If you’re in a SOC, pace is every little thing. The sooner you detect and ensure an intrusion, the quicker you may comprise it, and the much less injury it does to your group.
However uncooked indicators of compromise (IOCs) like hashes, IPs, or domains usually fall brief on their very own.
They elevate a flag, however with out context, analysts are left asking: What does this actually imply?
Enriched IOC Feeds shut that hole by including the lacking context and turning remoted knowledge factors into actionable intelligence.
The Limitations of Uncooked IOCs
Whereas IOCs are necessary for detection, counting on them of their uncooked type creates main hurdles for SOC groups:
Ambiguity: A single hash would possibly correspond to a number of recordsdata, making it troublesome to substantiate what’s really in play.
Brief lifespan: Domains and IPs usually rotate rapidly, leaving static indicators outdated by the point they’re noticed.
Lack of habits context: Uncooked knowledge doesn’t clarify how the risk behaves, strikes laterally, or persists inside a community.
Noise and false positives: With out enrichment, analysts spend hours chasing leads that transform irrelevant.
How Enriched IOC Feeds Clear up These Challenges
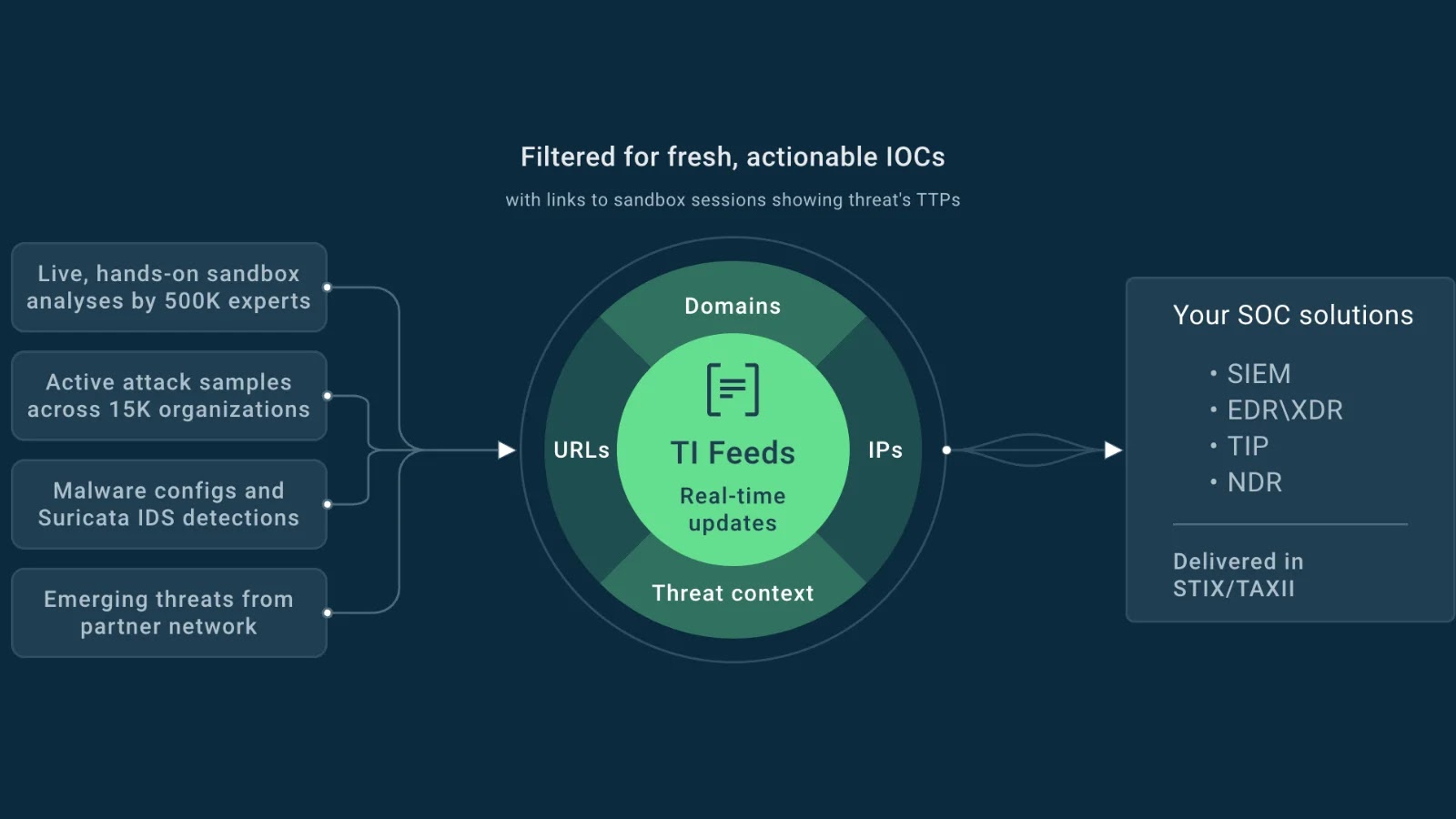
That is the place ANY.RUN’s Menace Intelligence Feeds stand out. As a substitute of offering static knowledge, they ship up-to-date indicators enriched with context from real-world malware exercise and sandbox classes.
That transforms a uncooked IOC right into a ready-to-use lead for each incident response and proactive searching.
ANY.RUN’s TI Feeds extracting actionable IOCs from distinctive sources
For instance, ANY.RUN’s Feed mechanically extracts the malware’s configuration and community site visitors, exposing C2 servers, registry modifications, persistence mechanisms, and extra.
All of this intelligence is linked right into a single execution chain, so analysts see the total image of TTPs as a substitute of chasing remoted IOCs.
Check out this sandbox session
ANY.RUN extracts contents of malware configs revealing precious indicators
This protects hours of handbook work: as a substitute of sewing collectively scattered proof, analysts can instantly pivot from an IOC within the feed to a whole sandbox session exhibiting how the assault unfolds step-by-step.
Equip your SOC to remain forward of threats -> Attempt TI Feeds
Key Benefits of Enriched IOC Feeds for SOC Groups
For SOC groups, the distinction between protecting tempo with threats and falling behind usually comes right down to the standard of intelligence at hand.
Uncooked IOCs elevate alerts, however with out context they drive analysts to spend hours validating what issues and what doesn’t.
Advantages of ANY.RUN’s TI Feeds for groups
Enriched IOC Feeds change that by offering the lacking behavioral element and scale SOC groups want to reply successfully.
Accelerated risk searching: Constantly up to date IOCs, enriched with sandbox context, assist analysts transfer past remoted alerts and rapidly uncover associated exercise throughout the atmosphere.
Proactive protection: As a substitute of reacting to yesterday’s assaults, SOCs can monitor how threats evolve in actual time and take preventive measures earlier than they strike.
Smarter triage and quicker response: With behavioral context tied to every IOC, analysts instantly see how a risk operates, permitting them to prioritize important incidents and minimize MTTR.
Lowered noise and false positives: Context-rich feeds reduce wasted effort by serving to SOCs focus solely on related, high-confidence indicators.
A Trusted Supply of Giant-Scale Intelligence
The power of any feed relies on the standard of its knowledge.
ANY.RUN’s Menace Intelligence Feeds are constructed on a basis of over 50 million threats within the database, with greater than 16,000 new samples added daily.
The info is contributed by a world group of 500,000 analysts and 15,000 firms, guaranteeing it displays the realities of energetic assaults throughout industries.
Feeds are refreshed each two hours, giving SOC groups a view of campaigns as they unfold, not after the very fact.
This fixed stream of present, real-world intelligence offers analysts the readability they should tune defenses, validate alerts, and hunt for threats with confidence.
Speed up Response and Menace Looking with IOC Feeds
Retaining your SIEM, XDR, and TIP updated with filtered malicious IPs, domains, and URLs is the distinction between chasing noise and catching actual threats.
Enriched IOC Feeds give SOC groups the context and protection they should reply quicker, hunt smarter, and defend extra successfully.
Request full entry of TI Feeds and see how enriched indicators can remodel your response and searching workflows.