Phishing assaults are evolving quickly, permitting cybercriminals to bypass conventional safety methods like e mail filters and static defenses. Because of this, many companies are left weak to credential theft, typically with out realizing the risk till it’s too late. Early detection is essential, and real-time evaluation of suspicious emails, hyperlinks, and recordsdata in a safe atmosphere provides the answer.
Let’s discover how companies can keep forward of those threats and forestall credential theft with superior phishing detection methods, utilizing interactive sandboxes like ANY.RUN.
Why Companies Turned to Sandboxes for Early Phishing Detection
As phishing assaults grew extra superior, conventional safety methods simply couldn’t sustain. Companies shortly realized they wanted a greater solution to catch these threats earlier than they induced harm. That’s when sandboxes grew to become the game-changer:
Actual-time detection: Sandboxes permit companies to see precisely how threats behave in a managed atmosphere.
Secure testing: Suspicious emails and recordsdata can be analyzed with out placing the corporate community in danger.
Fast motion: Sandboxes make it simpler to identify threats quick, serving to groups reply earlier than something severe occurs.
By providing real-time, hands-on evaluation, sandboxes give companies the instruments they should keep one step forward of evolving phishing assaults.
Seeing the Full Assault Unfold
A significant good thing about sandboxes is the power to observe your entire assault unfold in real-time. Companies can monitor the complete assault chain, from the phishing e mail to the ultimate malicious motion.
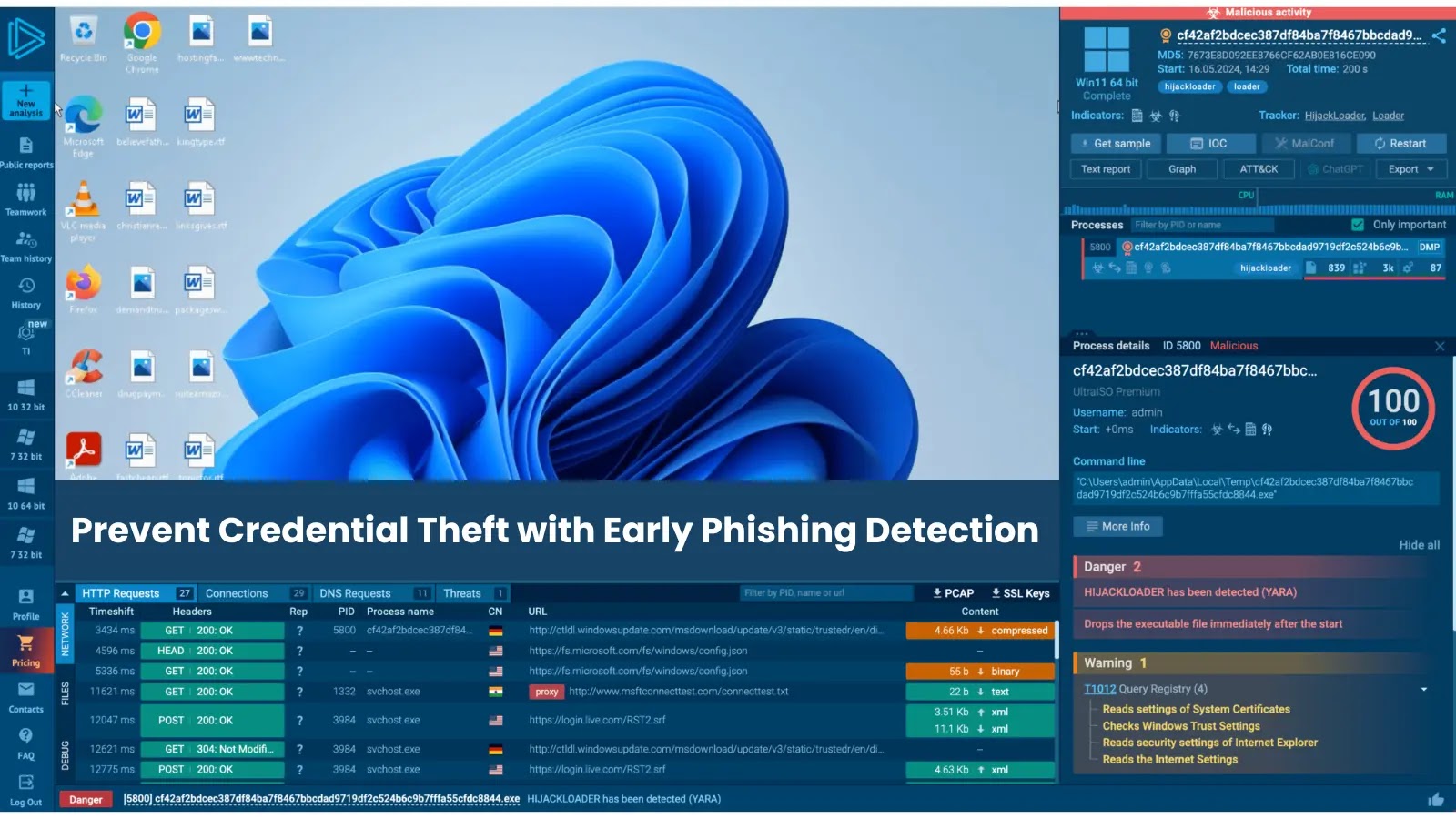
For instance, right here’s a phishing assault analyzed inside an ANY.RUN sandbox: we will see every little thing, how the phishing e mail triggers the assault, the malicious conduct it results in, and the ultimate verdict that the actions are dangerous.
View evaluation session
Phishing assault analyzed inside ANY.RUN sandbox
Why that is good for companies:
Full visibility: It’s not nearly recognizing a suspicious e mail; you may see your entire assault lifecycle.
Correct risk identification: By following the assault’s steps, companies may be sure about its nature and impression.
Higher preparedness: Understanding the complete sequence helps companies practice their groups and refine their defenses towards related assaults sooner or later.
Quicker decision-making: With all the small print at hand, safety groups could make extra knowledgeable, faster selections in regards to the risk’s severity.
Expertise quicker, extra correct phishing detection and enhanced safety for your small business with ANY.RUN’s real-time sandbox analysis-> Attempt ANY.RUN now
Simplifying Risk Evaluation for All Talent Ranges
ANY.RUN’s sandbox makes phishing detection simpler for safety groups of all expertise ranges, together with junior analysts. For example, Detonation Actions present useful hints to maintain the evaluation transferring ahead. If the evaluation stalls, analysts can merely check with this part for steering on what to do subsequent, like opening an e mail attachment or clicking on a suspicious hyperlink.
These hints assist analysts keep away from getting caught and make sure the evaluation progresses easily. Even junior analysts, with out intensive expertise, can observe these cues to grasp the risk and hold the method transferring.
No extra sticking factors: Analysts can depend on the Detonation Actions to maneuver ahead, even when they’re uncertain.
Quicker evaluation: The step-by-step steering ensures that evaluation doesn’t get delayed.
Accessible for junior analysts: With clear directions, even junior workers can contribute successfully with no need superior experience.
Along with Detonation Actions, ANY.RUN’s AI Assistant additional simplifies risk evaluation, making it even simpler for junior analysts to deal with phishing makes an attempt.
The AI Assistant supplies real-time help by providing automated summaries and clear explanations of the processes, breaking down advanced knowledge into simply digestible data.
ANY.RUN’s AI Assistant offering the abstract of the assault
Automating the Course of for Quicker, Smarter Detection
ANY.RUN’s Automated Interactivity function takes phishing detection to the subsequent degree by automating the processes. By enabling this function, companies can streamline their evaluation workflow and get verdicts on the risk degree of emails shortly.
QR code uncovered and analyzed inside ANY.RUN sandbox
For instance, within the evaluation session talked about earlier, the sandbox mechanically opens a hidden hyperlink inside a PDF’s QR code, accesses the hyperlink in a browser, verifies the CAPTCHA, and results in a faux Microsoft login web page; all in a few minute.
Pretend Microsoft login web page used to steal account credentials
This fast-paced automation mimics the whole assault chain, making certain that each essential step is caught at once.
How this advantages companies:
Quicker detection: Automation permits for fast, real-time evaluation of threats, minimizing response instances.
Much less guide work: Automated interactivity reduces the necessity for guide intervention, releasing up analysts to concentrate on extra advanced duties.
Elevated effectivity: With automation dealing with routine duties, SOC groups can deal with a better quantity of threats with out extra sources.
Automation helps companies reply swiftly to phishing makes an attempt, lowering the workload for analysts and enabling simpler risk administration.
Improve Your Cybersecurity Technique with Quicker Phishing Detection
As phishing assaults develop extra subtle, companies have to act quicker and smarter to remain forward. Sandboxes like ANY.RUN provide real-time evaluation, full assault visibility, and instruments that empower safety groups, no matter expertise degree, to detect and reply to threats extra effectively. With automation and AI help, companies can scale their safety efforts with out sacrificing accuracy or velocity.
Defend your small business earlier than it’s too late.
Attempt ANY.RUN for 14 days and expertise proactive, real-time phishing detection at the moment.