August 2025 has marked a big evolution in cybercrime ways, with menace actors deploying more and more refined phishing frameworks and social engineering strategies which can be efficiently bypassing conventional safety defenses.
Safety researchers at ANY.RUN has recognized three main marketing campaign households that symbolize a elementary shift in how cybercriminals method credential theft and system compromise: the multi-stage Tycoon2FA phishing framework, ClickFix-delivered Rhadamanthys stealer operations, and the emergence of Salty2FA, a brand new Phishing-as-a-Service (PhaaS) platform linked to the infamous Storm-1575 group.
These campaigns reveal an alarming development towards extremely focused, multi-layered assaults that mix superior evasion strategies with psychological manipulation to defeat each automated safety programs and human vigilance.
Not like conventional mass phishing makes an attempt, these refined frameworks particularly goal high-value accounts in authorities, monetary, and demanding infrastructure sectors.
Tycoon2FA: Seven-Stage Phishing Chain
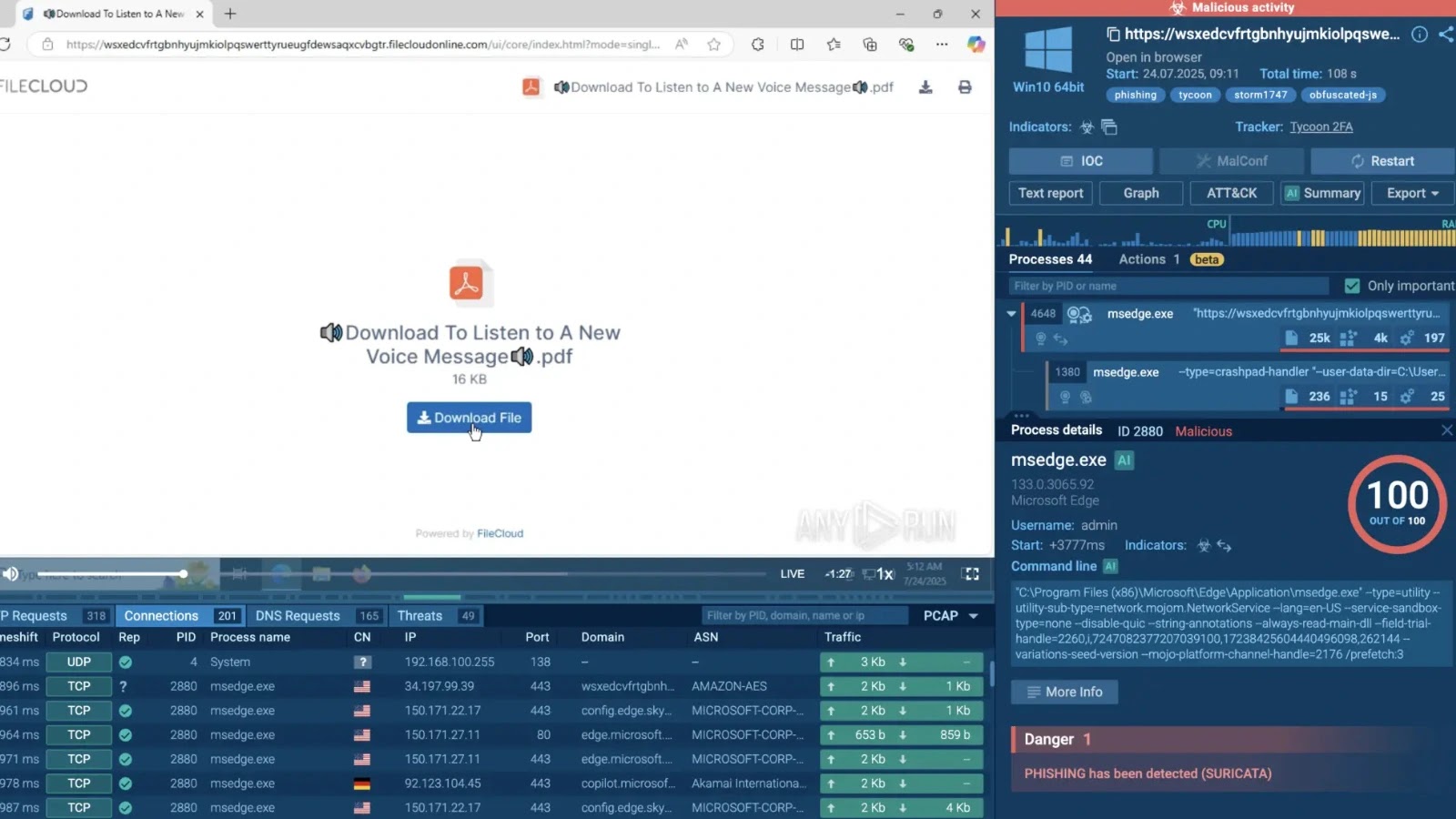
The Tycoon2FA marketing campaign represents a paradigm shift in phishing sophistication, using a seven-stage execution chain that systematically defeats automated safety instruments whereas exhausting human targets.
This framework has emerged as probably the most efficient credential harvesting operations noticed in 2025, particularly concentrating on authorities businesses, army installations, and main monetary establishments throughout america, the UK, Canada, and Europe.
The assault methodology begins with fastidiously crafted voicemail-themed phishing emails that provoke a posh redirection chain. Victims are guided by means of a number of validation screens, together with Cloudflare Turnstile CAPTCHAs and “press-and-hold” anti-bot checks, earlier than reaching the ultimate Microsoft login spoofing panel. Every stage serves twin functions: filtering out automated evaluation instruments whereas constructing psychological dedication from human targets.
Tycoon2FA seven-stage phishing execution chain
Evaluation knowledge reveals that 26% of Tycoon2FA campaigns particularly goal banking sector workers, indicating deliberate concentrate on high-value monetary credentials quite than opportunistic credential harvesting.
The framework’s selectivity extends to authorities and army personnel, the place single compromised accounts can present entry to categorised programs and delicate nationwide safety info.
With ANY.RUN’s Automated Interactivity incorporates a seven-stage execution movement that operates as follows: preliminary phishing e mail supply, faux PDF attachment obtain, embedded hyperlink activation, Cloudflare CAPTCHA problem, guide interplay verification, e mail validation requirement, and at last, credential harvesting by means of spoofed authentication panels.
Phishing publicity by means of a misleading voice message obtain immediate.
This technique successfully defeats signature-based detection programs whereas requiring sustained human engagement that builds belief and reduces suspicion.
Establish cyber threats and empower SOC Efficiency with Chopping-edge Instruments => Get Began
ClickFix Evolution
The ClickFix method has developed considerably past its authentic NetSupport RAT and AsyncRAT supply mechanisms, now serving as a complicated vector for deploying superior info stealers like Rhadamanthys.
This evolution represents a regarding escalation in each technical complexity and evasion capabilities, combining social engineering psychology with superior malware deployment strategies.
Latest campaigns make the most of ClickFix flows to ship Rhadamanthys stealer by means of Microsoft Installer (MSI) packages that execute silently in reminiscence, bypassing conventional file-based detection programs with ANY.RUN Sandbox, we will see how the Rhadamanthys was delivered by way of ClickFix.
Rhadamanthys malware supply vector by way of ClickFix, illustrating the malicious code execution and payload extraction course of.
The assault chain employs anti-virtual machine checks to evade sandbox evaluation whereas establishing TLS connections on to IP addresses, circumventing DNS monitoring and area fame programs.
StageTechniqueMITRE ATT&CK IDEvasion MethodInitial DeliveryClickFix Social EngineeringT1566Human Interplay RequiredInstallationMSI Silent ExecutionT1218.007In-Reminiscence ProcessingEvasionAnti-VM DetectionT1497.001Environment AnalysisCommunicationDirect IP TLST1071.001DNS BypassPayload DeliveryPNG SteganographyT1027.003Visual Obfuscation
Essentially the most refined facet of those campaigns includes steganography-based payload supply by means of compromised PNG picture information.
Attackers embed extra malware parts inside picture knowledge, permitting secondary payload deployment whereas showing as reputable graphic content material to safety scanners. This method successfully bypasses content material inspection programs that concentrate on executable file varieties.
Risk actors have additionally carried out self-signed TLS certificates with intentionally mismatched Issuer/Topic fields, creating distinctive community artifacts whereas sustaining encrypted communication channels.
These certificates serve twin functions: avoiding industrial certificates authority oversight whereas offering distinctive looking signatures for superior menace detection groups.
Salty2FA: Subsequent-Technology PhaaS Framework
The invention of Salty2FA represents maybe probably the most important improvement in phishing infrastructure evolution, introducing a complete Phishing-as-a-Service platform able to bypassing nearly all present multi-factor authentication implementations.
First recognized in June 2025, this framework has quickly expanded to focus on Microsoft 365 accounts throughout a number of continents, with explicit concentrate on North American and European enterprise environments.
Salty2FA derives its title from distinctive supply code “salting” strategies that disrupt each static evaluation instruments and guide reverse engineering efforts.
The framework implements adversary-in-the-middle capabilities that may intercept push notifications from cell authentication functions, SMS-based one-time passwords, and even two-way voice authentication calls. This complete 2FA bypass functionality represents a elementary menace to present enterprise authentication methods.
Salty2FA phishing package execution chain
Infrastructure evaluation reveals constant patterns in Salty2FA deployment, using compound subdomain constructions paired with Russian top-level domains for command and management operations.
The framework makes use of chained server architectures, which give resilient communication channels however complicate attribution and takedown efforts.
Attribution proof suggests connections between Salty2FA and the Storm-1575 menace group, beforehand accountable for the Dadsec phishing package operations. Right here is the instance of an evaluation session, Salty2FA habits obtain, and an actionable report.
Phishing try concentrating on Microsoft login credentials.
Nevertheless, infrastructure overlaps additionally point out potential relationships with Storm-1747, the group behind Tycoon2FA campaigns. These connections counsel potential collaboration between beforehand distinct menace actors or evolution inside present felony organizations.
Monetary providers and insurance coverage organizations
Power manufacturing and manufacturing amenities
Healthcare programs and telecommunications suppliers
Authorities businesses, instructional establishments, and logistics networks
These marketing campaign developments symbolize a elementary shift in cybercriminal capabilities, shifting past opportunistic assaults towards sustained, focused operations towards high-value institutional targets.
The sophistication demonstrated in multi-stage evasion, superior steganography, and complete 2FA bypass strategies signifies important funding in analysis and improvement inside felony organizations.
Conventional safety approaches targeted on signature-based detection and static evaluation show insufficient towards these developed threats.
The mixture of human psychological manipulation with superior technical evasion creates assault vectors that require behavioral evaluation, interactive sandbox environments, and steady menace intelligence integration for efficient detection and response.
Organizations should implement layered safety methods that mix superior behavioral analytics, interactive malware evaluation capabilities, and complete menace intelligence integration.
The shift towards PhaaS fashions means that these refined strategies will change into more and more accessible to lower-skilled menace actors, thereby considerably increasing the general menace panorama.
Safety groups ought to prioritize the event of detection guidelines primarily based on behavioral indicators quite than static IOCs, as these campaigns reveal fast infrastructure turnover and evasion method evolution.
Combine ANY.RUN options to work together with malware within the sandbox => Begin Your Free Trial