Regardless of the escalating hazard of cybersecurity breaches, high-performing Safety Operations Facilities are in a position to keep their resilience and forestall assaults. That’s what makes them important for sustainable development of companies and organizations.
However what allows highly effective SOC groups to remain forward of threats?
Selecting High quality Over Amount
Successful SOCs use menace intelligence for early detection of threats. However not all sources of intel are equally beneficial. In terms of menace information feeds, high quality outweighs amount.
As an alternative of processing countless quantities of knowledge inflicting countless false alarms, SOC groups thrive when getting access to legit, context-rich indicators from reliable sources.
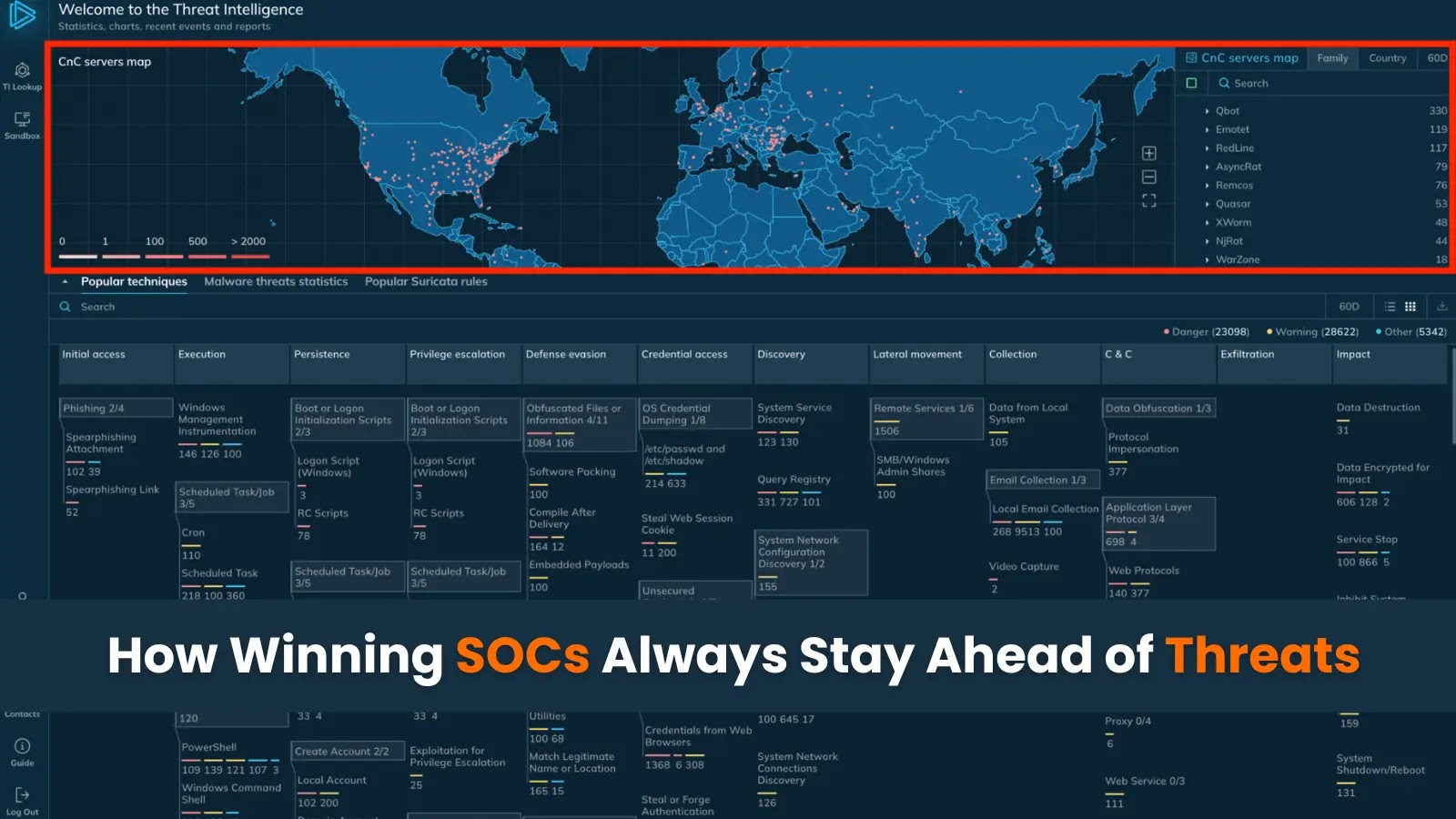
TI Feeds by ANY.RUN comprise clear, filtered information with wealthy context and common updates
ANY.RUN’s Menace Intelligence Feeds are centered on delivering high-fidelity intel created to avoid wasting your sources slightly than drain them. All TI Feeds indicators are extracted from dwell detonations of malware completed in Interactive Sandbox. There’s no noise to distract analysts; the info is dependable and might’t be discovered elsewhere.
Not like extraordinary feeds that largely depend on post-incident experiences with expired indicators, ANY.RUN delivers intel nearly in actual time, and solely from dependable sources: malware analyses completed by over 15,000 SOCs and half one million analysts. Earlier than making it to TI Feeds, all information is pre-processed to get clear outcomes with near-zero false constructive ranges.
Speedy, real-time method empowers organizations to answer rising threats at their earliest phases, staying forward of attackers.
Equip your SOC to remain forward of threats -> Strive TI Feeds
Driving Useful resource-Environment friendly Safety
A top quality supply of menace intelligence is a key issue for staying forward of rising and evolving threats. That’s what separates a profitable SOC from mediocre one.
Advantages of TI Feeds for various groups
With high-fidelity intel from Menace Intelligence Feeds, count on to see outcomes like:
Sturdy enterprise safety: Menace intelligence promotes proactive protection in opposition to cyber threats, which is irreplaceable for contemporary safety operations.
Lowered workload in SOC: Close to-zero false constructive price received’t trigger alert fatigue amongst your staff members, serving to them keep centered on prioritized incidents.
Mitigation of dangers: Context supplied for every IOC helps detect even essentially the most evasive malware, supporting each exterior and inside analysis.
Streamlined workflow: Integration by way of API/SDK in addition to compatibility with techniques like Microsoft Sentinel, OpenCTI, and ThreatConnect simplifies processes and will increase effectivity.
Keep Forward of Threats with ANY.RUN
Constructed for automation and acceleration of SOC operations, ANY.RUN integrates seamlessly with SIEM, XDR, menace intelligence platforms, and firewalls. TI Feeds help STIX/TAXII, in addition to MISP integration, and guarantee your safety specialists can:
Acquire visibility into malware: All indicators include intensive metadata, in addition to hyperlinks to associated sandbox classes for additional evaluation.
Develop menace protection: With distinctive IOCs from Reminiscence Dumps, Suricata IDS, and inside menace categorization techniques that assist them to catch evasive malware.
Automate duties for velocity: Block malicious IPs, flag associated logs, or set off playbooks based mostly on TI Feeds’ information to react quicker.
It’s time to spice up resilience in your SOC -> Get TI Feeds Trial.