Cybersecurity is about staying one step forward. The safety of enterprise belongings hinges on proactive menace detection and fast response powered by knowledge.
Each safety system and repair from community monitoring and incident response to analytics depends upon steady knowledge feeds to perform successfully.
The Basis: High quality Risk Information
Efficient cybersecurity hinges on knowledge high quality. Risk intelligence have to be:
Recent: Threats transfer quick. Stale knowledge leaves you susceptible to assaults already in movement.
Correct: False positives waste time and sources. Exact knowledge ensures your crew focuses on actual threats.
Full: Partial knowledge creates blind spots. Complete IOCs present the total image wanted to behave decisively.
For companies, this interprets to decreased threat, decrease prices, and quicker restoration from incidents. Inaccurate or outdated knowledge can result in missed threats, extended assaults, and monetary losses.
Excessive-quality menace intelligence feeds ship the actionable insights SOCs want to guard income, repute, and operations.
How Information Met Your Enterprise: Risk Intelligence Feeds
Risk intelligence serves because the spine for actionable safety knowledge, whereas menace intelligence feeds guarantee its steady supply in codecs that combine seamlessly with safety options.
TI feeds bridge the hole between uncooked menace data and sensible safety operations and gasoline a number of key enterprise advantages:
Actual-time relevance to present threats,
Seamless integration with present safety infrastructure,
Contextual data that allows fast decision-making,
Minimal false positives to chop prices and crew burnout.
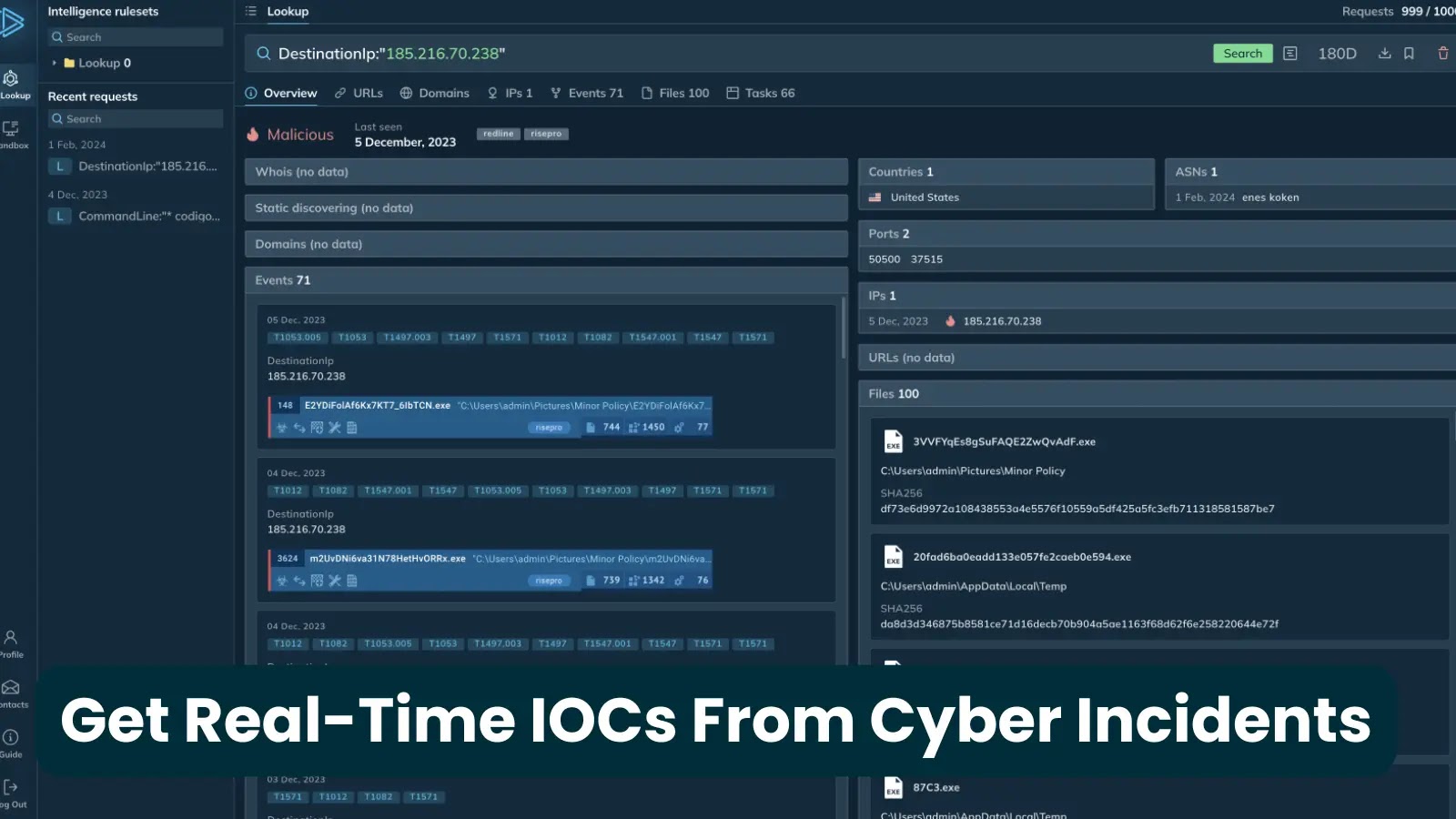
ANY.RUN’s Risk Intelligence Feeds exemplify what high quality menace intelligence ought to ship. Information supply is the important thing: actual cyber incidents investigated by over 15,000 organizations utilizing ANY.RUN’s Interactive Sandbox.
Cut back response time with actual incidents knowledge: Begin your TI Feeds trial
Why Actual-World Intelligence Issues
Cybercriminals not often assault a single firm. They aim industries, trade sectors, geographic areas, organizations with related vulnerabilities.
The threats one group faces at present will doubtless goal related companies tomorrow.
By aggregating intelligence from hundreds of actual investigations, ANY.RUN’s feeds show you how to forestall incidents by studying from assaults others face.
ANY.RUN’s feeds ship high-fidelity indicators of compromise (IPs, domains, URLs) extracted instantly from reside malware detonations.
Not like conventional sources that depend on post-incident experiences with probably expired indicators, ANY.RUN repeatedly provides recent IOCs each two hours.
This ensures SOC groups obtain actionable intelligence on threats nonetheless lively within the wild, enabling organizations to reply to rising threats at their earliest levels.
Sandbox-derived context brings behavioral insights that speed up incident response and menace looking actions.
Measurable Enterprise Impression
Methods TI Feeds improve the efficiency of safety groups
Implementing high quality menace intelligence feeds delivers tangible enterprise advantages:
1. Early Detection of Newest Assaults: Recent IOCs allow identification of rising threats earlier than they influence your group, lowering potential injury and restoration prices.
2. Lowered SOC Workload: Close to-zero false optimistic charges imply safety groups concentrate on real threats moderately than investigating numerous false alarms, enhancing operational effectivity and lowering staffing prices.
3. Accelerated Response Instances: Sandbox-generated behavioral context helps SOC groups perceive menace mechanics instantly, slicing investigation time from hours to minutes.
4. Enhanced Risk Looking Capabilities: Wealthy contextual knowledge allows proactive menace looking, permitting groups to determine superior persistent threats and complicated assault campaigns earlier than they trigger injury.
5. Improved Safety ROI: By lowering false positives and accelerating response occasions, organizations maximize their safety software investments whereas minimizing operational overhead.
Strategic Implementation For Enterprise Resilience
Companies can’t afford to react to cyber threats after the actual fact. Downtime, knowledge breaches, and reputational injury carry steep prices.
ANY.RUN’s Risk Intelligence Feeds empower your SOC with real-time, high-fidelity IOCs drawn from 15,000 organizations’ real-world incidents.
By integrating these feeds, you equip your crew to detect threats early, reply swiftly, and reduce threat.
ANY.RUN’s Risk Intelligence Feeds allow you to remain forward of attackers and detect incidents early to guard your belongings -> Combine now
The query isn’t whether or not your group wants higher menace intelligence it’s whether or not you may afford to function with out it.
In an setting the place cyber threats evolve day by day, staying forward requires the collective intelligence of the worldwide safety group working in your favor.