This complete information supplies SOC analysts and MSSP groups with sensible menace looking strategies utilizing superior menace intelligence platforms. Fashionable menace actors constantly develop subtle evasion strategies, making conventional detection strategies inadequate for complete safety operations.
The methods outlined right here leverage behavioral indicators, MITRE ATT&CK framework integration, and superior question capabilities to determine rising threats, cut back imply time to response (MTTR), and improve incident response effectiveness throughout numerous menace landscapes.
Efficient menace looking begins with understanding subtle question syntax that helps over 40 parameters for extremely particular and contextualized searches.
The fundamental construction usually features a parameter, a colon, and a worth, usually enclosed in citation marks. Logical operators play an important position in establishing efficient queries, the place the AND operator requires each circumstances to be true, the OR operator requires not less than one situation to be happy, and the NOT operator excludes outcomes that match particular circumstances.
Wildcards and particular characters improve question flexibility considerably. The asterisk (*) represents any variety of characters, the query mark (?) represents a single character, the caret (^) matches the start of a string, and the greenback signal ($) matches the tip of a string.
These parts allow analysts to create exact searches throughout file properties, course of actions, community communications, registry operations, and menace classifications.
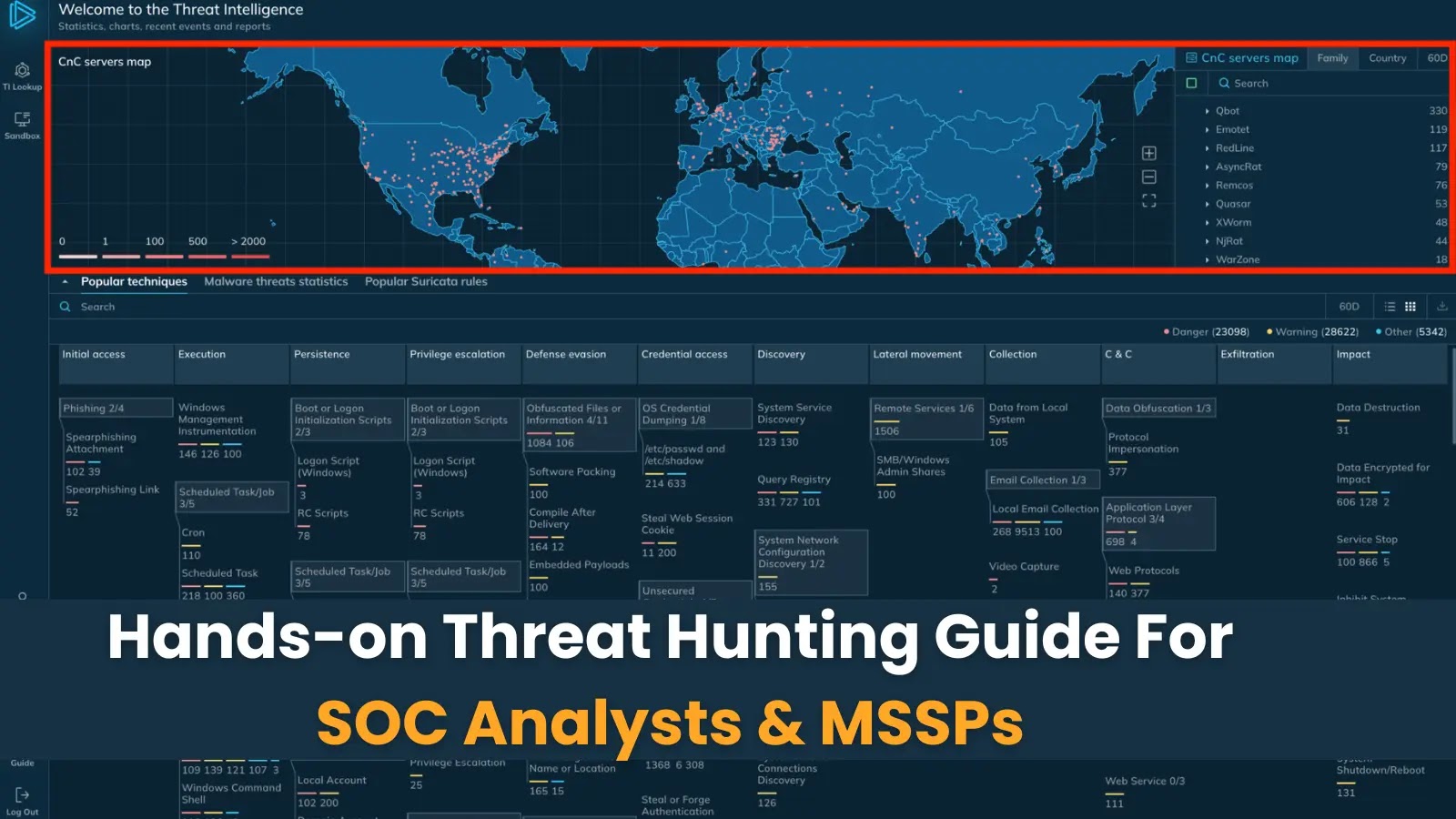
Utilizing Risk Intelligence Lookup companies corresponding to ANY.RUN focuses on a search engine that gives entry to an unlimited malware database, constantly up to date by over 500,000 customers of the Interactive Sandbox, together with 15,000 company SOC groups.
The platform’s subtle question syntax helps over 40 parameters, enabling extremely particular and contextualized searches that may ship tons of of related evaluation periods, malware samples, or indicators for additional analysis.
The service extends past conventional indicators of compromise (IOCs) to incorporate behavioral lookups, MITRE ATT&CK framework integration, file correlation capabilities, and YARA-based menace looking.
This complete strategy permits analysts to look primarily based on varied indicators, together with IP addresses, file hashes, URLs, domains, registry modifications, course of actions, and community communications.
ANY.RUN’s Risk Intelligence Lookup affords six core capabilities that allow complete menace looking and evaluation:
IOC Lookups facilitate detailed investigations of conventional compromise indicators, together with IP addresses, cryptographic hashes (MD5, SHA-1, SHA-256), domains, and URLs, offering foundational menace identification capabilities.
Behavioral Lookups lengthen past static indicators by analyzing system actions corresponding to registry modifications, course of executions, community communications, and mutex creations, which proves notably efficient for detecting novel threats missing established signatures or fileless assaults leveraging living-off-the-land strategies.
MITRE Methods Detection perform integrates the ATT&CK framework, enabling structured trying to find particular adversary techniques, strategies, and procedures (TTPs) via parameterized searches that map to documented assault sequences.
File/Occasion Correlation capabilities determine relationships between disparate assault elements, revealing complete menace chains by linking artifacts like mutex creations, registry modifications, and community communications throughout evaluation periods.
YARA-based Risk Searching introduces programmatic detection via binary sample matching, permitting identification of malware variants sharing core codebases regardless of obfuscation or model variations with out requiring prior indicator information.
Wildcards and Logical Operators allow complicated question building via asterisks for multi-character matching, query marks for single-character substitution, and Boolean logic (AND/OR/NOT) with grouping parentheses for exact menace speculation testing1. These capabilities collectively rework uncooked evaluation information into actionable intelligence by combining conventional IOC matching with behavioral evaluation and framework-aware detection methodologies.
Geographic Risk Evaluation
Nation-based menace detection represents a elementary approach for understanding regional menace landscapes and figuring out geopolitically motivated assaults. By using the submissionCountry parameter mixed with different indicators, analysts can successfully determine particular assault campaigns concentrating on specific areas.
For instance, concentrating on phishing assaults from Brazil requires combining geographic and menace classification parameters: submissionCountry:”br” AND threatName:”phishing”.
Geographic Risk Evaluation
This geographic strategy turns into notably invaluable when analyzing subtle assaults that leverage official system instruments. Figuring out malicious submissions from India involving PowerShell instructions might be completed via: submissionCountry:”in” AND commandLine:”powershell” AND threatLevel:”malicious”.
Such queries assist safety groups perceive how attackers adapt their strategies primarily based on regional traits and infrastructure.
MITRE ATT&CK Framework Integration
The incorporation of the MITRE ATT&CK framework permits analysts to seek for particular techniques, strategies, and procedures utilized by menace actors, facilitating a extra structured strategy to menace looking.
Command and script execution (T1059), probably the most frequent strategies, might be recognized via queries concentrating on PowerShell utilization or HTML Utility Host execution: MITRE:”T1059″ AND (commandLine:”powershell” OR imagePath:”mshta.exe”).
MITRE ATT&CK Framework Integration
Registry-based persistence (T1547) represents one other crucial approach, the place malware modifies the Home windows Registry to keep up system entry. Analysts can determine such actions by trying to find modifications to the Run key: MITRE:”T1547″ AND registryKey:”CurrentVersionRun”.
Superior correlation strategies contain combining a number of MITRE strategies to determine subtle assault patterns that make use of course of injection, persistence mechanisms, and system data discovery concurrently.
Detecting Obfuscated File Behaviors
Malware authors ceaselessly make use of obfuscation strategies to cover malicious code and evade evaluation. Figuring out executables in non-standard directories represents a typical evasion approach that may be detected via cautious question building.
By trying to find executable information outdoors normal Home windows directories, analysts can determine probably suspicious actions: fileExtension:”exe” AND NOT filePath:”Home windows*” AND NOT filePath:”Program Recordsdata*”.
Detecting Obfuscated File Behaviors
Script-based obfuscation presents one other problem, notably when JavaScript information execute PowerShell instructions in multi-stage assaults. The question commandLine:”powershell” and fileExtension:”js” successfully identifies such obfuscation makes an attempt.
This strategy helps analysts perceive how attackers layer completely different applied sciences to realize their goals whereas avoiding detection.
Persistence Mechanisms
Understanding persistence mechanisms and mutex creation patterns supplies insights into malware habits and helps determine particular menace households.
Persistence Mechanisms
Mutex objects, utilized by malware to make sure single-instance execution, might be investigated via synchronization object parameters. As an example, trying to find the “rmc” mutex reveals connections to the Remcos trojan: syncObjectName:”rmc”.
Area Era Algorithm Detection
Area Era Algorithms (DGAs) characterize subtle evasion strategies the place malware dynamically generates domains for command and management communication.
Figuring out DGA-based malware requires specializing in area traits and communication patterns1. Focusing on unusual top-level domains with energetic communication can reveal DGA exercise: domainName:”.high” OR domainName:”.xyz” AND (destinationPort:”80″ OR destinationPort:”443″) AND threatLevel:”malicious”.
Area Era Algorithm Detection
Fashionable attackers more and more abuse official companies like Cloudflare Employees for internet hosting malicious content material. Analysts can determine such abuse via focused searches: domainName:”.employees.dev” AND threatLevel:”malicious”. This strategy has confirmed efficient in figuring out tons of of phishing domains hosted on official infrastructure.
Superior menace looking via subtle question capabilities permits SOC analysts and MSSP groups to detect, prioritize, and include threats extra successfully.
The mixing of geographic evaluation, MITRE ATT&CK framework strategies, behavioral sample recognition, and chronic monitoring creates complete protection methods.
By leveraging these methodologies, safety groups can considerably cut back response instances, improve alert triage with contextual insights, and speed up menace detection and containment capabilities throughout numerous menace landscapes.
Are you from SOC/DFIR Groups! – Work together with malware within the sandbox and discover associated IOCs. – Request 14-day free trial