, however current waves have seen them hijacking advertiser accounts that lack sturdy safety measures.
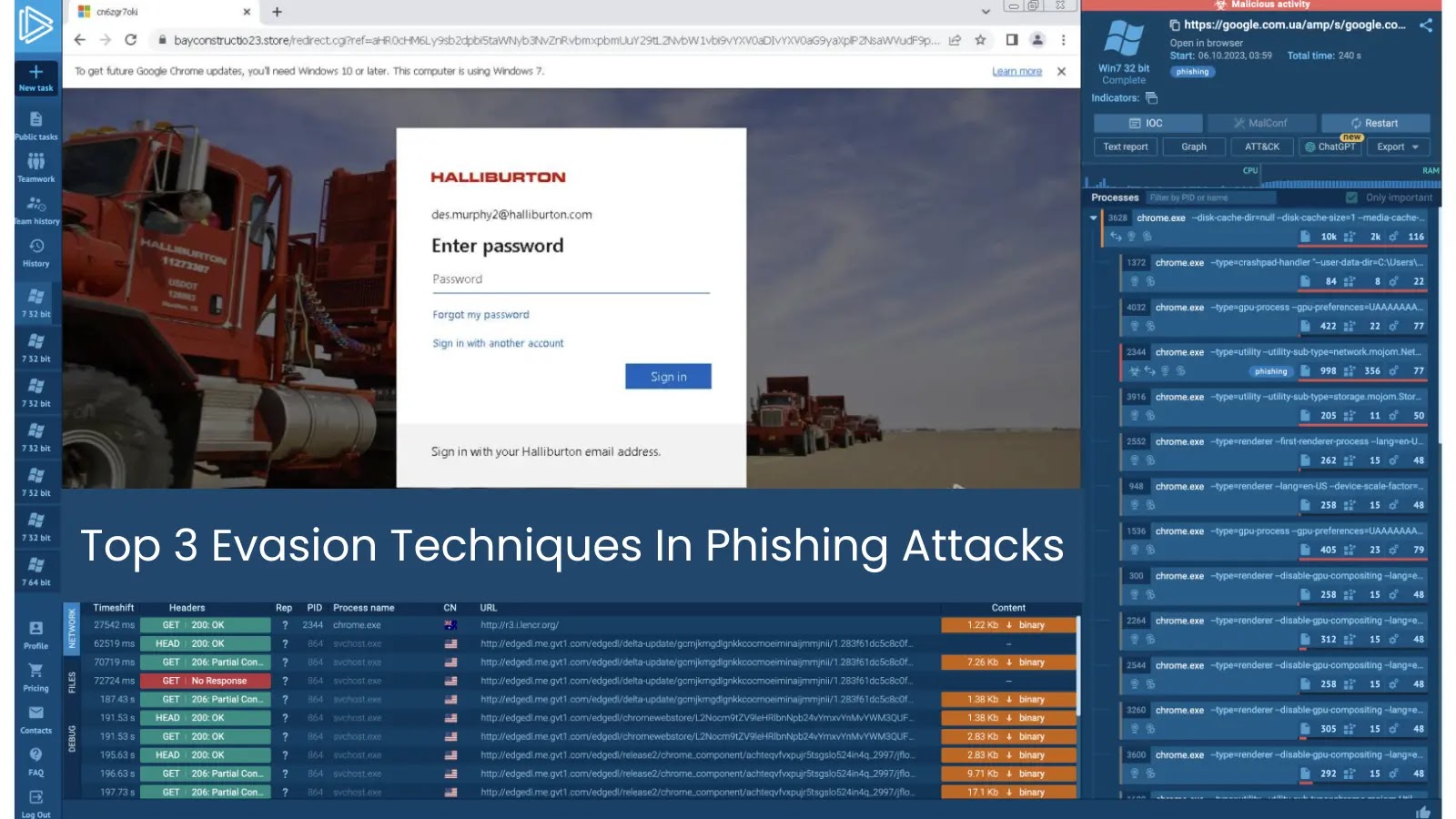
This pivot permits them to launch cloaked campaigns that seem respectable, redirecting unsuspecting customers to malicious content material hosted on respected platforms like GitHub and Discord, which customers sometimes belief.
Adex safety analysts recognized this multi-year operation, noting that Triada exercise accounted for over 15 % of all detected Android malware infections within the third quarter of 2025.
Their investigation revealed a strategic evolution in assault vectors, shifting from low-quality evasion methods to high-level infrastructure abuse.
The analysts documented distinct waves of exercise, every characterised by more and more refined strategies to infiltrate advert networks and distribute the Trojan by way of compromised profiles.
An infection Mechanism and Strategic Evolution
The malware’s development reveals a calculated effort to take advantage of systemic weaknesses in advert community safety protocols.
Between 2020 and 2021, operators centered on bypassing Know Your Buyer procedures utilizing solid id paperwork and repeated top-ups matching identified carding patterns.
These early makes an attempt usually relied on URL shorteners and Content material Supply Networks to masks the malicious nature of their touchdown pages.
By 2022, the technique shifted dramatically in direction of account takeovers, particularly concentrating on advertisers with out two-factor authentication.
The newest wave in 2025 introduces phishing pre-landers designed to imitate respectable Chrome updates.
These pages make use of advanced redirect chains that obscure the ultimate payload’s origin. Suspicious login exercise traced to Turkey and India suggests a coordinated effort to reap credentials and put together compromised accounts for large-scale distribution.
This evolution underscores the vital want for zero-trust safety fashions, together with necessary multi-factor authentication and rigorous area verification, to counter such persistent threats successfully.
Observe us on Google Information, LinkedIn, and X to Get Extra Immediate Updates, Set CSN as a Most well-liked Supply in Google.