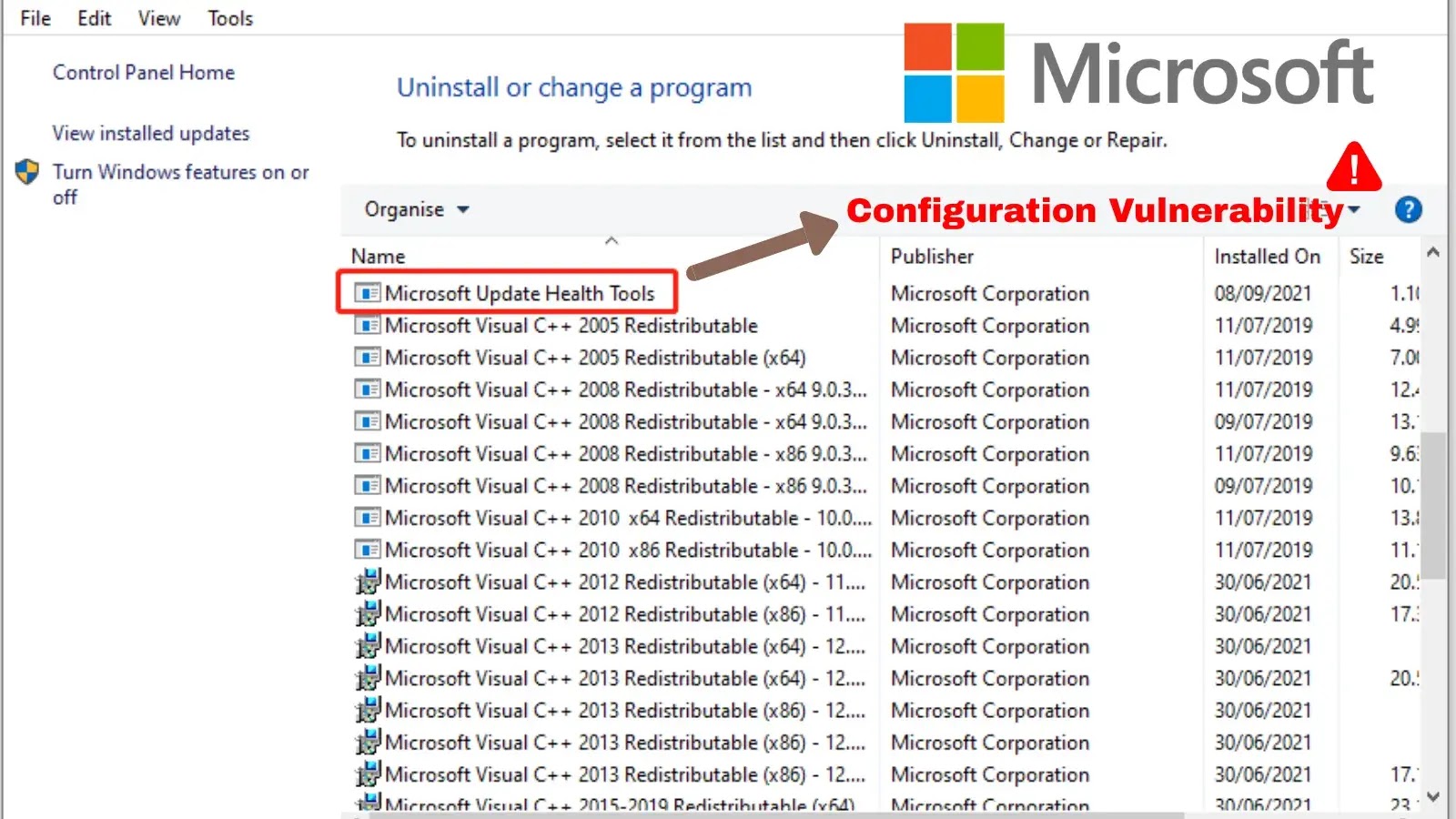
A vital distant code execution (RCE) vulnerability in Microsoft’s Replace Well being Instruments (KB4023057). A broadly deployed Home windows element designed to expedite safety updates by Intune.
The flaw stems from the device connecting to dropped Azure Blob storage accounts that attackers may register and management.
How the Vulnerability Works
The vulnerability exists in model 1.0 of the Replace Well being Instruments, which makes use of Azure Blob storage accounts following a predictable naming sample (payloadprod0 by payloadprod15.blob.core.home windows.web) to fetch configuration information and instructions.
Eye Safety researchers discovered that Microsoft had left 10 of the 15 storage accounts unregistered and unused.
After registering these deserted endpoints, the researchers noticed over 544,000 HTTP requests inside seven days from almost 10,000 distinctive Azure tenants worldwide.
The device’s uhssvc.exe service, positioned at C:Program FilesMicrosoft Replace Well being Instruments, was actively resolving these domains throughout a number of enterprise environments.
uhssvc.exe file
The vital subject lies within the device’s “ExecuteTool” motion, which permits execution of Microsoft-signed binaries.
By crafting malicious JSON payloads that time to respectable Home windows executables corresponding to explorer.exe, attackers can obtain arbitrary code execution on susceptible techniques.
The newer model 1.1 implements a correct net service at devicelistenerprod.microsoft.com, although backward-compatibility choices may nonetheless expose techniques.
Eye Safety reported the vulnerability to Microsoft on July 7, 2025, and Microsoft confirmed the habits on July 17.
Hashicorp researchers transferred possession of all compromised storage accounts again to Microsoft on July 18, 2025, successfully closing the assault vector.
Organizations ought to guarantee they’re operating the newest model of Replace Well being Instruments and confirm no legacy configurations stay enabled.
Safety groups ought to monitor for uncommon community site visitors to Azure Blob storage endpoints from replace providers.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.