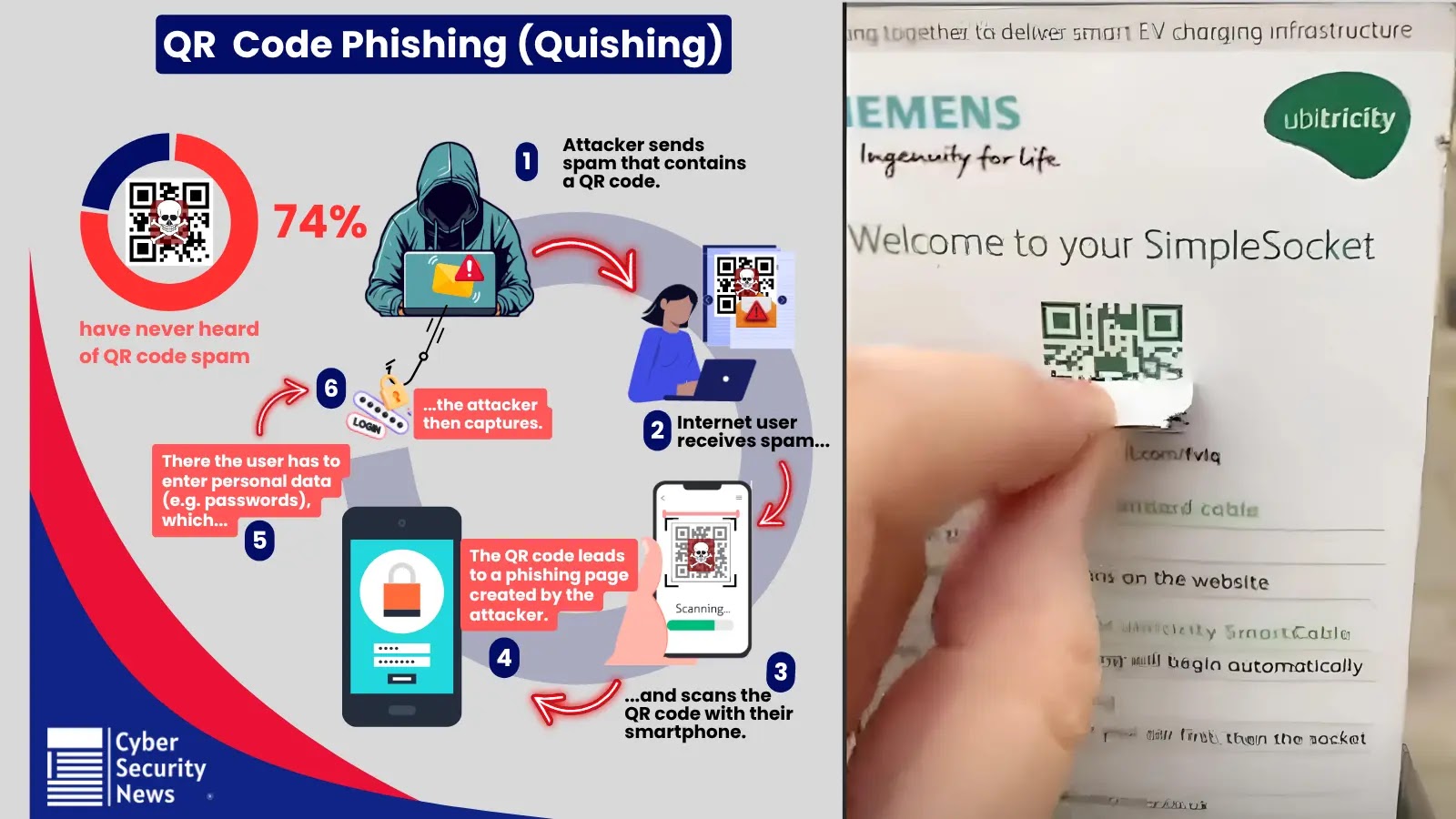
QR codes was once innocent, now they’re one of many sneakiest methods attackers slip previous defenses. Quishing, or QR code phishing, hides malicious hyperlinks inside innocent-looking photographs that filters can’t learn.
One scan, and the sufferer lands on a faux login web page designed to steal credentials or set off a obtain; usually from a cellular machine utterly outdoors your SOC’s visibility.
Why Quishing Is Exhausting to Catch
From a detection standpoint, Quishing breaks the standard guidelines. The phishing payload isn’t within the e-mail physique or attachment, it’s embedded inside a picture as a QR code. Meaning:
No clickable hyperlinks for safe e-mail gateways or URL filters to analyze.
No apparent indicators for content material inspection or heuristic engines.
No telemetry as soon as the consumer scans the code on a cellular machine outdoors the company community.
Analyst’s New Weapon: Expose QR Phishing in Seconds
For SOC analysts, Quishing is a time sink and a blind spot. Conventional instruments can’t scan QR codes and decoding them manually is gradual and dangerous.
That’s why many groups now depend on interactive sandboxes like ANY.RUN to securely expose what’s hidden behind these codes with out leaving the protected setting.
As an alternative of extracting photographs or utilizing exterior decoders, the sandbox mechanically detects and decodes QR codes from emails, PDFs, and screenshots.
It follows the ensuing hyperlink in an remoted VM, giving analysts the complete assault context, from payload supply to community exercise, in simply seconds.
Actual-World Instance: Voicemail Rip-off Uncovered in Underneath 60 Seconds
An e-mail arrives claiming you’ve missed a voicemail. As an alternative of a hyperlink, it comprises a QR code urging the consumer to “hearken to the message.”
Verify how sandbox exposes the hidden QR code
ANY.RUN sandbox exposing the malicious URL in seconds
As soon as uploaded to ANY.RUN, the sandbox mechanically detects and decodes the QR with out handbook extraction or third-party instruments.
Reveal complicated threats in seconds inside ANY.RUN’s interactive sandbox, reducing investigation time and turning hidden assaults into clear proof -> Be part of ANY.RUN now
The decoded URL is displayed instantly within the Static Discovering part, and automatic interactivity triggers a managed browser session.
Malicious URL found within the Static discovering part inside ANY.RUN sandbox
In 60 seconds, the sandbox found the complete assault chain, surfacing related TTPs, exportable IOCs, community connections, and a shareable evaluation report analysts can use to dam, hunt, and write detections.
Properly-structured report generated by ANY.RUN for straightforward sharing
Why SOC Analysts Select ANY.RUN for Quishing Evaluation
Quishing assaults are constructed to waste analyst time; ANY.RUN offers that point again. With automated QR detection, real-time interplay, and deep visibility, analysts can shift from handbook decoding to instantaneous validation.
90% of assaults uncovered in underneath 60 seconds: The sandbox reveals hidden payloads, redirect chains, and credential-harvesting pages in seconds, reducing common triage time by greater than half.
Full visibility in a single interface: Analysts see course of bushes, community site visitors, and decoded URLs collectively; no switching between instruments, no danger of lacking a step.
Automated proof assortment: Each session generates IOCs, community indicators, and screenshots that may be exported or shared in a single click on.
Sooner detection engineering: Verified TTPs and IOCs will be was new detection guidelines instantly from the sandbox report.
Protected dealing with setting: QR codes, phishing pages, and scripts execute solely contained in the remoted VM, analysts keep absolutely protected whereas observing actual conduct.
Collaborative workflows: Share classes throughout the crew or combine together with your SIEM, SOAR, or ticketing system to speed up incident response.
Flip QR Phishing from a Blind Spot Right into a 60-Second Investigation
Quishing doesn’t solely check your defenses but in addition your effectivity. Analysts spend hours decoding photographs, validating hyperlinks, and correlating telemetry that ought to already be seen.
ANY.RUN adjustments that stability, giving SOCs the sort of context they will act on immediately.
With automation constructed into each stage of research, SOC groups utilizing ANY.RUN report measurable outcomes:
As much as 58% extra threats recognized general, together with people who bypass commonplace filters and static evaluation.
94% of customers report sooner triage, due to automated IOC assortment and ready-to-share stories.
95% of SOC groups velocity up investigations, connecting decoded URLs, community site visitors, and menace conduct in a single workflow.
Strive ANY.RUN to uncover hidden phishing payloads, decode QR assaults safely, and switch each investigation into actionable perception.