A complicated new ransomware group has emerged from the shadows, focusing on multinational organizations throughout numerous sectors with precision and systematic method.
Kawa4096, first detected in June 2025, has quickly established itself as a formidable risk to enterprises spanning finance, schooling, and repair industries, notably specializing in victims in Japan and the US.
The group’s operational sophistication suggests well-coordinated cybercriminal actions with potential for widespread influence throughout a number of international locations inside a remarkably brief timeframe.
The Kawa4096 ransomware operation demonstrates superior tactical capabilities via its implementation of double extortion methodologies, combining knowledge encryption with knowledge theft to maximise leverage over victims.
The group operates a devoted Tor-based knowledge exfiltration platform the place they systematically disclose sufferer data, creating further stress for ransom fee compliance.
Their operational construction reveals meticulous planning, offering individualized declare URLs for every sufferer to manage knowledge entry and preserve organized communication channels all through the extortion course of.
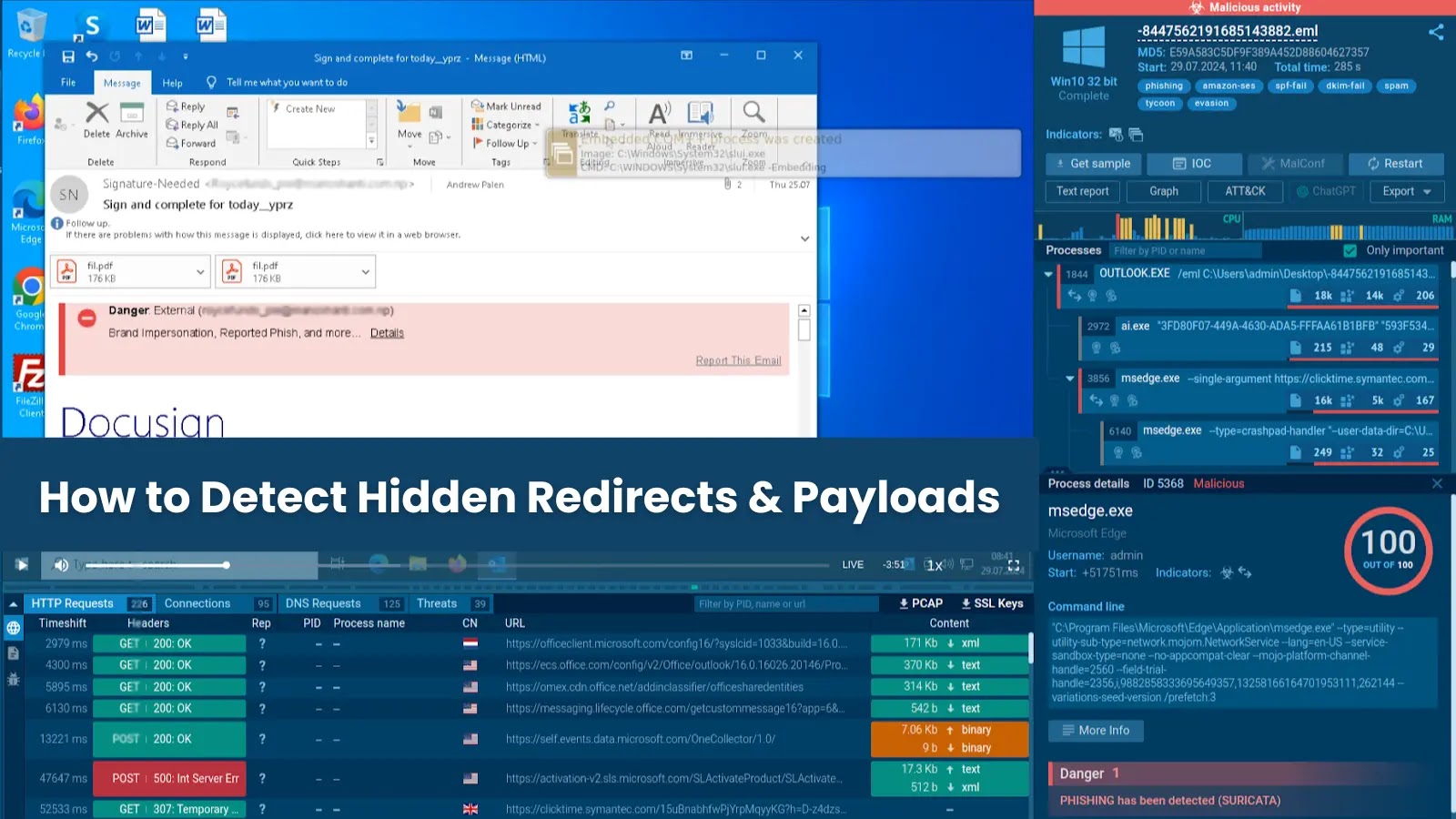
ASEC analysts famous that the ransomware’s technical implementation incorporates a number of distinctive traits that set it aside from typical ransomware households.
The malware robotically re-executes with the – all argument when launched with out parameters, making certain complete file encryption throughout goal programs.
Moreover, it creates a singular mutex named “SAY_HI_2025” utilizing the CreateMutexA API to forestall duplicate executions and potential system conflicts through the encryption course of.
The ransomware’s configuration administration system makes use of embedded useful resource sections containing 17 distinct fields that management encryption conduct.
Kawa4096 ransomware knowledge leak website (Supply – ASEC)
These configurations embody complete exclusion lists for file extensions, directories, and particular filenames to take care of system stability whereas maximizing harm.
Crucial system recordsdata resembling [.]exe, [.]dll, [.]sys, and core Home windows parts like boot[.]ini and desktop[.]ini are intentionally excluded to protect system performance and preserve negotiation capabilities.
Superior Encryption Mechanics and Evasion Ways
Kawa4096 employs refined partial encryption strategies to optimize pace and effectivity whereas sustaining damaging influence.
The malware divides goal recordsdata into 64KB chunks and encrypts solely 25% of every file, considerably decreasing encryption time whereas rendering recordsdata utterly unusable.
This selective method proves notably efficient towards databases, paperwork, and multimedia recordsdata, the place partial corruption of headers or indexes renders total recordsdata inaccessible.
The encryption course of makes use of the Salsa20 stream cipher algorithm, with encrypted recordsdata receiving extensions within the format [original_filename].[extension].[9_random_characters].
Kawa4096 ransomware ransom word (Supply – ASEC)
For recordsdata exceeding 10MB, the ransomware applies robust partial encryption patterns, whereas smaller recordsdata obtain full or weak partial encryption therapy.
This adaptive method demonstrates the group’s understanding of system efficiency optimization and sufferer influence maximization.
The ransomware systematically terminates important processes, together with database servers, workplace purposes, and backup providers to unlock recordsdata for encryption.
Goal processes embody sqlservr[.]exe, excel[.]exe, firefox[.]exe, outlook[.]exe, and quite a few different purposes that would intrude with the encryption course of or present restoration mechanisms for victims.
Discover this Story Attention-grabbing! Observe us on Google Information, LinkedIn, and X to Get Extra On the spot Updates.