Okay-12 IT groups face intensifying stress to ship inexpensive cybersecurity, as attackers exploit colleges as “smooth targets” wealthy in delicate scholar information.
Past college students’ expertise assessments, educators should counter ransomware, phishing, and breaches head-on.
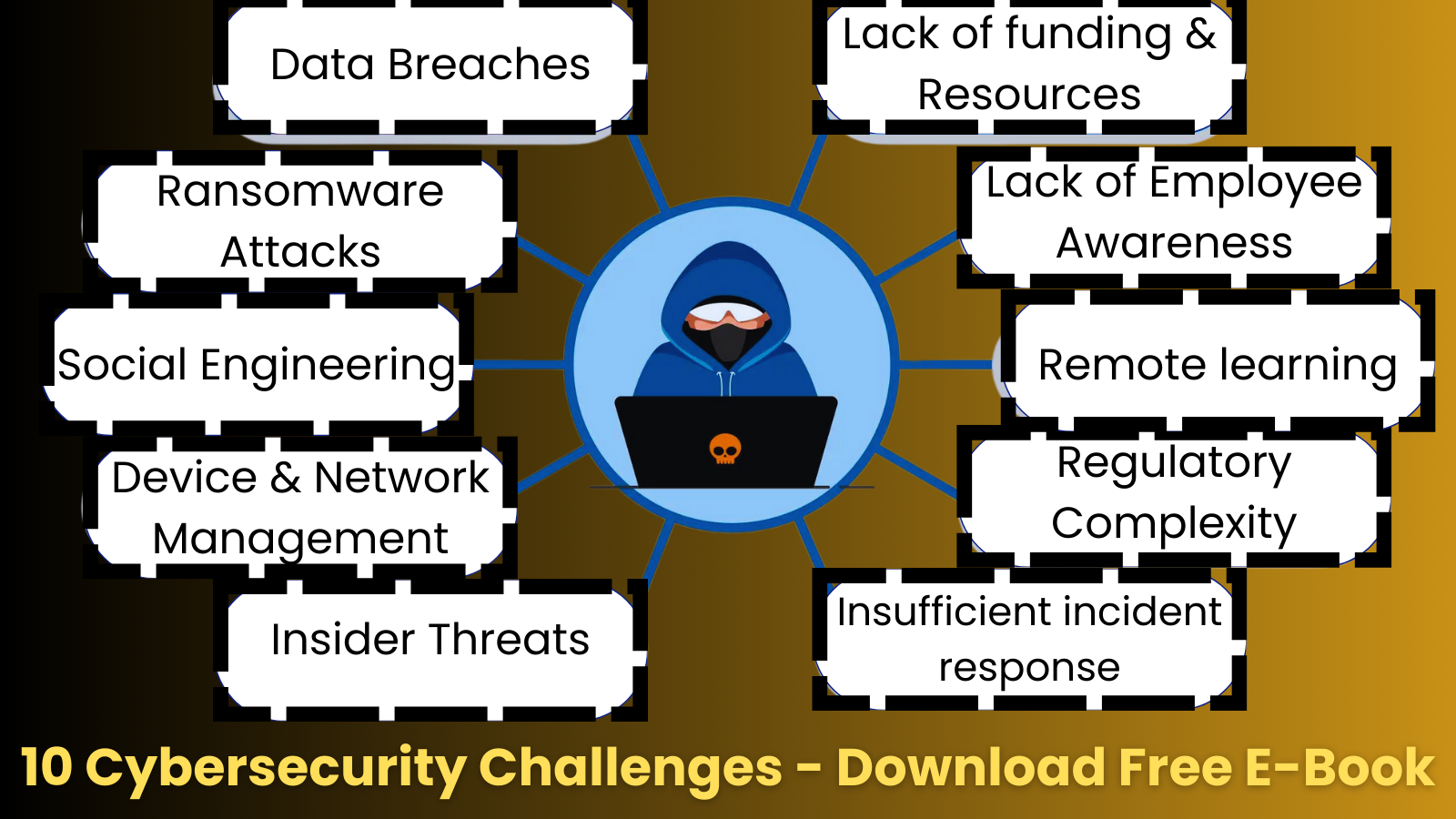
Discover the highest 10 challenges in Cynet’s free information, “Prime 10 Cybersecurity Challenges Confronted by Okay-12 Establishments.”
Drawing from real-world successes with establishments like Goshen Group Faculties (US), Wigmore Faculty Academy Belief (UK), and Grambling State College, IT leaders can mix platforms, experience, and processes to safe techniques and allow scholar success.
On-Demand Webinar to Safe the Prime 3 SME Assault Vectors: Look ahead to Free.
1. Information Breaches
Problem: 87% of instructional establishments have been breached by a cyberattack. The excessive charge of compromise stems from a number of components.
Faculties retailer huge quantities of personally identifiable data (PII), together with scholar information, monetary information, and personnel data, making them enticing targets for cybercriminals.
Faculties typically function with restricted budgets and assets, resulting in outdated IT infrastructure and inadequate cybersecurity measures.
College, employees and college students lack coaching to identify and report cyberattacks.
As colleges change into more and more interconnected by means of expertise adoption, publicity to threats and vulnerabilities will increase.
Answer: Holistic threat discount calls for a complete strategy encompassing technical controls, ongoing coaching and funding in assets to guard delicate information.
2. Ransomware Assaults
Problem: 80% of Okay-12 suppliers have been hit by a ransomware assault in 2023 — costing $1.42 million per incident to remediate on common. Along with the monetary harm, ransomware assaults price colleges three days to a few weeks of misplaced studying time throughout restoration.
Answer: Faculties can scale back their threat of ransomware assaults by deploying backup and catastrophe restoration options, modernizing their IT infrastructure and implementing sturdy safety controls. Incident response plans and coaching are additionally essential to well timed restoration, minimizing influence on college students.
3. Social Engineering
Problem: Round 30% of education-sector workers have fallen for phishing scams. In lots of such circumstances, cybercriminals impersonate faculty directors, IT employees or different trusted entities to deceive “colleagues” into disclosing delicate data or clicking on malicious hyperlinks.
Answer: Along with common consciousness coaching, there are technological measures to mitigate social engineering dangers. Electronic mail filtering and authentication protocols can stop phishing emails from reaching recipients’ inboxes and block malicious attachments. Area filtering instruments cease customers from connecting to malicious websites.
4. Machine & Community Administration
Problem: With the proliferation of cellular gadgets, laptops, tablets and IoT gadgets, IT groups in training should handle more and more complicated community environments, facilitating dependable connectivity and entry to instructional assets — with out compromising safety. Compounding the complexity, extra colleges are adopting BYOD (carry your personal system) insurance policies, including a plethora of non-public gadgets to the combination.
Answer: Faculties should implement strong endpoint safety measures to guard each school-issued and private gadgets towards malware, unauthorized entry and information breaches. This consists of deploying antivirus software program, implementing sturdy password insurance policies, and implementing endpoint detection and response (EDR) options.
10. Inadequate incident response prep
Problem: Many colleges are ill-prepared to quickly detect and comprise a cyberattack. Their lack of thorough incident response planning may end up in costlier recoveries and prolonged disruption to tutorial actions.
Answer: IT groups should collaborate with faculty stakeholders to determine clear procedures and protocols for response if a safety incident arises.
Plans ought to outline roles and obligations for incident response group members, set up communication channels for reporting and escalating incidents, and outlining processes for remediation.
Moreover, by proactively conducting threat assessments and vulnerability scans, colleges can determine potential weaknesses of their techniques and prioritize assets for mitigation efforts.
6. Lack of funding & assets
Problem: Price range looms massive within the minds of Okay-12 expertise leaders. They have to steadiness competing priorities for funding for an array of expertise initiatives, and typically cybersecurity feels the squeeze.
Restricted funding can result in outdated IT infrastructure, insufficient safety measures, and a scarcity of devoted cybersecurity personnel. Legacy techniques could lack important safety features and updates, making them extra vulnerable to exploitation.
Answer: Trendy built-in cybersecurity platforms, resembling Cynet’s All-in-One Cybersecurity Platform, present safety throughout a number of domains. Consolidated capabilities are much more inexpensive, to not point out simpler to handle, than buying a number of standalone options.
7. Lack of Worker Consciousness
Problem: Cybersecurity consciousness in Okay-12 colleges is commonly briefly provide. That college students are to not be relied upon as exemplars of cybersecurity finest follow virtually goes with out saying. However academics and employees is probably not conversant in the strategies cyber attackers use to infiltrate networks, steal private and institutional information, or disrupt instructional processes.
Answer: Faculties ought to combine ongoing, age-appropriate cybersecurity training into curriculums {and professional} improvement applications. Drills and simulations must also be carried out common to organize employees and college students to answer a cyber incident.
8. Distant studying
Problem: Faculties should make sure that college students, school, and employees can securely entry on-line studying platforms and assets from distant places with out compromising delicate data.
Answer: Distant studying dangers will be addressed through proactive, layered cybersecurity measures, together with sturdy authentication mechanisms, encrypted information transmission, and steady monitoring for unauthorized entry or suspicious conduct.
9. Regulatory complexity
Problem: Okay-12 colleges are topic to a wide range of information privateness requirements, resembling FERPA in the USA, that prescribe strict information safety measures, common audits, and necessities for workers to know their obligations below these legal guidelines. Non-compliance may end up in substantial penalties, to not point out harm to the establishment’s popularity.
Answer: Common opinions and updates to information safety insurance policies and protocol should adapt to adjustments within the regulation, in addition to evolving cyber threats. Third-party assist can present colleges with specialised experience. Log assortment and administration additionally helps to evaluate and assist regulatory compliance.
10. Insider threats
Problem: College students, school, employees, or contractors could misuse their person privileges — deliberately or by mistake — to realize unauthorized entry to delicate information and techniques.
This could result in information exfiltration, for instance, the place people steal or leak delicate data for private achieve or malicious functions. Even with out malintent, insiders could inadvertently expose delicate information by means of careless dealing with of data.
Answer: IT groups in training ought to implement entry controls to restrict privileged entry to important personnel, monitor person exercise for indicators of suspicious conduct, and implement safety insurance policies and procedures to forestall information misuse.
Conclusion
Okay-12 leaders should prioritize scholar security over organizational hurdles amid rising cyber threats. Important finest practices seem within the information “Prime 10 Cybersecurity Challenges Confronted by Okay-12 Establishments.”
Unified platforms like Cynet’s All-in-One resolution consolidate detection, response, and assist right into a single, user-friendly interface with 24/7 professional entry empowering IT groups to safe college students, academics, dad and mom, and employees. Discover a personalised demo to evaluate its match in your atmosphere.