Cybersecurity researchers have uncovered a classy evolution of the ClickFix assault methodology, the place risk actors are leveraging cache smuggling strategies to keep away from conventional file obtain detection mechanisms.
This progressive marketing campaign targets enterprise networks by masquerading as a Fortinet VPN compliance checking software, particularly exploiting the belief organizations place of their distant entry infrastructure.
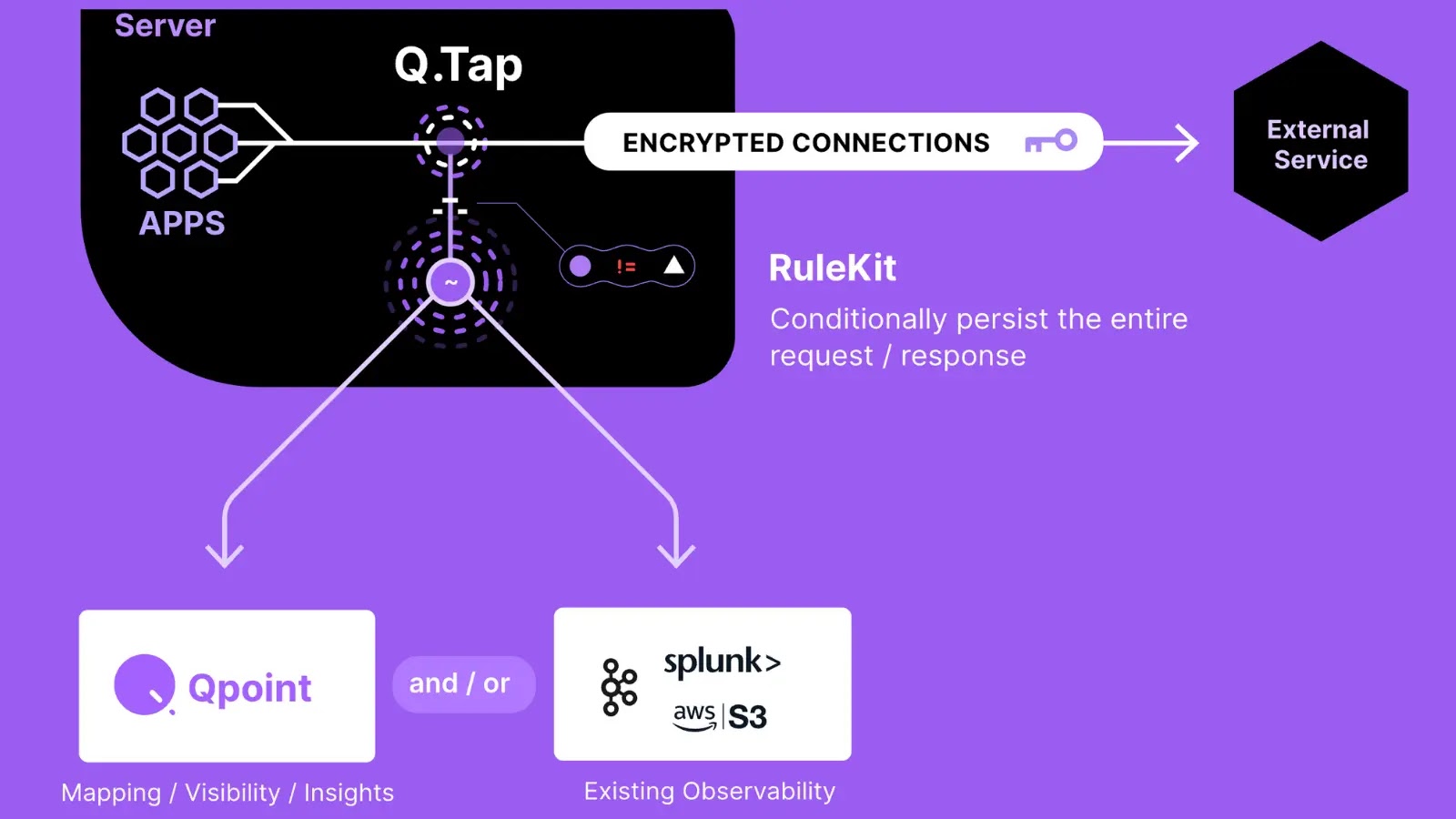
The malicious webpage, hosted on the area fc-checker[.]dlccdn[.]com, introduced itself as a professional company safety utility designed to confirm VPN compliance throughout enterprise environments.
The assault represents a major departure from standard ClickFix variants that usually depend on direct file downloads or specific web communication.
As a substitute, attackers have developed a way that pre-emptively shops malicious payloads inside the browser’s cache system, successfully bypassing many safety controls that monitor file downloads and community communications.
The webpage makes use of Fortinet’s branding to lure customers into working malicious code (Supply – Expel)
Expel analysts famous that this system demonstrates a regarding development in social engineering ways, significantly because it targets Fortinet VPN shoppers predominantly utilized by enterprises for safe distant entry.
What makes this marketing campaign significantly harmful is its skill to seem as if customers are executing information already current on their company community.
The webpage shows a textual content field containing what seems to be a regular community file path: “PublicSupportVPNForticlientCompliance.exe”.
Nevertheless, beneath this veneer of legitimacy lies a fancy PowerShell payload designed to extract and execute malicious code from the browser’s cache with out establishing any exterior community connections.
The Hidden Payload Supply Mechanism
The technical sophistication of this assault facilities round its cache smuggling implementation, which represents a novel strategy to payload supply.
When customers work together with the malicious webpage, an obfuscated JavaScript operate executes a fetch request to “/5b900a00-71e9-45cf-acc0-d872e1d6cdaa”, which presents itself as a professional JPEG picture by setting the HTTP Content material-Kind header to “picture/jpeg”.
The browser mechanically caches this supposed picture file, however examination reveals it accommodates no JPEG header and as an alternative homes a compressed ZIP archive wrapped between distinctive delimiter strings “bTgQcBpv” and “mX6o0lBw”.
The PowerShell script hidden inside the clipboard payload features a subtle regex sample that searches Chrome’s cache listing for these particular delimiters: $m=[regex]::Matches($c,'(?.
As soon as positioned, the script extracts the info between these markers, writes it to “ComplianceChecker.zip”, extracts the archive, and executes “FortiClientComplianceChecker.exe” fully offline.
This system successfully circumvents safety options that monitor file downloads or PowerShell internet requests, as no specific community exercise happens in the course of the malicious execution part.
Comply with us on Google Information, LinkedIn, and X to Get Extra On the spot Updates, Set CSN as a Most popular Supply in Google.