When an incident occurs, there’s no time to waste. SOC groups should react quick to guard their group, and this requires greater than experience. Sturdy options tailor-made to the wants of companies could make all of the distinction.
The key to radically reducing response time for incidents lies in equipping your SOC crew with an enterprise-grade resolution suited to groups that delivers quick, environment friendly outcomes.
On this article, we’ll break down how Interactive Sandbox by ANY.RUN helps groups worldwide considerably cut back MTTR and enhance proactive detection.
What makes interactive malware evaluation stand out
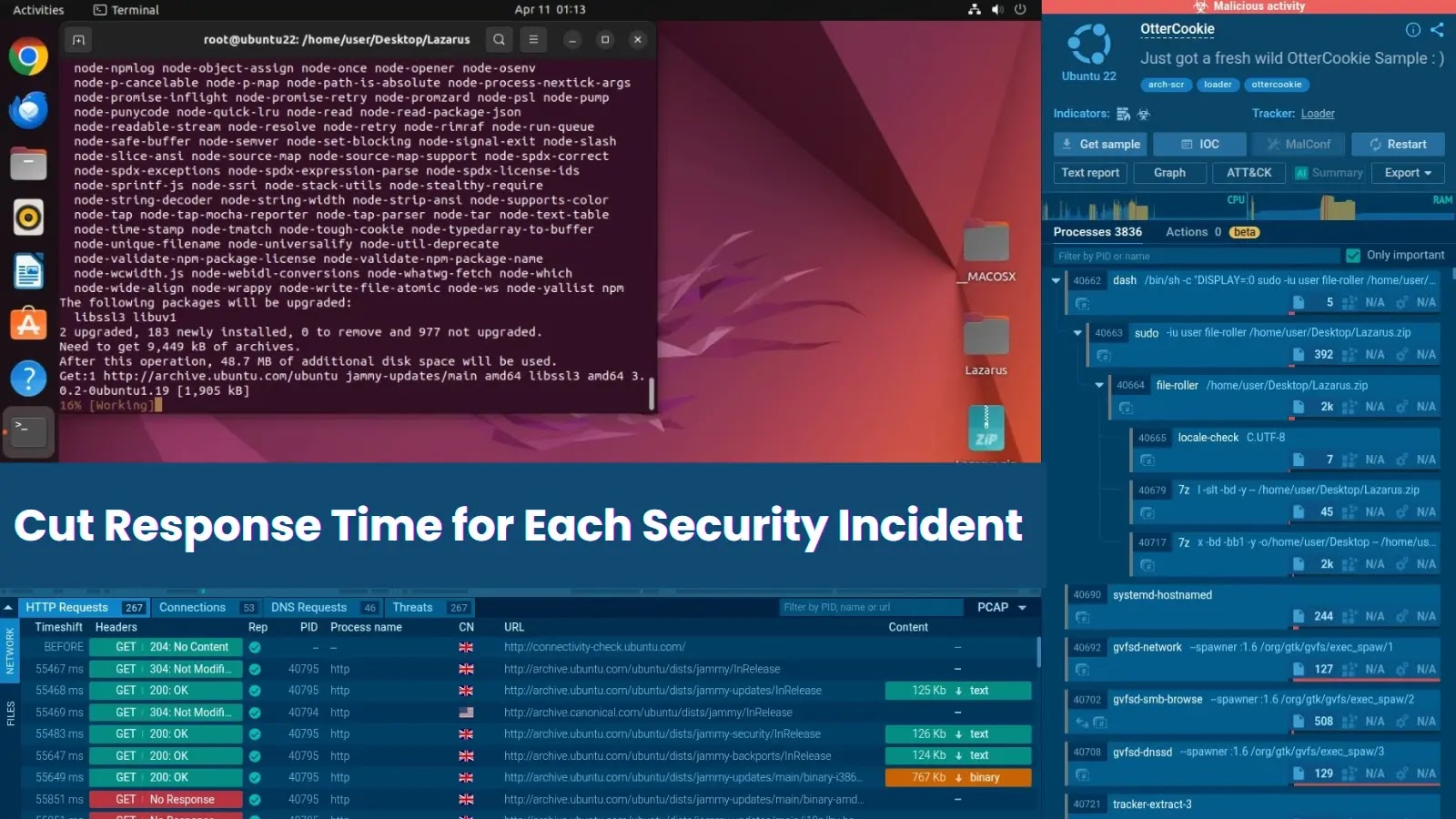
Evaluation of a risk pattern related to infamous Lazarus APT in ANY.RUN Sandbox
ANY.RUN’s hands-on method promotes a cutting-edge strategy to obtain improved metrics, together with lowered MTTR, and well-informed safety of firm infrastructure.
The twin energy of interactivity and real-time visibility into threats solves two main challenges SOC groups typically face:
Problem ANY.RUN Answer Gradual response to threats: SOC groups waste time on routine handbook duties and unoptimized processes. Interactive response: Analysts carry out in-depth investigation in an easy-to-use interface with prompt studies, decreasing workload and accelerating triage. Poor risk visibility: Automated options would possibly velocity up investigation however ship solely surface-level detection. Deep analysis in actual time: Each motion malware takes may be explored at an prompt, enabling quick and well-informed strikes.
That’s what takes interactive sandboxes like ANY.RUN a step past conventional automated malware evaluation. Analysts see greater than the ultimate verdict; they will management the method and work together with malware. All this results in a greater understanding and extra environment friendly conclusions.
Impression in numbers
With interactive malware evaluation, SOC groups obtain spectacular outcomes, equivalent to:
21 min discount in MTTR per incident
As much as 58% extra threats recognized total
Quicker risk investigations in 95% of circumstances
One other issue that additional accelerates incident response is sensible automation. In ANY.RUN sandbox, most repetitive actions may be finished robotically, together with fixing a CAPTCHA or opening a hyperlink.
The sandbox performs actions mandatory for detonation with out rising the workload of the analyst, permitting them to concentrate on extra urgent duties.
Reduce response time and enhance detection with ANY.RUN’s Interactive Sandbox for enterprises -> Get a trial on your firm
Breaking down a real-world risk in below a minute
Most assaults begin with phishing. Malicious emails may be very misleading and result in company-wide safety compromises. However it takes seconds to see the reality in ANY.RUN’s Interactive Sandbox.
Within the evaluation beneath, you may see a pdf file that appears innocent at first look. However as soon as opened, it reaches out to a phishing web page hosted on SharePoint, a reputable area that after once more would possibly lead you to consider that it’s reliable.
Nevertheless, the sandbox flags it as malicious and attributes as phishing inside seconds.
View evaluation
Suspicious PDF file analyzed in ANY.RUN sandbox
By searching by way of tabs and observing risk conduct, analysts get to react to the risk as shortly as doable: they will verify and escalate the high-risk risk, block malicious domains or IPs associated to it, and begin remediation earlier than attackers achieve a foothold.
With out a sandbox, this type of assault could be straightforward to overlook. The file seems like an everyday PDF, the internet hosting area is trusted. However this risk may result in stolen credentials utilizing social engineering and invisible redirections.
Empower your SOC with a quick and easy sandbox to realize:
Quicker Risk Response: Assaults might be detected early on, decreasing the window of publicity.
Decrease MTTR: Rapid insights into risk conduct will allow analysts to behave with velocity and confidence.
Much less Routine Workload: SOC crew might be free to concentrate on high-value duties and strategic motion, whereas repetitive duties might be finished robotically.
Conclusion
By decreasing investigation time and eliminating handbook setup, ANY.RUN helps SOC groups function extra effectively, whereas minimizing publicity to threats.
Quicker detection and deeper visibility give analysts the readability and management wanted to guard firm’s atmosphere earlier than an incident escalates.
Scale back MTTR with prompt evaluation and in-depth risk visibility -> Streamline SOC workflow with ANY.RUN