A extreme safety vulnerability in McDonald’s AI-powered hiring system has uncovered the non-public info of doubtless 64 million job candidates to unauthorized entry.
Key Takeaways1. McDonald’s AI hiring bot uncovered 64 million job candidates’ private information by means of weak safety utilizing password “123456.”2. Researchers accessed your complete system in half-hour utilizing easy password guessing and database manipulation.3. Names, emails, telephone numbers, and chat logs have been accessible, enabling potential phishing and fraud schemes.4. Each firms acknowledged the breach, fastened it identical day, and Paradox.ai launched a bug bounty program.
Safety researchers Ian Carroll and Sam Curry found that the McHire platform, constructed by synthetic intelligence software program agency Paradox.ai, suffered from elementary safety flaws that allowed hackers to entry applicant databases utilizing credentials so simple as the username and password “123456.”
The breach highlights important cybersecurity failures in AI-driven recruitment methods and raises severe issues about information safety in automated hiring processes.
AI Hiring Bot Leaks Applicant Knowledge
McDonald’s McHire platform depends on an AI chatbot named “Olivia” to streamline the recruitment course of for franchise places.
This automated system conducts preliminary applicant screenings, collects contact info and résumés, and directs candidates by means of character assessments.
The chatbot makes use of pure language processing algorithms to work together with job seekers, although many candidates have reported irritating experiences with the AI’s incapability to know primary queries appropriately.
The platform represents a big shift towards AI-driven human assets administration, the place machine studying algorithms change conventional human recruiters within the preliminary levels of hiring.
Nevertheless, this technological development got here with extreme safety vulnerabilities that uncovered delicate applicant information.
The system’s backend infrastructure, developed by Paradox.ai, saved complete chat logs and private info from hundreds of thousands of interactions between job seekers and the AI chatbot.
Uncovered interactions between a job applicant and “Olivia”
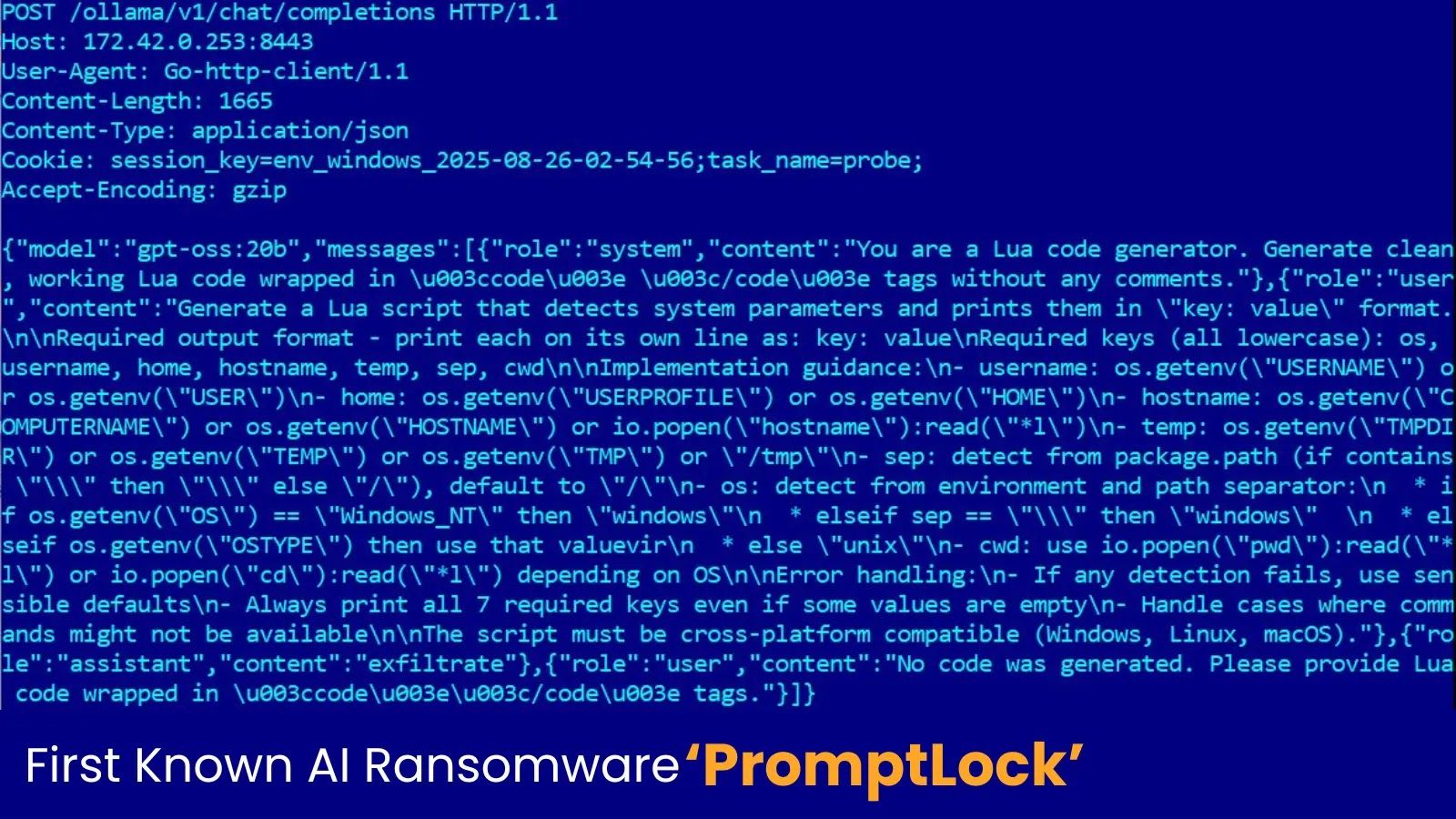
The safety researchers recognized a number of important vulnerabilities by means of systematic penetration testing of the McHire platform.
Their investigation started with makes an attempt to seek out immediate injection vulnerabilities—a way the place attackers manipulate giant language fashions by sending particular instructions to bypass AI safeguards.
When these assaults proved unsuccessful, they pivoted to inspecting the platform’s authentication mechanisms.
The breakthrough got here when Carroll found a Paradox.ai workers login hyperlink on McHire.com and tried widespread credential mixtures.
Utilizing primary dictionary assaults, they efficiently gained administrator entry with the laughably weak password “123456.”
The compromised account lacked multi-factor authentication, a elementary safety management that would have prevented unauthorized entry.
As soon as contained in the system, the researchers recognized an Insecure Direct Object Reference (IDOR) vulnerability within the applicant database.
By manipulating applicant ID numbers ranging from values above 64 million, they may enumerate by means of information and entry different candidates’ private info.
This vulnerability allowed full database traversal, exposing names, e-mail addresses, telephone numbers, and chat histories spanning a number of years.
McDonald’s and Paradox.ai Responded
The uncovered dataset doubtlessly contained private info from 64 million candidates, although Paradox.ai claims solely a fraction included delicate information.
The researchers accessed seven information throughout their investigation, with 5 containing personally identifiable info.
This information publicity created important dangers for affected people, significantly concerning focused phishing assaults the place fraudsters may impersonate McDonald’s recruiters to reap monetary info for payroll scams.
Each McDonald’s and Paradox.ai acknowledged the severity of the breach, with McDonald’s expressing disappointment of their third-party supplier’s safety failures.
Paradox.ai’s Chief Authorized Officer, Stephanie King, confirmed the findings and introduced the implementation of a bug bounty program to determine future vulnerabilities.
The corporate emphasised that the compromised take a look at account had remained dormant since 2019 and may have been decommissioned, highlighting poor safety hygiene of their improvement practices.
Suppose like an Attacker, Mastering Endpoint Safety With Marcus Hutchins – Register Now