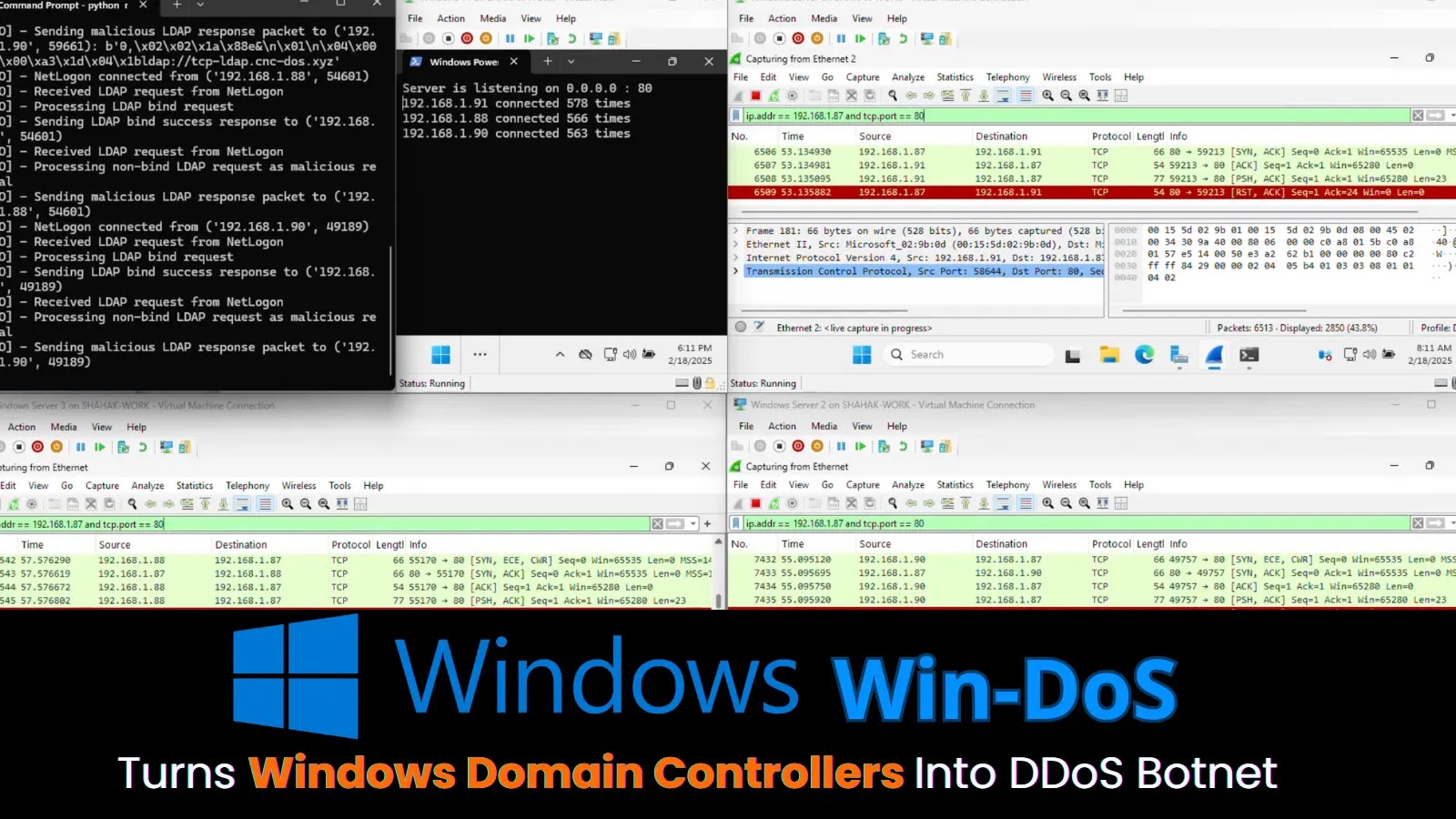
1000’s of organizations worldwide face lively cyberattacks concentrating on Microsoft SharePoint servers by means of two crucial vulnerabilities, prompting pressing authorities warnings and emergency patches.
Microsoft confirmed over the weekend that risk actors are actively exploiting two zero-day vulnerabilities in on-premises SharePoint servers, designated CVE-2025-53770 and CVE-2025-53771.
The assaults, dubbed “ToolShell” by safety researchers, have compromised dozens of organizations globally since July 18, together with U.S. federal companies, universities, and vitality firms.
The first vulnerability, CVE-2025-53770, carries a crucial CVSS rating of 9.8 and allows unauthenticated distant code execution by means of unsafe deserialization of untrusted information.
The companion flaw, CVE-2025-53771 (CVSS 6.3), permits attackers to bypass authentication by manipulating HTTP headers, particularly crafting requests with cast Referer headers pointing to SharePoint’s sign-out web page.
The U.S. Cybersecurity and Infrastructure Safety Company (CISA) added CVE-2025-53770 to its Identified Exploited Vulnerabilities catalog on July 20, requiring federal companies to implement mitigations inside 24 hours
Appearing Government Assistant Director Chris Butera confirmed CISA was alerted by a trusted companion and instantly coordinated with Microsoft.
“We’re witnessing an pressing and lively risk,” warned Lotem Finkelstein, Director of Menace Intelligence at Verify Level Analysis. “Our workforce has confirmed dozens of compromise makes an attempt throughout authorities, telecom, and tech sectors since July 7.”
Safety researchers estimate over 10,000 SharePoint servers worldwide stay weak, with the best concentrations in america, Netherlands, United Kingdom, and Canada.
Eye Safety, which first disclosed the lively exploitation, reported scanning greater than 8,000 SharePoint servers globally and discovering proof of ongoing assaults in a number of waves.
The ToolShell exploit chain demonstrates refined ways, starting with specifically crafted POST requests to SharePoint’s weak ToolPane.aspx endpoint.
Attackers manipulate the Referer header to bypass authentication, then add malicious ASPX information sometimes named “spinstall0.aspx” to extract crucial cryptographic keys from the server.
These stolen ValidationKeys and DecryptionKeys allow attackers to forge professional authentication tokens, sustaining persistent entry even after patching.
The approach permits risk actors to execute PowerShell instructions by means of SharePoint’s IIS employee course of (w3wp.exe), typically working underneath NT AUTHORITYIUSR privileges.
“The vulnerability basically breaks SharePoint’s safety mannequin,” defined researchers at Strobes Safety. “As soon as exploited, attackers can steal SharePoint’s cryptographic MachineKey configuration, granting persistent entry indefinitely.”
Emergency Patches and Mitigation Steering
Microsoft launched emergency safety updates on July 21 for SharePoint Server Subscription Version (KB5002768) and SharePoint Server 2019 (KB5002754), with language pack updates additionally accessible. Nonetheless, SharePoint Server 2016 stays weak, with Microsoft working to develop complete patches.
To mitigate potential assaults, prospects ought to:
Use supported variations of on-premises SharePoint Server
Apply the newest safety updates linked above.
Deploy Microsoft Defender for Endpoint safety, or equal risk options
Make sure the Antimalware Scan Interface (AMSI) is turned on and configured accurately, with an applicable antivirus resolution equivalent to Defender Antivirus
Rotate SharePoint Server ASP.NET machine keys.
Microsoft Defender Unified Superior Searching question
DeviceTvmSoftwareVulnerabilities| the place CveId in (“CVE-2025-49706″,”CVE-2025-53770”)
To Verify for Profitable exploitation by way of file creation
DeviceFileEvents| the place FolderPath has_any (@’microsoft sharedWeb Server Extensions16TEMPLATELAYOUTS’, @’microsoft sharedWeb Server Extensions15TEMPLATELAYOUTS’)| the place FileName has “spinstall0″| venture Timestamp, DeviceName, InitiatingProcessFileName, InitiatingProcessCommandLine, FileName, FolderPath, ReportId, ActionType, SHA256| order by Timestamp desc
To verify for course of creation
DeviceProcessEvents| the place InitiatingProcessFileName has “w3wp.exe”and InitiatingProcessCommandLine !has “DefaultAppPool”and FileName =~ “cmd.exe”and ProcessCommandLine has_all (“cmd.exe”, “powershell”)and ProcessCommandLine has_any (“EncodedCommand”, “-ec”)| prolong CommandArguments = cut up(ProcessCommandLine, ” “)| mv-expand CommandArguments to typeof(string)| the place CommandArguments matches regex “^[A-Za-z0-9+/=]{15,}$”| prolong B64Decode = substitute(“x00”, “”, base64_decodestring(tostring(CommandArguments))) | the place B64Decode has_any (“spinstall0”, @’C:PROGRA~1COMMON~1MICROS~1WEBSER~115TEMPLATELAYOUTS’, @’C:PROGRA~1COMMON~1MICROS~1WEBSER~116TEMPLATELAYOUTS’)
The fast development from proof-of-concept demonstration to mass exploitation occurring inside simply 72 hours highlights the evolving risk panorama the place zero-day vulnerabilities could be weaponized nearly immediately. Organizations are urged to deal with this as an emergency-priority incident requiring quick motion to forestall compromise.
Increase detection, cut back alert fatigue, speed up response; all with an interactive sandbox constructed for safety groups -> Attempt ANY.RUN Now