Phishing has moved far past suspicious hyperlinks. At present, attackers cover contained in the information workers belief most; PDFs. On the floor, they appear to be invoices, contracts, or reviews.
However as soon as opened, these paperwork can set off hidden scripts, redirect to faux login pages, or quietly steal credentials.
The hazard lies in how convincing they’re. PDFs usually slip previous filters, look clear to antivirus instruments, and don’t increase alarms till it’s too late. That’s why malicious PDFs have grow to be some of the efficient entry factors for attackers, and one of many hardest for analysts to identify early.
Why PDFs Turned a Hacker’s Favourite Weapon
From an attacker’s perspective, PDFs supply a novel mixture of belief and performance. They’re business-critical, exchanged day by day throughout industries, and supported by virtually each working system. That makes them a dependable supply car for each malware and phishing.
The dangers stem from a number of technical components:
Trusted format: Safety filters usually deal with PDFs as low-risk in comparison with executables.
Embedded performance: JavaScript, types, and hyperlinks present a number of entry factors for malicious code.
Exploitable software program: Adobe Reader and different viewers repeatedly face crucial vulnerabilities.
Cross-platform attain: The identical file can impression Home windows, macOS, Linux, or cell customers.
This implies a PDF isn’t “only a doc.” With out dynamic evaluation, dangerous behaviors, reminiscent of credential theft, persistence, or community connections, stays hidden till execution.
The Quickest Method to Detect Malicious PDFs
Static scans could verify a file is “clear,” however they don’t reveal what occurs as soon as it runs. That’s why analysts are adopting interactive sandboxes like ANY.RUN to check PDFs in a protected surroundings and watch all the assault unfold in actual time.
Suspicious PDF attachment analyzed inside ANY.RUN sandbox
Right here’s what it offers safety groups:
Quicker verdicts: Malicious habits is detected in below 60 seconds, slicing imply time to detect.
Context for choices: Not simply {that a} file is malicious, however the way it operates, which helps decide response actions.
Diminished handbook work: No must dig by means of obfuscated scripts or uncooked visitors logs.
Confidence in response: Analysts can hint each step of the assault, guaranteeing nothing is missed.
Actionable intelligence: IOCs are robotically extracted, mapped to MITRE ATT&CK, and prepared for SIEM/SOAR integration.
Detect malicious PDFs in seconds, minimize investigation time, and get prompt IOCs with interactive sandbox.Strive ANY.RUN now
Actual Case: A Harmful PDF That Seems to be Legit
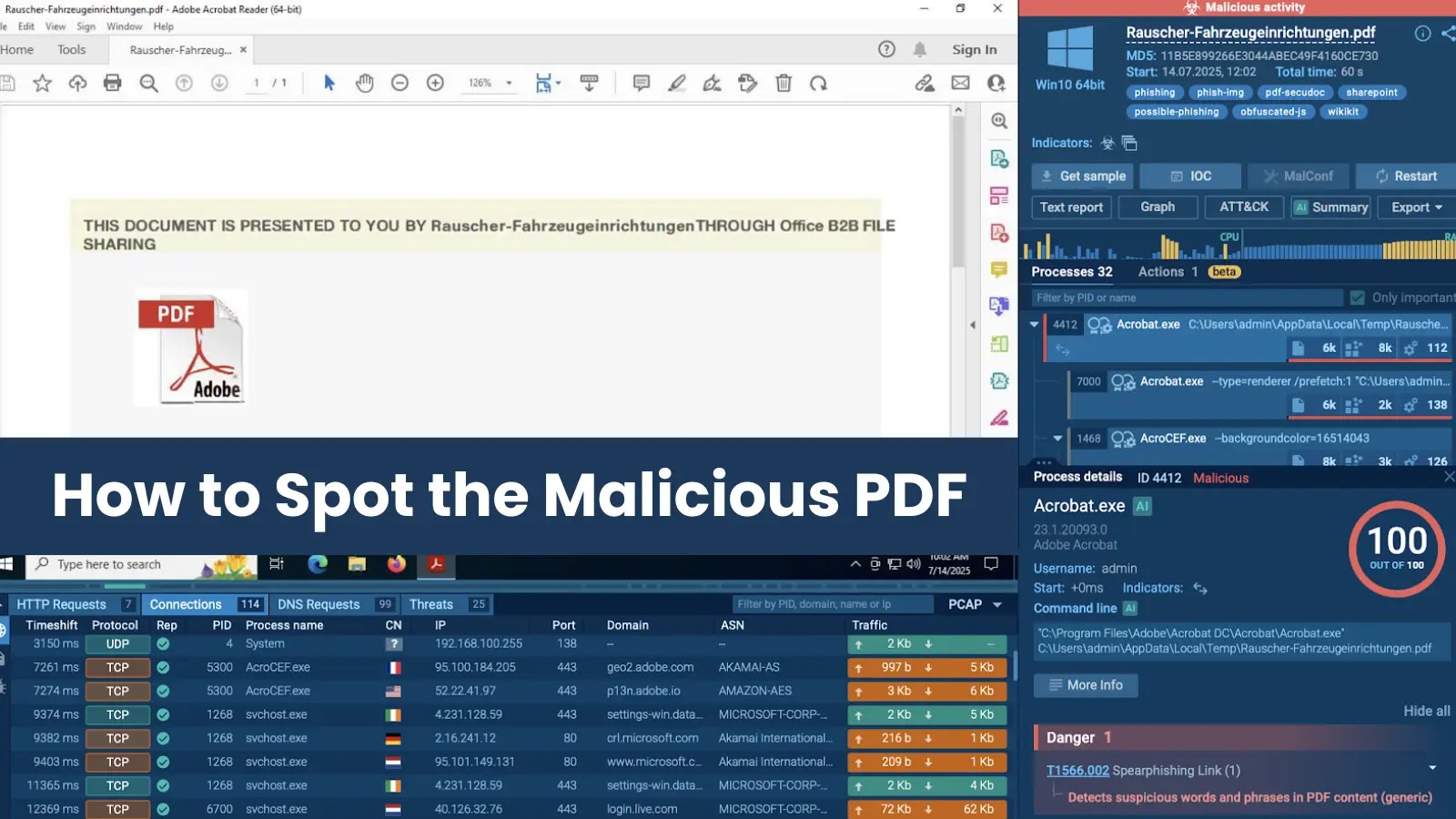
In an ANY.RUN sandbox session, a suspicious file named Rauscher-Fahrzeugeinrichtungen.pdf was detonated. Inside simply 60 seconds, the evaluation marked the exercise as malicious, leaving little doubt concerning the verdict.
View malicious PDF file inside sandbox
Quick verdict of malicious processes by ANY.RUN sandbox
The complete assault chain appeared within the course of tree. Every course of was mapped to ATT&CK methods, giving analysts clear visibility into execution, persistence, and credential theft makes an attempt.
Seeing the chain this fashion makes it simple to know the assault’s intent and resolve on the proper response.
Spearphishing hyperlink uncovered inside ANY.RUN’s interactive sandbox
The sandbox additionally displayed the faux Microsoft login web page used to steal credentials, exhibiting precisely what the sufferer would see.
For analysts, this makes the chance immediately clear with out digging by means of code and helps talk the menace to non-technical groups or administration.
Pretend Microsoft web page seems because of phishing assault with PDF attachment
All related IOCs, domains, IPs, and file hashes, have been robotically collected in a single place, able to feed into SIEM or SOAR instruments. This protects analysts time on handbook extraction and ensures sooner blocking of comparable threats.
Related IOCs extracted by ANY.RUN sandbox
Lastly, the session might be exported as a structured report with timelines, tags, and behavioral particulars. That makes it easy to transient managers, assist compliance wants, or share outcomes with shoppers with out additional work.
Nicely-structured report generated by ANY.RUN sandbox
What appeared like a routine PDF turned out to be a credential-stealing phishing marketing campaign, absolutely uncovered in seconds.
Cease PDF Threats Earlier than They Unfold
Malicious PDFs are one of many best methods attackers break into organizations, but in addition one of many quickest to show with the proper instruments.
With ANY.RUN’s interactive sandbox, analysts can detect threats in seconds, minimize investigation time, and provides companies the boldness that phishing makes an attempt are stopped earlier than injury happens.
Strive ANY.RUN right now and see how briskly actual threats are uncovered in a protected surroundings