A brand new malware marketing campaign has emerged that exploits reputable AI platforms to ship malicious code on to unsuspecting customers.
Menace actors are utilizing sponsored Google search outcomes to redirect customers trying to find widespread macOS troubleshooting suggestions, akin to “the way to clear storage on Mac,” to faux ChatGPT and DeepSeek shared chat hyperlinks.
These shared chats seem to offer useful system directions however truly comprise hidden malicious instructions designed to compromise the goal system.
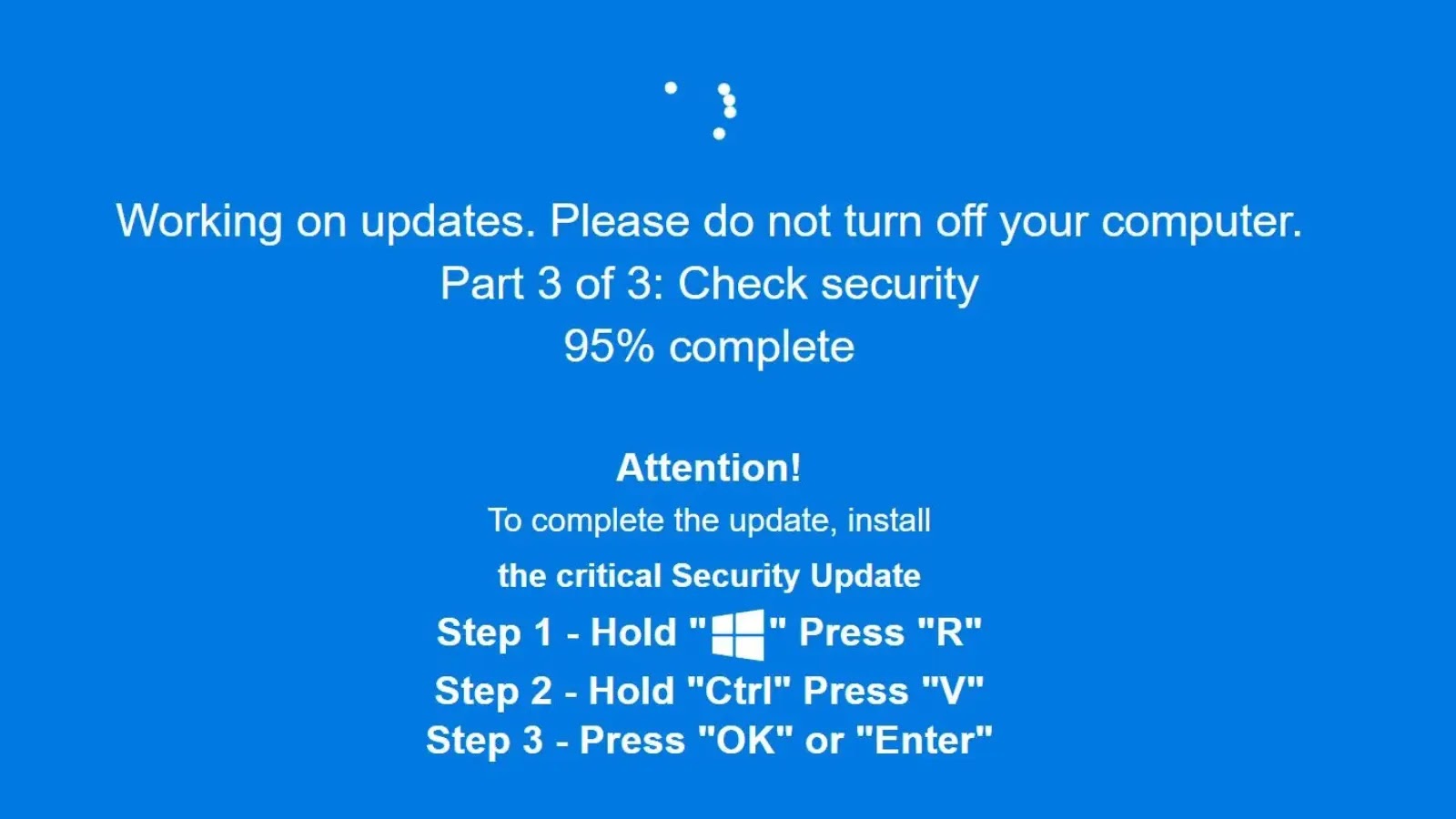
The assault begins when customers encounter a seemingly reputable shared chat that gives step-by-step directions for clearing cupboard space on their Mac.
Nonetheless, embedded inside these directions are base64-encoded instructions that, when executed, obtain and run a complicated multi-stage malware program.
Google Search (Supply – Breakpoint Safety)
This system is intelligent as a result of it bypasses the security checks these AI platforms sometimes make use of, permitting attackers to ship focused, malicious directions on to customers by official channels.
The an infection course of begins with a bash script that prompts customers to enter their system password, masquerading as a credential verification immediate.
As soon as captured, the malware makes use of this password to escalate privileges and obtain the principle malware binary from attacker-controlled servers.
Breakpoint Safety safety analysts recognized this pattern as Shamus, a identified data stealer and cryptocurrency thief that has been extensively documented in safety communities.
Refined tactic
The malware’s sophistication lies in its multi-layered encoding and detection evasion ways.
Reddit Publish (Supply – Breakpoint Safety)
It makes use of arithmetic and XOR encoding mixed with a customized 6-bit decoder to cover its malicious code from evaluation instruments.
This obfuscation makes it extraordinarily tough for safety researchers to establish its true performance by static evaluation alone.
As soon as put in, the malware establishes persistent system entry by making a LaunchDaemon that runs routinely at startup.
This ensures the malware maintains entry even after the person restarts their laptop. The core performance targets delicate knowledge throughout a number of classes, together with browser cookies and passwords from Chrome, Firefox, and 12 different Chromium-based browsers.
Deepseek Publish (Supply – Breakpoint Safety)
The risk extends to cryptocurrency wallets, with the malware particularly focusing on 15 completely different desktop and {hardware} pockets purposes, together with Ledger Reside, Trezor Suite, Exodus, Coinomi, Electrum, and Bitcoin Core.
Moreover, the malware steals your complete macOS Keychain database, Telegram session knowledge, VPN profiles, and information from the desktop and Paperwork folders.
After assortment, all stolen knowledge is compressed and transmitted to the attacker’s command-and-control servers utilizing encrypted communications.
This marketing campaign represents a complicated evolution in malware distribution, demonstrating how risk actors proceed to search out new methods to bypass safety measures and compromise person techniques.
Comply with us on Google Information, LinkedIn, and X to Get Extra Instantaneous Updates, Set CSN as a Most popular Supply in Google.