The cybercrime panorama has undergone a dramatic transformation in 2025, with synthetic intelligence rising as a cornerstone know-how for malicious actors working in underground boards.
Based on Google’s Menace Intelligence Group (GTIG), the underground market for illicit AI instruments has matured considerably this yr, with a number of choices of multifunctional instruments designed to help numerous phases of the assault lifecycle.
This evolution has basically altered the accessibility and class of cybercrime, decreasing boundaries to entry for much less technical risk actors whereas amplifying the capabilities of skilled criminals.
The underground AI market has witnessed explosive development all through 2024 and 2025. Safety researchers from KELA documented a 200% enhance in mentions of malicious AI instruments throughout cybercrime boards in 2024 in comparison with the earlier yr, with the pattern persevering with to speed up into 2025.
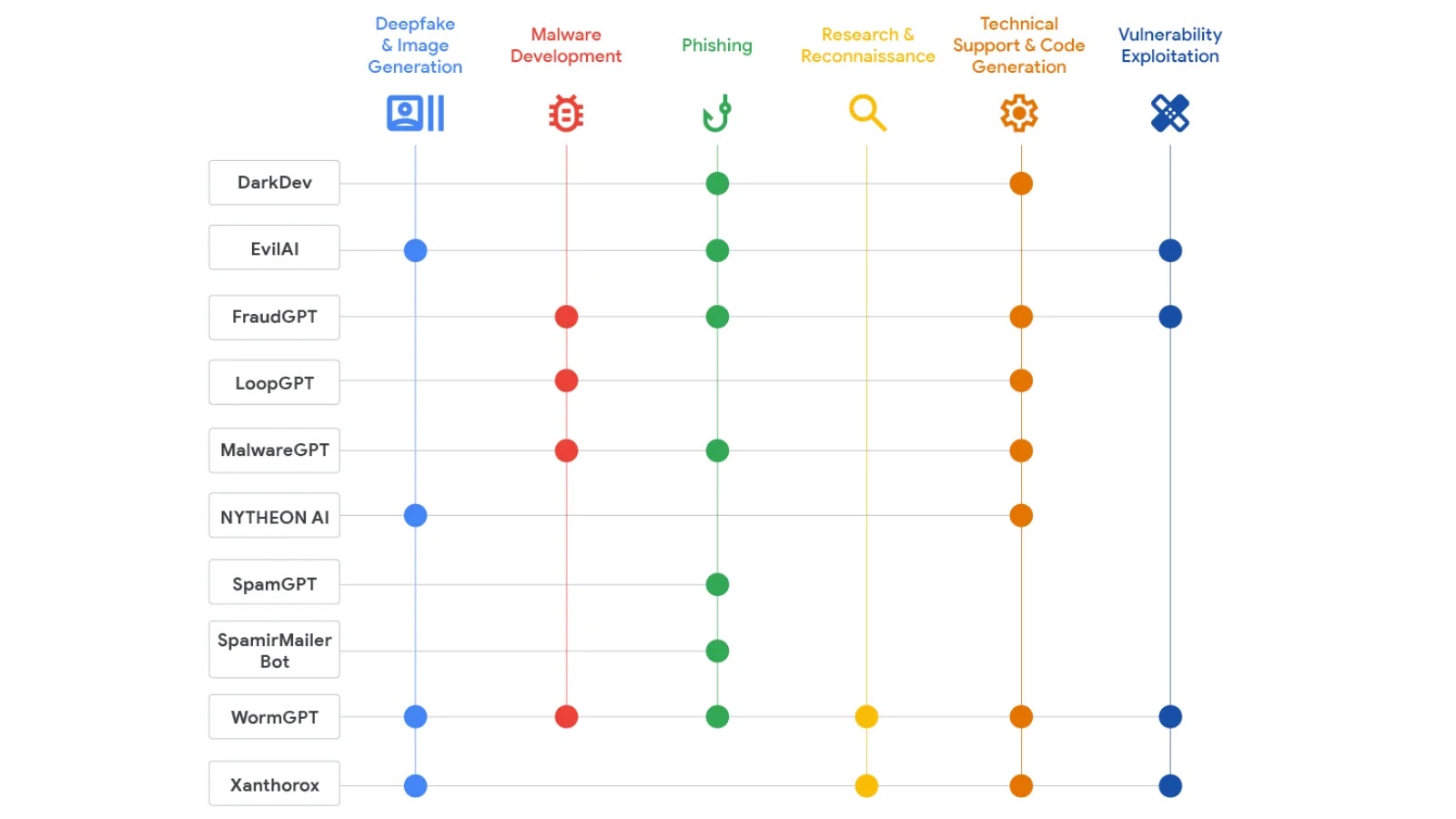
This surge represents not simply elevated chatter, however a basic shift in how cybercriminals conduct operations. Among the many most outstanding instruments marketed in English and Russian-language underground boards are WormGPT, FraudGPT, Evil-GPT, Xanthorox AI, and NYTHEON AI, every providing distinct capabilities tailor-made to totally different features of cybercrime.
AI Instruments Promoted by Menace Actors (Supply: Google)
WormGPT stands as one of many earliest and most well known malicious AI instruments within the underground ecosystem. Constructed on the GPT-J language mannequin and promoted since July 2023, WormGPT was marketed as a “blackhat different” to industrial AI methods, particularly designed to help enterprise e-mail compromise (BEC) assaults and phishing campaigns.
The instrument gained notoriety for its capability to generate convincing phishing emails that bypass spam filters, with pricing fashions starting from $100 monthly to $5,000 for personal server setups.
Researchers demonstrated that WormGPT may craft strategically intelligent and exceedingly convincing emails impersonating firm executives, a functionality that considerably elevated the risk posed by much less refined actors.
Following intently behind WormGPT, FraudGPT emerged in late July 2023 as an much more formidable platform. Promoted by the person “CanadianKingpin12” throughout a number of boards and Telegram channels, FraudGPT supplied subscription-based entry at $200 monthly or $1,700 yearly.
The instrument claimed capabilities extending past phishing to incorporate writing malicious code, creating undetectable malware, discovering vulnerabilities, discovering compromised credentials, and offering hacking tutorials.
This subscription mannequin mirrored legit software-as-a-service choices, full with tiered pricing buildings that unlocked extra options reminiscent of picture technology, API entry, and Discord integration at larger worth factors.
By 2025, the underground AI market may have developed past easy jailbroken fashions to embody refined, multi-functional platforms. Xanthorox AI represents this subsequent technology of malicious instruments, advertising itself because the “Killer of WormGPT and all EvilGPT variants”.
First detected in Q1 2025, Xanthorox distinguishes itself by its modular, self-hosted structure that operates solely on personal servers quite than counting on public cloud infrastructure.
This design drastically reduces detection and traceability dangers whereas providing an all-in-one answer for phishing, social engineering, malware creation, deepfake technology, and vulnerability analysis.
NYTHEON AI emerged as one other refined platform, leveraging a number of legit open-source fashions to offer complete GenAI-as-a-service capabilities for cybercriminals.
Operated on the darkish internet and marketed by Telegram channels and Russian boards, NYTHEON consists of six specialised fashions, together with Nytheon Coder for malicious code technology, Nytheon Imaginative and prescient for picture recognition, and Nytheon R1 for reasoning duties.
This integration of purpose-built AI fashions units NYTHEON other than earlier single-function instruments, demonstrating the rising sophistication of underground AI companies.
Cyberattacks Surge With Malicious AI platforms
Evaluation of underground commercials reveals putting commonalities throughout malicious AI platforms. Most notably, almost each notable instrument marketed in underground boards emphasised its capability to help phishing campaigns.
This common focus displays phishing’s continued dominance because the main assault vector, with AI-generated phishing representing the highest enterprise risk of 2025.
Safety analysts documented a 1,265% surge in phishing assaults pushed by generative AI capabilities, with AI-written phishing proving simply as efficient as human-crafted lures whereas requiring considerably much less time and ability.
Past phishing, underground AI instruments generally marketed capabilities spanning malware improvement, vulnerability analysis, technical help for code technology, and reconnaissance operations.
A number of platforms, together with WormGPT, FraudGPT, and MalwareGPT, promoted their capability to generate polymorphic malware that consistently modifications to evade antivirus detection.
This functionality represents a major escalation in risk sophistication, as Google researchers just lately recognized 5 new malware households utilizing AI to regenerate their very own code and conceal from safety software program.
The pricing buildings for illicit AI companies intently mirror these of typical cybercrime instruments and legit software program choices. Underground builders have adopted acquainted subscription-based fashions with tiered pricing that add technical options at larger worth factors.
Many platforms provide free variations with embedded commercials, permitting potential clients to check capabilities earlier than committing to paid subscriptions.
This strategy, mixed with developer-provided technical help and common updates, creates an ecosystem that operates remarkably equally to legit software program markets.
The low barrier to entry exemplified by instruments like Evil-GPT, priced at simply $10 per copy, demonstrates how AI has democratized refined cybercrime capabilities.
This accessibility permits financially motivated risk actors with restricted technical experience to conduct operations that beforehand required years of coaching.
The FBI and a number of cybersecurity companies have warned that AI tremendously will increase the velocity, scale, and automation of phishing schemes whereas serving to fraudsters craft extremely convincing messages tailor-made to particular recipients.
GTIG assesses with excessive confidence that financially motivated risk actors and others within the underground neighborhood will proceed augmenting their operations with AI instruments.
Given the rising accessibility of those purposes and rising AI discourse in underground boards, risk exercise leveraging AI will more and more turn into commonplace amongst cybercriminals.
By early 2025, AI-supported phishing campaigns reportedly represented greater than 80% of noticed social engineering exercise worldwide, underscoring the transformation already underway.
Because the underground AI market continues to mature, organizations face an evolving risk panorama the place refined assault capabilities can be found to anybody keen to pay modest subscription charges, basically reshaping the cybersecurity problem for the foreseeable future.
Observe us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to function your tales.