New analysis uncovers beneficial insights hidden inside Microsoft Intune’s Cell Gadget Administration (MDM) certificates, providing a extra dependable strategy to confirm system and tenant identities in comparison with conventional strategies like registry values.
These certificates, issued to enrolled units, comprise Object Identifiers (OIDs) that, when correctly decoded, reveal distinctive GUIDs for the MDM Gadget ID and Entra ID Tenant ID, enhancing belief in system authentication.
This discovery, detailed by Ben Whitmore, highlights how endpoint managers can leverage cryptographic knowledge for sturdy identification affirmation in enterprise environments.
The Intune MDM certificates ensures safe communication between units and the Intune service, embedding non-human-readable extensions that maintain vital identifiers.
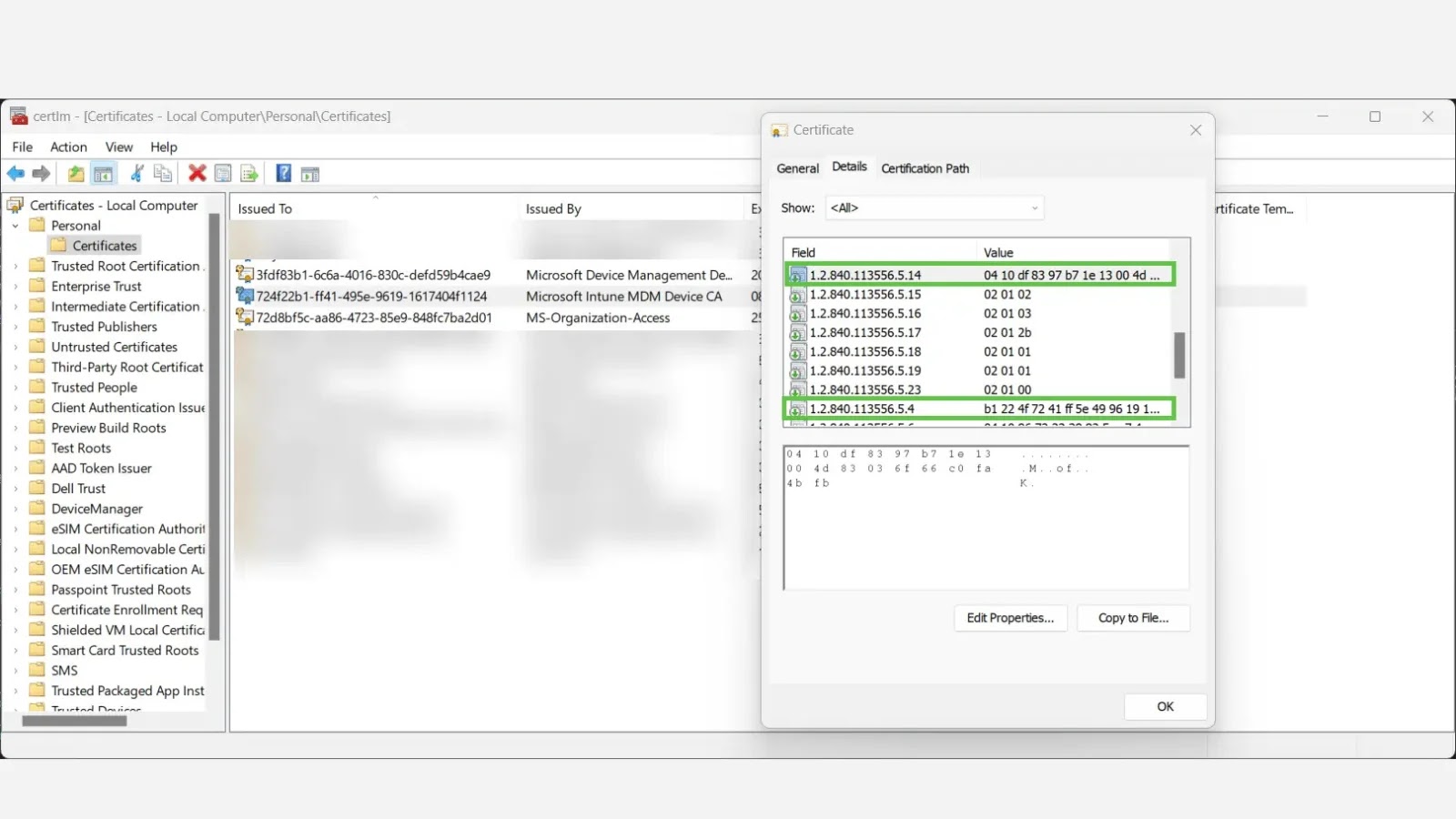
Researchers recognized two key OIDs: 1.2.840.113556.5.4 for the MDM Gadget ID and 1.2.840.113556.5.14 for the Entra ID Tenant ID, each saved as blended little-endian and big-endian byte arrays requiring particular reordering to kind readable GUIDs.
In contrast to registry values, which will be tampered with simply, these certificate-bound identifiers present a sequence of belief backed by Microsoft’s certification authorities.
Hidden OIDs in MDM Certificates
For example, the certificates’s properties, seen in instruments like certmgr.msc, present byte arrays that should be rearranged to unlock their that means, providing IT admins a tamper-resistant various for auditing system enrollment.
Extracting significant knowledge from these OIDs entails a exact byte reordering course of, usually found by means of trial and error.
For the MDM Gadget ID (OID 1.2.840.113556.5.4), the primary 4 bytes are reversed, adopted by reversals of the following two pairs, whereas the ultimate six bytes stay unchanged; utilizing instance bytes 12 34 56 78 9A BC DE F0 12 34 56 78 90 AB CD EF yields the GUID 78563412-BC9A-F0DE-1234-567890ABCDEF after transformation.
Equally, the Entra ID Tenant ID (OID 1.2.840.113556.5.14) follows a variant sample with eight unchanged ultimate bytes, changing pattern knowledge A1 B2 C3 D4 E5 F6 12 34 56 78 9A BC DE F0 01 23 A1 into F6E5D4C3-F6E5-3412-5678-9ABCDEF00123A1.
This methodology ensures high-confidence verification, as the information originates from trusted issuers just like the Microsoft Intune MDM Gadget CA, lowering dangers from modifiable system artifacts.
To streamline this course of, builders at MSEndpointMgr launched a PowerShell script, Get-TenantInformation.ps1, obtainable on GitHub, which automates certificates discovery and decoding throughout LocalMachine and person profile shops.
The script searches for certificates issued by the Microsoft Intune MDM Gadget CA or MS-Group-Entry, validates their chain towards anticipated root and intermediate authorities, and checks personal key exportability utilizing certutil for Key Storage Supplier particulars.
It processes OIDs like 1.2.840.113556.5.4 and 1.2.840.113556.5.14, reassembling bytes into GUIDs whereas outputting complete particulars, together with thumbprint, issuer, and belief standing, in accordance with Ben Whitmore.
Working as admin reveals whether or not keys are TPM-protected, indicated by “Microsoft Platform Crypto Supplier” versus software-only on older units, flagging potential vulnerabilities.
This device empowers admins to audit Entra ID be a part of varieties and tenant areas from extensions like 1.2.840.113556.1.5.284.7, fostering proactive safety administration.
By prioritizing certificates OIDs over much less safe alternate options, organizations can construct stronger system identification assurance, akin to selecting premium authentication over fundamental checks.
This strategy not solely elevates belief but in addition aids in risk detection by confirming reputable tenant associations. As Intune evolves, such strategies will show important for sustaining endpoint integrity.
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to function your tales.