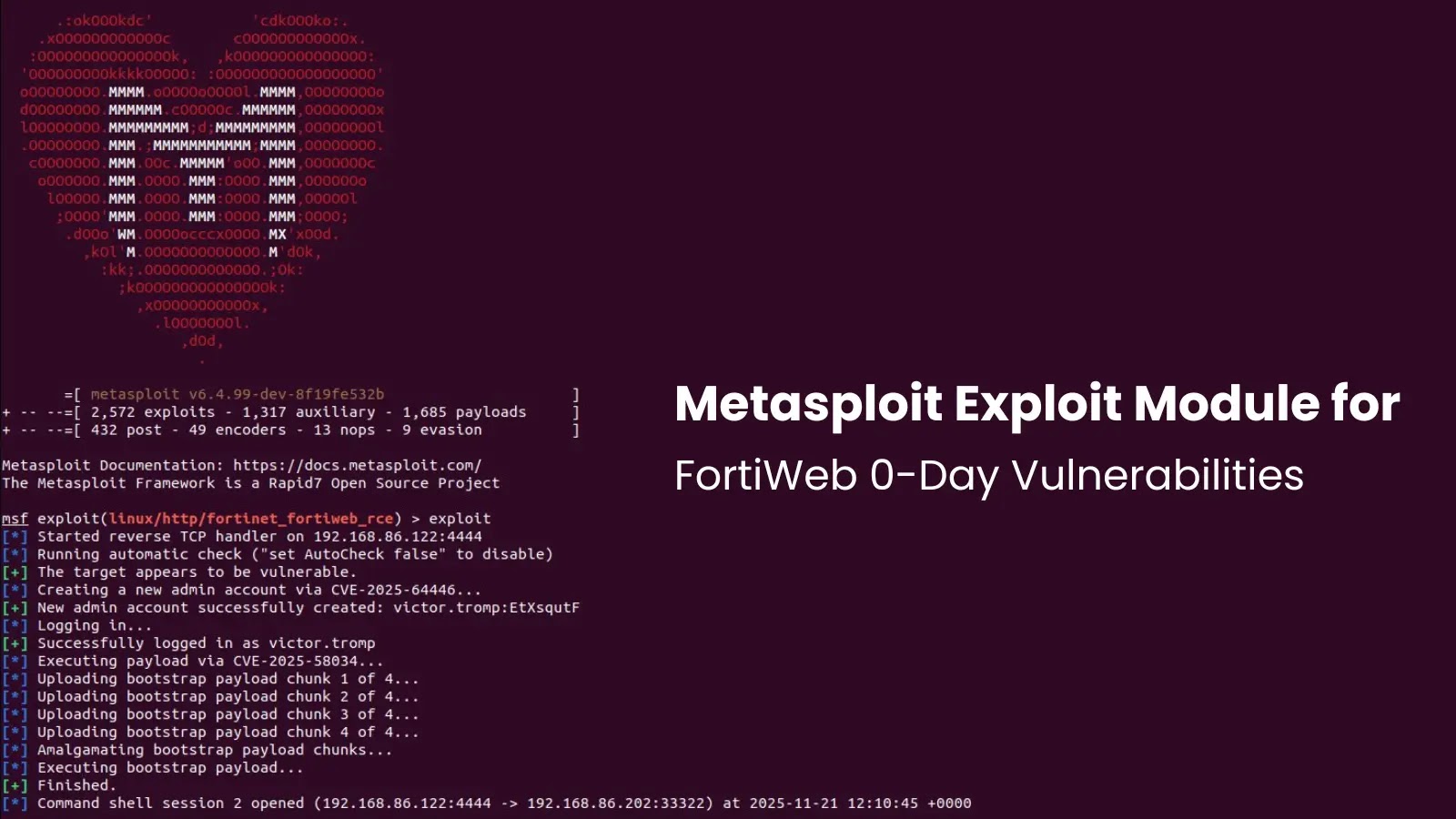
The Metasploit Framework has launched a brand new exploit module concentrating on vital vulnerabilities in Fortinet’s FortiWeb Net Software Firewall (WAF).
This module chains two not too long ago disclosed flaws, CVE-2025-64446 and CVE-2025-58034, to attain unauthenticated Distant Code Execution (RCE) with root privileges.
The discharge follows studies of lively exploitation within the wild, together with “silent patches” and subsequent bypasses which have left many home equipment uncovered.
The Exploitation Chain
The brand new module, recognized as exploit/linux/http/fortinet_fortiweb_rce, automates a classy assault chain that bypasses authentication mechanisms earlier than executing arbitrary working system instructions.
The assault begins with CVE-2025-64446, a vital authentication bypass vulnerability with a CVSS rating of 9.1. As analyzed by researchers at watchTowr, this flaw entails a path traversal problem mixed with improper dealing with of the CGIINFO header.
By manipulating this header and traversing to the fwbcgi executable, an unauthenticated attacker can impersonate the built-in admin person and create a brand new administrative account with out legitimate credentials.
As soon as administrative entry is established, the module leverages CVE-2025-58034 to compromise the underlying system. This second vulnerability is an authenticated command injection flaw discovered within the FortiWeb API and CLI, the place particular components in OS instructions aren’t correctly neutralized.
Rapid7 evaluation confirms that this flaw permits an authenticated person to flee the supposed shell restrictions and execute instructions as the basis person. By chaining these two points, the Metasploit module permits an exterior attacker to go from zero entry to full system management in seconds.
The Metasploit module is designed to be versatile throughout totally different assault situations. In its default mode, it routinely exploits the authentication bypass (CVE-2025-64446) to provision a random administrator account.
It then authenticates with these new credentials to set off the command injection. Alternatively, if an attacker already possesses legitimate credentials, the module may be configured to skip the bypass section and immediately exploit CVE-2025-58034.
Technically, the exploit makes use of a chunked add mechanism to ship its payload. As seen within the pull request documentation, the module uploads a “bootstrap payload” in a number of components (e.g., 4 chunks) earlier than amalgamating and executing them.
This methodology ensures dependable execution even throughout the constrained atmosphere of the equipment. Profitable exploitation grants a shell with uid=0(root), giving the attacker full management over the WAF machine.
Fortinet has launched patches to deal with these vulnerabilities, and customers are strongly suggested to improve to FortiWeb model 8.0.2 or later instantly.
As a result of CVE-2025-64446 permits for the silent creation of rogue directors, merely patching is inadequate for doubtlessly compromised gadgets. Safety groups ought to audit their person lists for unknown accounts and evaluate logs for requests to /api/v2.0/cmdb/system/admin originating from untrusted IP addresses.
CVE IDVulnerability TypeCVSSAffected Merchandise (Partial Listing)CVE-2025-64446Auth Bypass / Path Traversal9.1FortiWeb 7.4.0-7.4.4, 7.6.0-7.6.4, 8.0.0-8.0.1CVE-2025-58034OS Command Injection7.2FortiWeb 8.0.0-8.0.1
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.