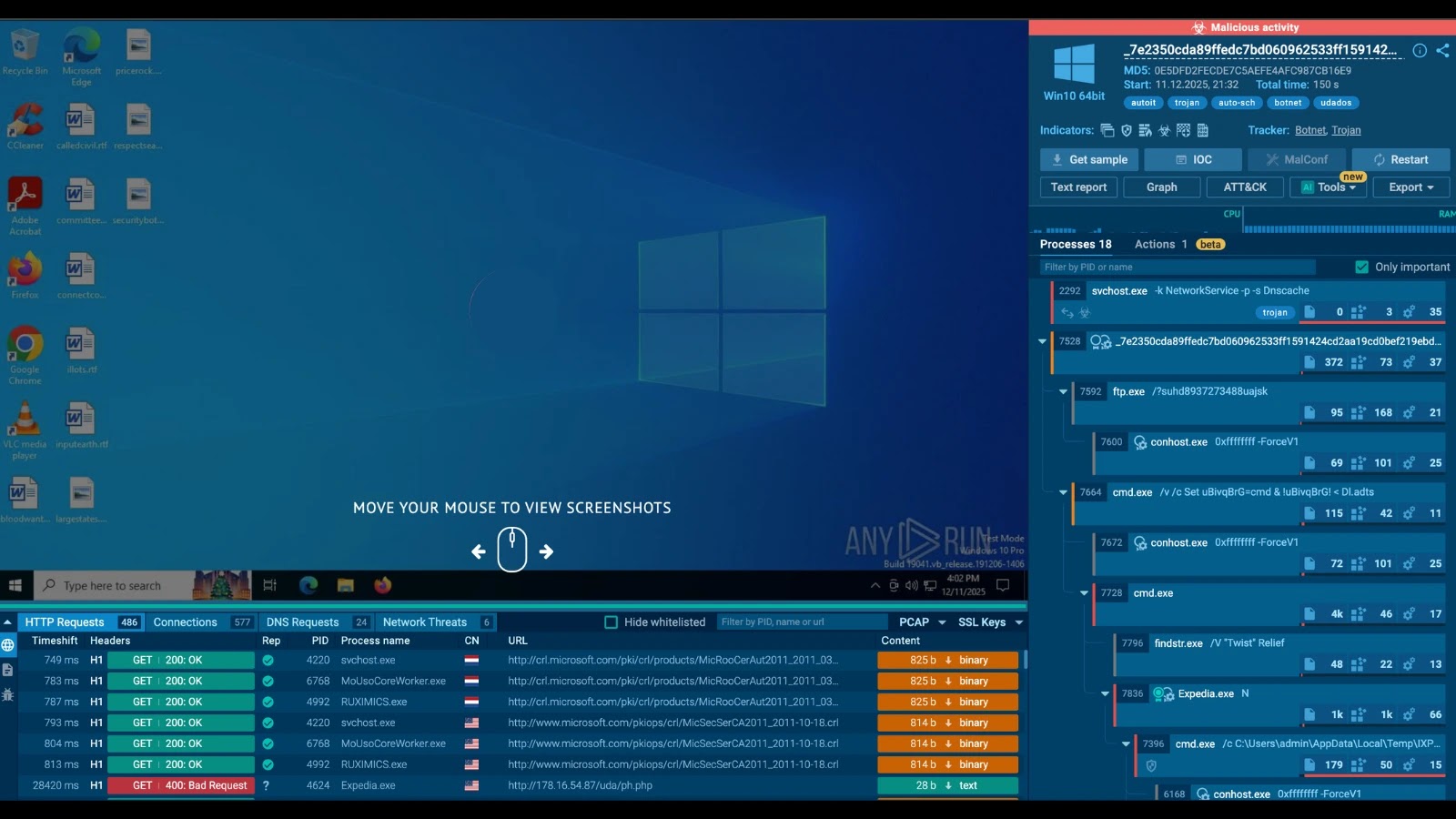
As we navigate by 2025, cybersecurity professionals face an more and more subtle risk panorama. Community Intrusion Detection Methods (IDS) have grow to be important guardians towards evolving digital threats that concentrate on organizations worldwide.
With cybercrime prices projected to surge from $9.22 trillion in 2024 to $13.82 trillion by 2028, the race between attackers and defenders has by no means been extra essential.
Rising Cyber Threats Reshaping the 2025 Panorama
The cybersecurity panorama in 2025 is dominated by a number of subtle threats that conventional safety measures battle to fight.
AI-driven malware has emerged as a big concern, with criminals now utilizing machine studying to mutate malicious code in actual time, avoiding static detection strategies.
This know-how allows malware to deepen its set up, detect sandbox environments, and adapt to endpoint defenses.
Ransomware continues to evolve, with 2025 witnessing a surge in subtle operations concentrating on essential infrastructure, healthcare programs, and monetary establishments.
The rise of Ransomware-as-a-Service (RaaS) has lowered the barrier to entry, making a surge of assaults, with the typical price of restoration now reaching $2.73 million.
Maybe most regarding is the impression of generative AI on cyber threats. Practically 47% of organizations cite adversarial advances powered by generative AI as their main concern.
These instruments allow extra subtle and scalable assaults, notably in social engineering. In 2024, 42% of organizations reported such incidents.
AI-Powered Intrusion Detection: The New Protection Paradigm
As threats evolve, so too should protection mechanisms. Trendy intrusion detection programs have embraced synthetic intelligence and machine studying to detect and stop cyber threats in real-time.
These AI-IDS options be taught from patterns, establish unknown threats, and considerably cut back false alarms, making them important for shielding networks and delicate information.
An Enhanced Anomaly Intrusion Detection utilizing Optimization Algorithm with Dimensionality Discount and Hybrid Mannequin (EAID-OADRHM) represents the innovative of those applied sciences.
This method leverages min-max scaling normalization, equilibrium optimizer fashions for dimensionality discount, and lengthy short-term reminiscence and autoencoder fashions for classification, leading to superior accuracy in risk detection.
Market Leaders Driving Innovation
In 2025, a number of options are main the market with superior options designed to fight rising threats:
Darktrace stands out with its self-learning AI, which makes it extremely efficient in detecting unknown and rising threats. Its automated risk response capabilities and real-time community monitoring present organizations complete safety towards subtle assaults.
Vectra AI provides superior accuracy in figuring out hidden attackers by its cloud-native IDS that makes use of behavioral evaluation. Its incident response automation capabilities make it notably useful for organizations in search of to cut back response occasions.
Cisco Safe IDS combines synthetic intelligence with community safety, offering superior intrusion detection that seamlessly integrates with Cisco’s broader safety ecosystem. This integration permits for extra complete safety protection throughout numerous environments.
The Rising IDS Market
The intrusion detection market is experiencing important development, with projections indicating a Compound Annual Progress Price (CAGR) of 5.4% by 2025.
This growth is pushed by rising demand for revolutionary applied sciences, together with clever video verification, wi-fi options, and seamless integration capabilities.
Cloud-based options are gaining specific traction. Google Cloud’s Intrusion Detection System detects network-based threats at each community and utility layers, together with malware, spy ware, and command-and-control assaults.
These cloud-native, managed providers present industry-leading safety with out the draw back of managing advanced infrastructure.
Geopolitical Components Influencing IDS Adoption
Geopolitical tensions are more and more influencing cybersecurity technique in 2025, with almost 60% of organizations stating that such tensions have affected their method.
These geopolitical components have altered threat perceptions, with one in three CEOs citing cyber espionage and lack of delicate info as their prime concern.
As organizations adapt to this difficult panorama, community intrusion detection programs have grow to be a non-negotiable element of complete safety methods.
With their potential to detect, stop, and reply to classy assaults in real-time, these programs symbolize the primary and most important line of protection towards the ever-evolving risk panorama of 2025.
Discover this Information Attention-grabbing! Comply with us on Google Information, LinkedIn, & X to Get On the spot Updates!