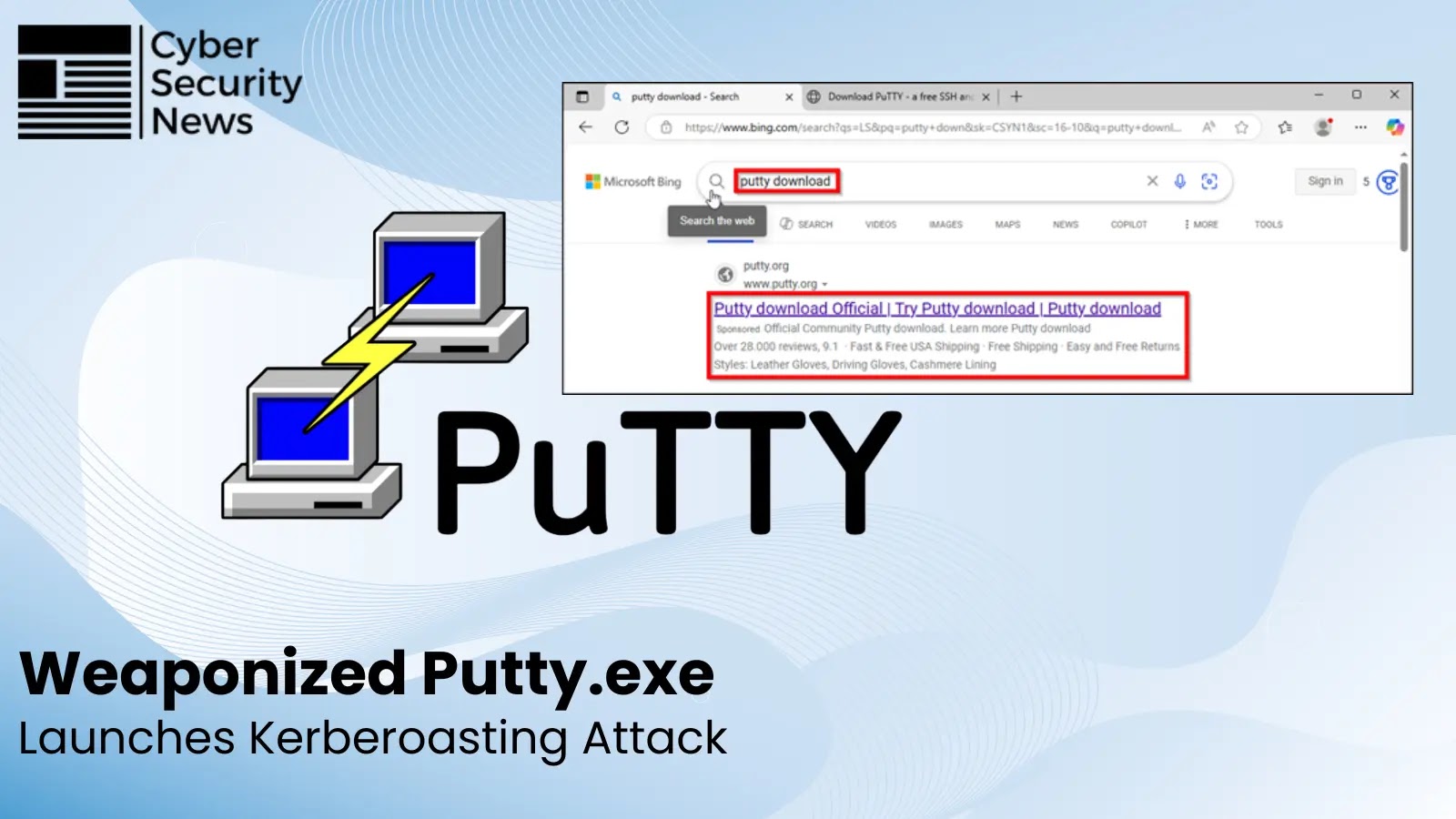
A malvertising marketing campaign utilizing sponsored outcomes on Microsoft’s search platform delivered a weaponized PuTTY that established persistence, enabled hands-on keyboard management, and executed Kerberoasting to focus on Energetic Listing service accounts.
In response to an investigation revealed by LevelBlue’s MDR SOC and corroborated by impartial analysis monitoring Oyster/Broomstick backdoor exercise tied to trojanized admin instruments distributed through search advertisements and search engine optimization poisoning.
Search outcomes spotlight a sponsored hyperlink for downloading PuTTY, illustrating the malvertising techniques used within the marketing campaign.
LevelBlue’s SOC obtained a SentinelOne high-risk alert in USM Wherever, flagging a suspicious PuTTY.exe obtain signed by “NEW VISION MARKETING LLC,” an sudden signer for reliable PuTTY and the primary purple flag on the endpoint.
The evaluation highlighted outbound visitors from PuTTY.exe to malicious infrastructure, suspicious DLL creation in %appdata% and %temp%, scheduled-task persistence through rundll32 DllRegisterServer, and HOK exercise culminating in Kerberoasting.
Subsequent, the asset was remoted, the account was disabled, and execution chains have been reconstructed. This revealed that the pretend installer had scheduled a activity, “Safety Updater,” to run each three minutes, loading a malicious DLL (twain_96.dll). This DLL then dropped “inexperienced.dll,” which was used for operator entry and reconnaissance.
Weaponized PuTTY to Exploit Kerberos
Faux PuTTY with an anomalous code-signing certificates executed and created a scheduled activity persistence, invoking rundll32 with DllRegisterServer at three-minute intervals.
The primary-stage DLL (twain_96[.]dll) dropped a second-stage (inexperienced[.]dll) that initiated a single outbound 443 connection and spawned cmd[.]exe for discovery instructions in step with ransomware operator TTPs (nltest, web group area admins, nltest /dclist).
SentinelOne telemetry and VirusTotal classifications mapped the DLLs to the Oyster/Broomstick backdoor household identified for hardcoded C2, scheduled-task persistence, and distant command execution.
The ultimate recorded motion was an inline PowerShell script performing Kerberoasting, requesting TGS tickets for SPN-bearing accounts and leveraging weak RC4-HMAC if AES enforcement was absent, then extracting ticket bytes in-memory to emit Hashcat-ready $krb5tgs$ materials (mode 13100).
PowerShell script showcasing a command execution bypass designed for Kerberoasting
The script borrowed from Invoke-Kerberoast patterns, executed absolutely in-memory with out disk writes, and was validated through USM Wherever occasions exhibiting RC4-HMAC-encrypted Kerberos service tickets (Occasion ID 4769). This enabled offline cracking of service account credentials for privilege escalation and lateral motion in opposition to AD providers.
LevelBlue traced the preliminary entry to malicious sponsored outcomes impersonating putty[.]org and redirecting to typosquatted domains resembling puttyy[.]org and puttysystems[.]com that delivered the trojanized installer, with payload internet hosting noticed through heartlandenergy[.]ai and a rotating loader script at putty[.]community pulling from compromised WordPress websites.
The MDR staff famous variant payload hashes, a number of code-signing certificates (together with NEW VISION MARKETING LLC) to evade hash/signer-based detections, and alternate scheduled-task names resembling “FireFox Agent INC” in sandboxed samples.
This exercise aligns with broader 2024–2025 malvertising/search engine optimization poisoning tendencies delivering trojanized PuTTY/WinSCP and Oyster/Broomstick, as reported by Rapid7 and Arctic Wolf.
Here’s a consolidated desk of the reported IOCs from the LevelBlue investigation into weaponized PuTTY malvertising tied to the Oyster/Broomstick backdoor; add these to blocklists and detection pipelines for speedy containment. The entries under mirror the symptoms documented by LevelBlue and aligned open-source reporting on the identical marketing campaign.
Beneath is the consolidated IOC desk combining domains, hashes, signers, IPs, URLs, and scheduled duties linked to the weaponized PuTTY/Oyster malvertising exercise. Use these indicators for blocklists, retro-hunting, and detection content material.
TypeIndicatorContext/NotesDomainputtyy[.]orgTyposquat used to ship trojanized PuTTY installers.Domainputtysystems[.]comMalvertising touchdown used to impersonate PuTTY obtain.Domainupdaterputty[.]comNewly registered area related to marketing campaign stream.Domainputty[.]betCampaign-associated area registration.Domainputtyy[.]comTyposquat tied to supply infrastructure.Domainputty[.]runCampaign-associated area registration.Domainputty[.]latCampaign-associated area registration.Domainputty[.]us[.]comCampaign-associated area registration.Domainheartlandenergy[.]aiObserved internet hosting payload behind “Obtain PuTTY.”Domainputty[.]networkLoader web page rotating mirrors through JS for payload checks.Domainruben.findinit[.]comCompromised WordPress web site used to serve payloads.Domainekeitoro.siteinwp[.]comCompromised WordPress web site used to serve payloads.Domaindanielaurel[.]tvCompromised WordPress web site used to serve payloads.File hash (SHA256)0b85ad058aa224d0b66ac7fdc4f3b71145aede462068cc9708ec2cee7c5717d4Malicious PuTTY/Oyster-related pattern.File hash (SHA256)e9f05410293f97f20d528f1a4deddc5e95049ff1b0ec9de4bf3fd7f5b8687569Malicious PuTTY/Oyster-related pattern.File hash (SHA256)d73bcb2b67aebb19ff26a840d3380797463133c2c8f61754020794d31a9197d1Malicious PuTTY/Oyster-related pattern.File hash (SHA256)dd995934bdab89ca6941633dea1ef6e6d9c3982af5b454ecb0a6c440032b30fbMalicious PuTTY/Oyster-related pattern.File hash (SHA256)03012e22602837132c4611cac749de39fb1057a8dead227594d4d4f6fb961552Malicious PuTTY/Oyster-related pattern.File hash (SHA256)a653b4f7f76ee8e6bd9ffa816c0a14dca2d591a84ee570d4b6245079064b5794Malicious PuTTY/Oyster-related pattern.File hash (SHA256)e02d21a83c41c15270a854c005c4b5dfb94c2ddc03bb4266aa67fc0486e5dd35Malicious PuTTY/Oyster-related pattern.File hash (SHA256)80c8a6ecd5619d137aa57ddf252ab5dc9044266fca87f3e90c5b7f3664c5142fMalicious PuTTY/Oyster-related pattern.File hash (SHA256)1112b72f47b7d09835c276c412c83d89b072b2f0fb25a0c9e2fed7cf08b55a41Malicious PuTTY/Oyster-related pattern.File hash (SHA256)3d22a974677164d6bd7166e521e96d07cd00c884b0aeacb5555505c6a62a1c26Malicious PuTTY/Oyster-related pattern.File hash (SHA256)e8e9f0da26a3d6729e744a6ea566c4fd4e372ceb4b2e7fc01d08844bfc5c3abbMalicious PuTTY/Oyster-related pattern.File hash (SHA256)eef6d4b6bdf48a605cade0b517d5a51fc4f4570e505f3d8b9b66158902dcd4afMalicious PuTTY/Oyster-related pattern.File signerTHE COMB REIVERS LIMITEDAbused code-signing certificates on trojanized installers.File signerNEW VISION MARKETING LLCAnomalous signer on pretend PuTTY[.]exe noticed.File signerPROFTORG LLCAbused certificates on malicious samples.File signerLLC FortunaAbused certificates on malicious samples.File signerLLC BRAVERYAbused certificates on malicious samples.File signerLLC Infomed22Abused certificates on malicious samples.IP45.86.230[.]77C2/registration/login endpoints noticed.IP185.208.159[.]119Malicious API host noticed in exercise.IP144.217.207[.]26Outbound 443 connection (inexperienced.dll).IP85.239.52[.]99Malicious API host noticed in exercise.IP194.213.18[.]89C2 registration/login endpoints noticed.URL (defanged)hxxp[:]//185.208.158[.]119/api/jgfnsfnuefcnegfnehjbfncejfhMalicious API path.URL (defanged)hxxp[:]//185.208.158[.]119/api/kcehcMalicious API path.URL (defanged)hxxp[:]//45.86.230[.]77:443/regC2 registration endpoint.URL (defanged)hxxp[:]//45.86.230[.]77:443/loginC2 login endpoint.URL (defanged)hxxp[:]//85.239.52[.]99/api/jgfnsfnuefcnegfnehjbfncejfhMalicious API path.URL (defanged)hxxp[:]//85.239.52[.]99/api/kcehcMalicious API path.URL (defanged)hxxp[:]//194.213.18[.]89:443/regC2 registration endpoint.URL (defanged)hxxp[:]//194.213.18[.]89:443/loginC2 login endpoint.Scheduled taskSecurity UpdaterPersistence through rundll32 DllRegisterServer at 3‑minute intervals.Scheduled taskFireFox Agent INCAlternate activity identify seen in sandboxed samples.
Suggestions embrace blocking the recognized domains, imposing AES for Kerberos on SPN accounts, rotating credentials for affected SPNs, and proscribing software program acquisition to vetted repositories and official vendor websites.
Safety groups ought to deploy customized detections for rundll32 DllRegisterServer misuse, three-minute recurring scheduled duties, in-memory Kerberoasting patterns, and storyline correlations linking pretend admin instruments to DLL drops and cmd.[]exe reconnaissance.
Steady person coaching for privileged employees and speedy MDR-led risk looking throughout fleets can scale back dwell time and blunt credential theft-to-ransomware escalation paths.
Discover this Story Fascinating! Observe us on LinkedIn and X to Get Extra Prompt Updates.