A classy cyber marketing campaign is focusing on macOS customers by distributing the potent “Odyssey” data stealer by way of a misleading web site impersonating the official Microsoft Groups obtain web page.
The assault, recognized by researchers at CloudSEK’s TRIAD, leverages a social engineering approach generally known as a “Clickfix” assault to trick victims into executing malicious code that systematically harvests delicate knowledge, establishes long-term persistence, and even replaces official cryptocurrency functions with trojanized variations.
This marketing campaign represents a tactical evolution from an analogous assault reported by Forcepoint in early August 2025, the place risk actors used a faux TradingView web site to ship the identical malware.
By shifting their lure to a trusted enterprise software like Microsoft Groups, the attackers are widening their internet to ensnare a broader vary of victims.
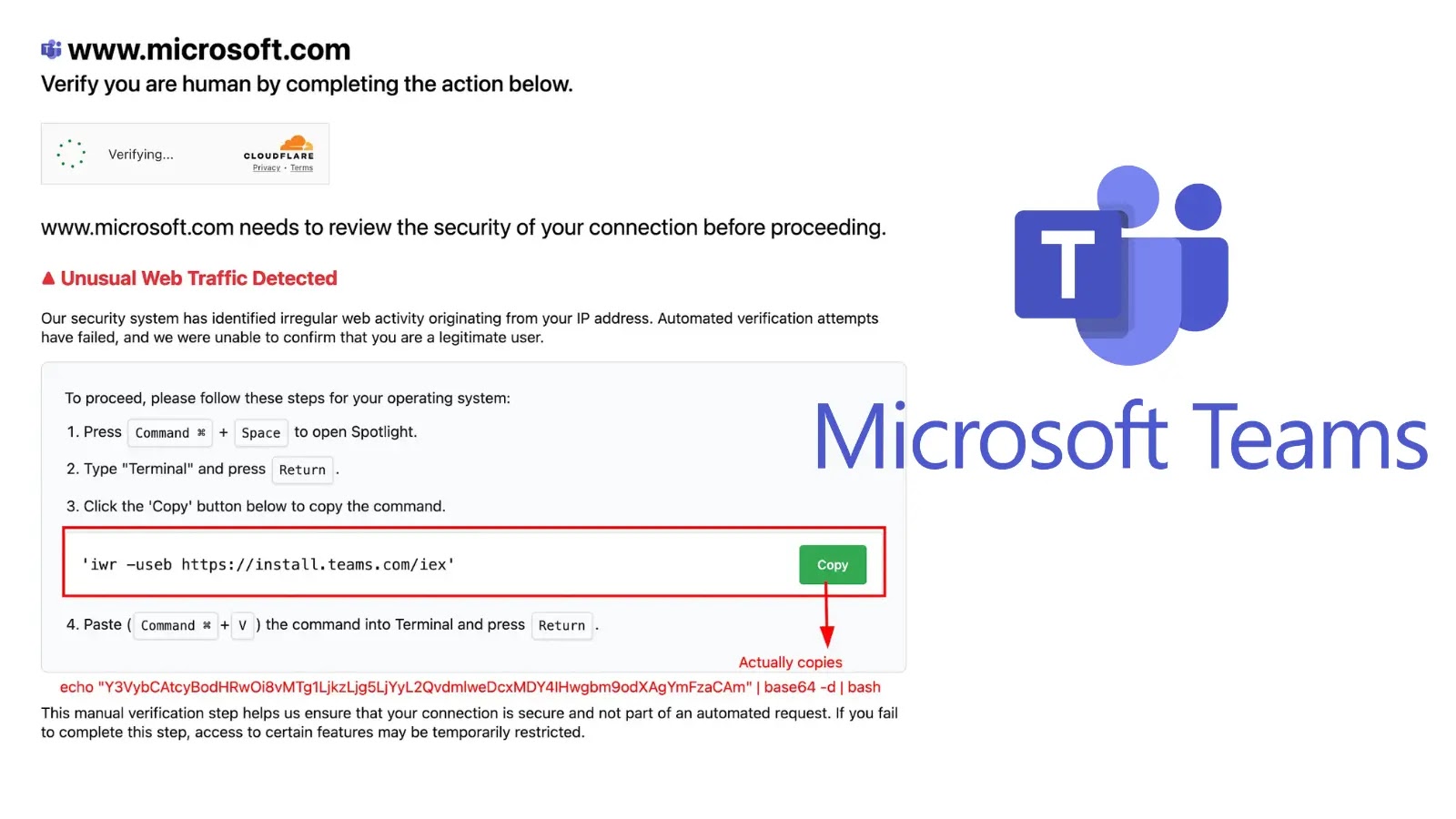
The assault begins when a person lands on a fraudulent webpage designed to appear to be a Microsoft safety verification web page for Groups. The web page instructs the person to resolve a supposed “Uncommon Internet Site visitors” problem by copying a command and pasting it into their macOS Terminal.
faux groups web site
Whereas the web page shows a seemingly innocent command, the “Copy” button truly locations a malicious, base64-encoded AppleScript payload onto the person’s clipboard. When an unsuspecting person executes this command, they unwittingly launch the Odyssey stealer.
Odyssey’s Malicious Payload
As soon as energetic, the malware initiates a multi-stage course of to compromise the system completely:
Credential Theft: The script first makes an attempt to achieve the person’s password by presenting a faux dialog field that reads, “Required Software Helper. Please enter machine password to proceed.” It relentlessly prompts the person till the right password is supplied. This password is then used to entry and steal the macOS login keychain and the Chrome browser’s keychain.
Widespread Knowledge Assortment: Odyssey conducts a complete sweep of the contaminated machine, accumulating an unlimited array of private and monetary data. This contains:
Apple Ecosystem: It extracts the whole Apple Notes database, together with attachments, together with Safari browser knowledge like cookies and saved type values.
Browser Artifacts: The malware targets Chromium-based browsers (Chrome, Edge, Courageous, Opera) and Firefox-based browsers, stealing cookies, internet knowledge, and saved logins. It additionally particularly hunts for knowledge from a protracted listing of browser extensions, specializing in password managers and crypto wallets like MetaMask.
Cryptocurrency Wallets: It recursively copies knowledge from quite a few desktop cryptocurrency wallets, together with Electrum, Exodus, Atomic, Wasabi, Ledger Stay, and Trezor Suite.
Private Information: The stealer searches the person’s Desktop and Paperwork folders for information with extensions like .txt, .pdf, .doc, .pockets, and .key, bundling as much as 10MB of those information for exfiltration.
Exfiltration: All harvested knowledge is compressed right into a single archive file named out.zip in a short lived listing. This file is then despatched to a command-and-control (C2) server positioned on the IP deal with 185.93.89.62. The identical server hosts the login panel for the Odyssey stealer toolkit.
Malware login web page
Persistence and Tampering: To make sure long-term entry, Odyssey creates a LaunchDaemon, a service that runs mechanically at startup. Utilizing the beforehand stolen password for administrator privileges, it installs this backdoor. In a very brazen transfer, the malware kills the official Ledger Stay software course of, deletes the app, and replaces it with a trojanized model downloaded from the C2 server, giving attackers direct management over the person’s crypto {hardware} pockets interactions.
Mitigations
The implications for victims are extreme, starting from credential theft and knowledge breaches to vital monetary losses from compromised cryptocurrency wallets. The persistence mechanism implies that even after a one-time knowledge theft, the system stays compromised and weak to additional assaults.
To defend in opposition to this risk, safety specialists advocate the next measures:
Community Monitoring: Block site visitors to the identified C2 IP deal with (185.93.89[.]62) and monitor for uncommon outbound POST requests containing massive zip information.
Endpoint Safety: Commonly audit /Library/LaunchDaemons/ for suspicious information and search for current, sudden osascript executions.
Consumer Vigilance: Train excessive warning when web sites request that you just run instructions within the Terminal. Confirm the authenticity of obtain pages earlier than continuing.
Incident Response: If an an infection is suspected, instantly reset all vital passwords (Apple ID, electronic mail, banking, crypto wallets) from a clear system. Take away the trojanized Ledger Stay software and contemplate a full system wipe and rebuild to make sure full elimination of the malware.
Discover this Story Attention-grabbing! Comply with us on Google Information, LinkedIn, and X to Get Extra Instantaneous Updates.