Abstract
1. Microsoft Defender for Workplace 365 is introducing giant language mannequin (LLM) know-how to supply clear, human-readable explanations for why emails are categorised as spam, phishing, or clear.
2. The characteristic will deploy robotically worldwide from late June to mid-July 2025, requiring no administrative motion or configuration adjustments from organizations.
3. Customers will obtain detailed reasoning behind classification choices, together with key indicators and behavioral insights.
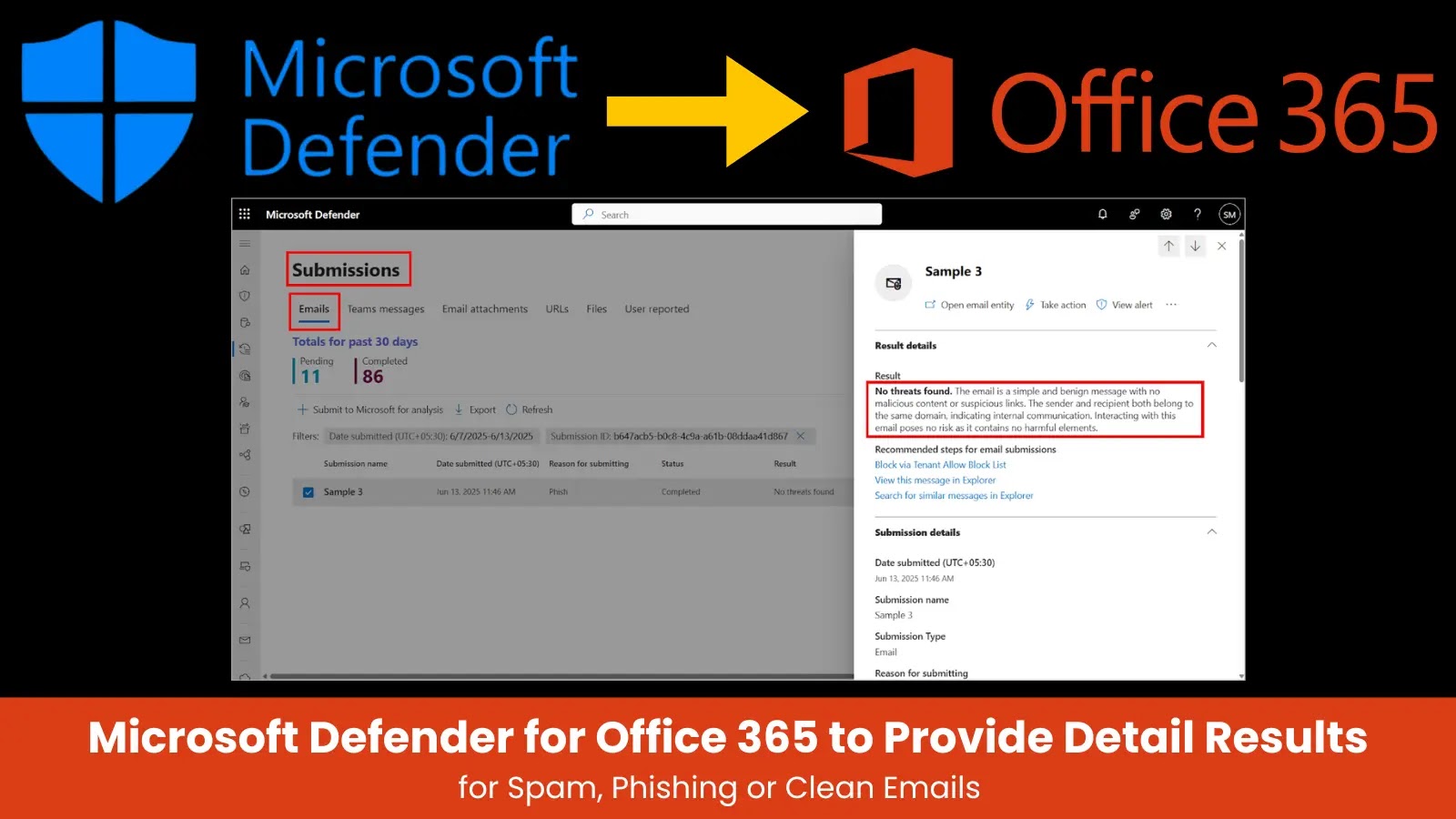
4. Customers can entry AI explanations via the Microsoft Defender portal at safety.microsoft.com beneath Actions & Submissions > Submissions.
Microsoft is about to revolutionize electronic mail safety transparency with the introduction of AI-powered explanations for electronic mail submission leads to Microsoft Defender for Workplace 365.
This groundbreaking characteristic, leveraging giant language fashions (LLMs), will present clear, human-readable rationales for why messages are categorised as spam, phishing, or clear, marking a major development in cybersecurity communication and person understanding.
AI-Powered Enhancement
The brand new functionality represents a serious technological leap in electronic mail safety transparency, using subtle giant language fashions (LLMs) to generate complete explanations for electronic mail classification choices.
This characteristic, related to Microsoft 365 Roadmap ID 488098, addresses a longstanding problem in cybersecurity the place customers usually obtain classification outcomes with out understanding the underlying reasoning.
The AI-generated explanations will embrace a number of parts designed to reinforce person comprehension.
These embody the precise reasoning behind every classification resolution, key indicators that influenced the willpower, and optionally available behavioral insights that present context about sender patterns or message traits.
When the AI clarification system is unavailable, the platform will robotically revert to straightforward explanations, making certain a constant person expertise.
The system helps 5 distinct consequence sorts similar to:
Unknown classifications happen when Microsoft can not attain a definitive resolution attributable to inaccessible content material or analyst disagreement.
Bulk classifications determine senders as bulk mailers with future blocking potential primarily based on BCL (Bulk Grievance Degree).
Spam classifications set off blocking of comparable gadgets primarily based on SCL (Spam Confidence Degree).
No threats discovered signifies clear content material with potential filter updates.
Threats discovered identifies malicious content material requiring quick filter modifications.
The rollout timeline spans from late June 2025 via mid-July 2025, with world availability deliberate throughout all Microsoft Defender for Workplace 365 deployments.
This characteristic can be obtainable by default, requiring no administrative intervention or configuration adjustments, streamlining the implementation course of for organizations worldwide.
Technical entry requires navigation to the Microsoft Defender portal at adopted by accessing Actions & Submissions > Submissions or straight visiting
Customers should choose the Emails tab and open particular submissions to view AI-generated explanations within the Outcome Particulars part.
The present scope particularly targets electronic mail submissions throughout the Microsoft Defender portal, excluding recordsdata, Groups messages, URLs, or different user-submitted content material sorts.
This targeted strategy ensures optimum efficiency and accuracy through the preliminary deployment part.
In line with the Report, Organizations can anticipate quick advantages with out requiring preparatory actions, as the automated rollout eliminates administrative overhead.
Nevertheless, safety groups ought to evaluation current submission workflows to maximise the brand new explanatory capabilities and take into account updating inside documentation to mirror enhanced transparency options.
The implementation supplies vital worth for safety operations facilities and end-users alike, providing deeper insights into electronic mail risk detection processes.
Organizations could wish to notify directors and customers about these enhancements to make sure optimum utilization of the improved classification explanations and keep constant safety consciousness protocols throughout their Microsoft 365 environments.
Reside Credential Theft Assault Unmask & Instantaneous Protection – Free Webinar