Cybercriminals are more and more exploiting the belief organizations place in synthetic intelligence platforms to conduct subtle phishing assaults, based on a brand new report from cybersecurity agency Cato Networks.
The corporate’s Managed Detection and Response (MDR) service just lately uncovered a marketing campaign the place menace actors leveraged Simplified AI, a well-liked advertising and marketing platform, to steal Microsoft 365 credentials from US-based organizations.
The assault, found in July 2025, efficiently compromised a minimum of one US funding agency earlier than being detected and contained.
Whereas the marketing campaign is not lively, safety specialists warn it represents a harmful evolution in cybercrime ways that would have an effect on organizations throughout all industries.
Weaponizing Trusted AI Platforms
“Menace actors are not counting on suspicious servers or low cost lookalike domains,” the Cato Networks report states.
“As a substitute, they abuse the fame and infrastructure of trusted AI platforms that staff already depend on, permitting them to bypass defenses and slip into organizations below the duvet of legitimacy.”
Weaponizing Trusted AI Platforms
The subtle assault started with emails impersonating executives from a worldwide pharmaceutical distributor, full with genuine firm logos and govt names verified by LinkedIn.
The emails contained password-protected PDF attachments designed to evade automated safety scanners that can’t examine encrypted information.
The phishing marketing campaign employed a multi-layered method that exploited each social engineering and technical evasion ways:
Preliminary Contact: Victims acquired emails showing to be from pharmaceutical firm executives, with passwords for connected PDFs conveniently included within the message physique.
PDF Lure: The paperwork displayed professional firm branding and contained hyperlinks directing customers to Simplified AI’s platform at app.simplified.com.
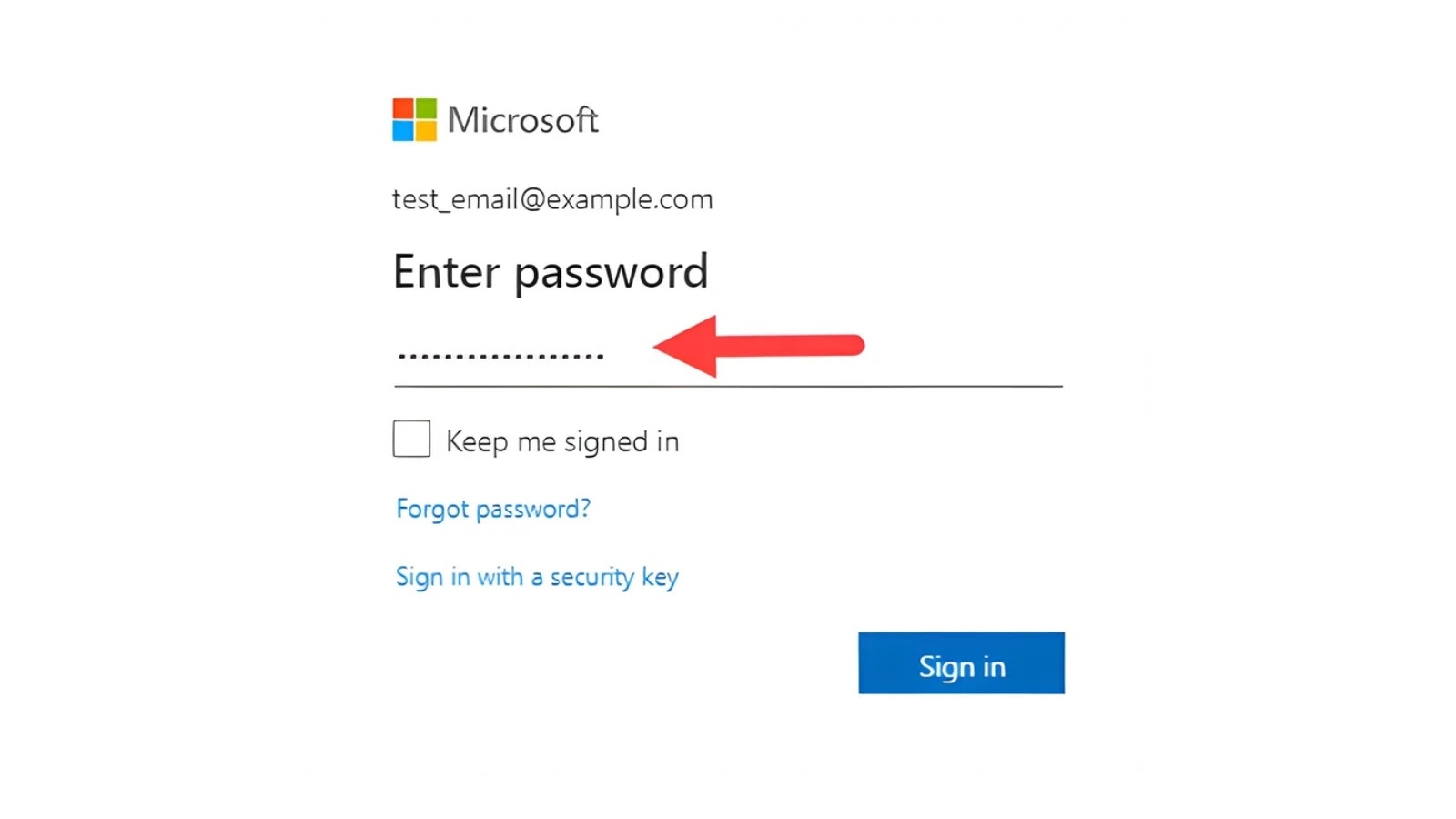
Trusted Redirect: Customers had been taken to what seemed to be a professional Simplified AI web page, displaying the impersonated firm’s identify alongside Microsoft 365 imagery.
Credential Harvest: The ultimate step redirected victims to a convincing pretend Microsoft 365 login portal designed to steal enterprise credentials.
The assault highlights how cybercriminals are adapting to the speedy adoption of AI instruments in company environments.
AI advertising and marketing platforms like Simplified AI have change into commonplace in enterprises, with IT departments routinely whitelisting their domains and permitting worker entry.
pattern malware doc
“For CISOs and IT leaders, approving such providers typically appears simple: permit entry, whitelist the area, and allow the advertising and marketing crew to innovate,” the report notes.
“However what if the exact same platform is leveraged by menace actors to steal from you?”
This incident displays broader issues about “shadow AI” utilization in enterprises, the place staff more and more depend on AI instruments with out correct safety oversight.
The attackers’ use of established platforms makes detection considerably tougher for conventional safety measures.
Mitigations
Safety specialists suggest a number of protecting measures:
Implementing multi-factor authentication on all vital providers
Coaching staff to fastidiously deal with password-protected attachments
Monitoring all AI platform utilization, together with unauthorized purposes
Sustaining steady inspection of AI site visitors relatively than implicitly trusting it
Deploying superior menace detection capabilities that may establish suspicious habits patterns
The assault serves as a wake-up name for organizations to reassess their method to AI platform safety, treating AI site visitors with the identical scrutiny utilized to unknown domains whereas balancing safety wants with enterprise innovation necessities.
Discover this Story Fascinating! Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates.