Attackers have leveled up. Powered by AI and professional-grade toolkits, at present’s social engineering scams are almost unattainable to inform other than the actual factor, and automatic defenses hardly ever catch them.
That’s the actual problem for safety leaders: these threats solely reveal themselves as soon as a person clicks, solves a CAPTCHA, or follows a “verification” step.
Nevertheless, many companies have discovered methods to uncover these assaults earlier, by utilizing interactive sandboxing and different proactive defenses that expose the total assault chain earlier than it ever reaches staff.
Let’s see how.
Why Social Engineering Is Now a Enterprise Threat
Social engineering has advanced into one of the crucial damaging threats for firms, not due to the malware itself, however as a result of it exploits individuals and belief.
Information theft: Buyer information, monetary knowledge, and mental property will be stolen in minutes.
Monetary loss: Assaults typically result in wire fraud, ransom calls for, or regulatory fines.
Downtime: Compromised techniques can halt operations, affecting income and repair supply.
Fame harm: Prospects lose belief rapidly when an organization falls sufferer to a preventable rip-off.
Larger SOC strain: Investigations devour helpful analyst hours and escalate response prices.
The true threat right here is how lengthy these threats go undetected and the way a lot harm is completed earlier than the SOC can reply.
ClickFix: The New Face of Social Engineering
One of the crucial widespread strategies attackers now depend on is ClickFix. As a substitute of dropping malware instantly, it hides behind regular person actions, like fixing a CAPTCHA or clicking a reserving affirmation. The true hazard begins solely after the sufferer follows the directions.
That makes ClickFix extraordinarily efficient. Since there’s no malicious exercise till a human interacts, conventional filters and automatic scanners see nothing mistaken. By the point the malware is triggered, it’s typically too late.
The excellent news is that many firms have already closed this hole by adopting interactive sandboxing. With options like ANY.RUN, SOC groups can detonate suspicious information and hyperlinks safely, work together with them as a person would, and reveal the whole assault chain, from pretend pages to hidden PowerShell instructions and remaining payloads.
This implies even junior analysts can detect superior strategies like ClickFix early, export indicators of compromise, and block the assault earlier than it ever reaches staff.
Test Full Assault with ClickFix Tactic
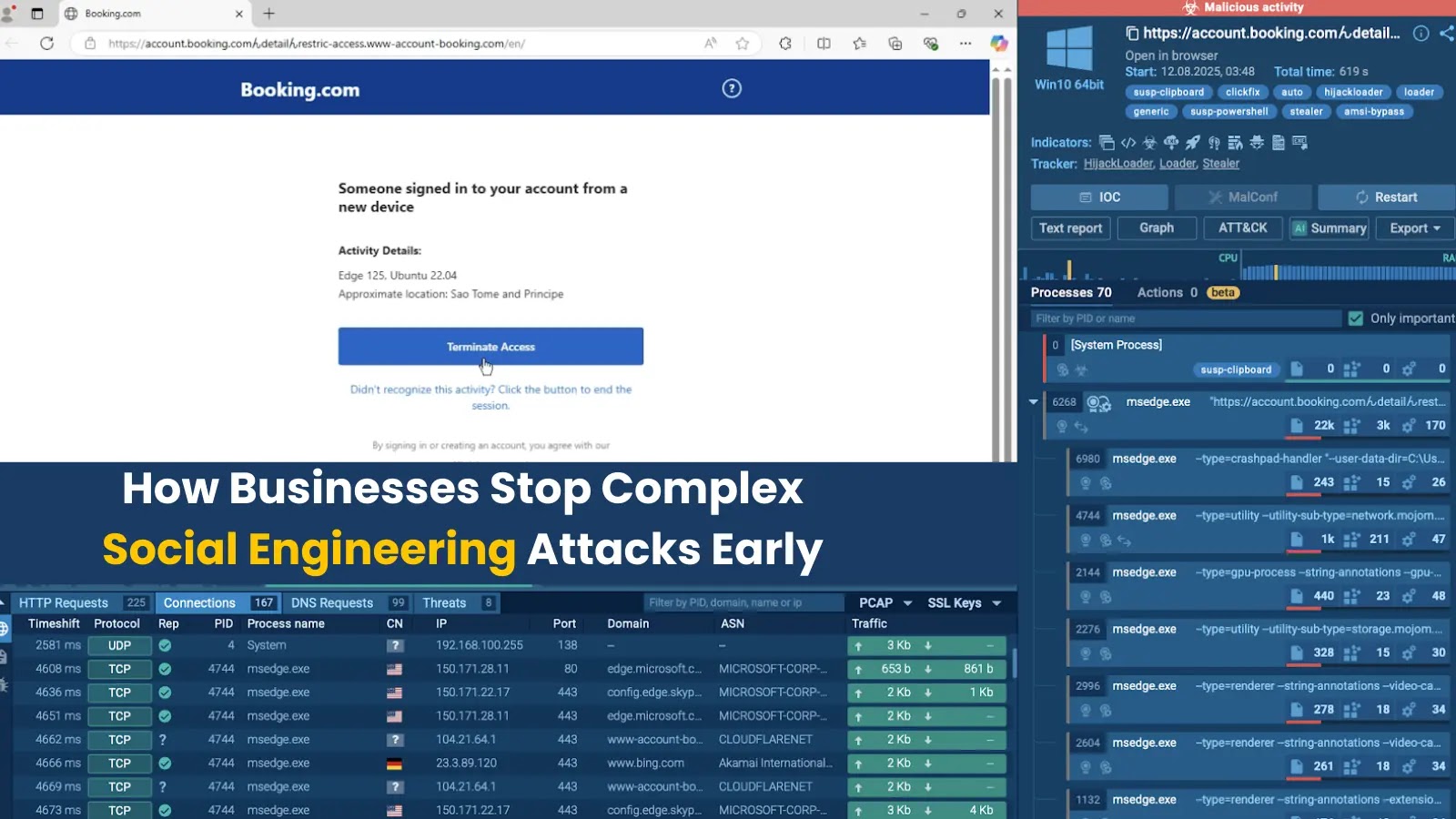
Pretend reserving web page used to lure potential victims, uncovered inside ANY.RUN sandbox
On this case, attackers used a pretend Reserving.com web page to lure victims (see screenshot above, captured in ANY.RUN sandbox). The web page appeared professional and warned a few suspicious login try, prompting the person to “terminate entry.”
Give your staff a protected surroundings to uncover difficult assaults in actual time, earlier than one click on turns right into a full breach -> Attempt ANY.RUN now
Subsequent, the sufferer was requested to show they’re human by fixing a CAPTCHA. The directions advised them to open the Home windows Run utility and paste a command, copied silently to the clipboard, into the dialog field.
Verification steps used to begin extra malicious payload
As soon as executed, this command launched a hidden an infection chain. Behind the scenes, malicious processes ran and ended with the deployment of Hijackloader, a modular loader designed to tug in extra payloads and set up persistence.
ANY.RUN evaluation revealed the malicious behaviors and related MITRE ATT&CK TTPs, together with course of creation, registry queries, and system info discovery.
Hijackloader found with the assistance of ANY.RUN sandbox evaluation
With out detonation inside a protected, interactive surroundings, these steps would stay invisible to conventional defenses, making sandboxing important for early detection.
Expose Tough Social Engineering Assaults Earlier than They Hit
Due to ANY.RUN’s interactive sandbox, companies can expose even essentially the most misleading social engineering techniques in a protected surroundings. By analyzing threats interactively, the sandbox makes it doable to see each step of the assault, earlier than staff ever encounter it.
Scale back Imply Time to Detect (MTTD): Spot threats sooner by triggering hidden behaviors in minutes, not days.
Reduce investigation time: Automated course of mapping and IOCs cut back handbook work, liberating senior analysts to deal with strategic duties.
Empower junior analysts: With a beginner-friendly interface and interactive workflows, even less-experienced workers can analyze superior threats like ClickFix.
Increase SOC effectivity: Extra threats resolved on the first line means fewer escalations and decrease general prices.
As a substitute of reacting after an incident, companies can proactively uncover assaults, include them early, and strengthen defenses for the longer term.
Begin your 14-day trial of ANY.RUN and provides your staff the instruments to cease advanced social engineering assaults earlier than they develop into a breach.