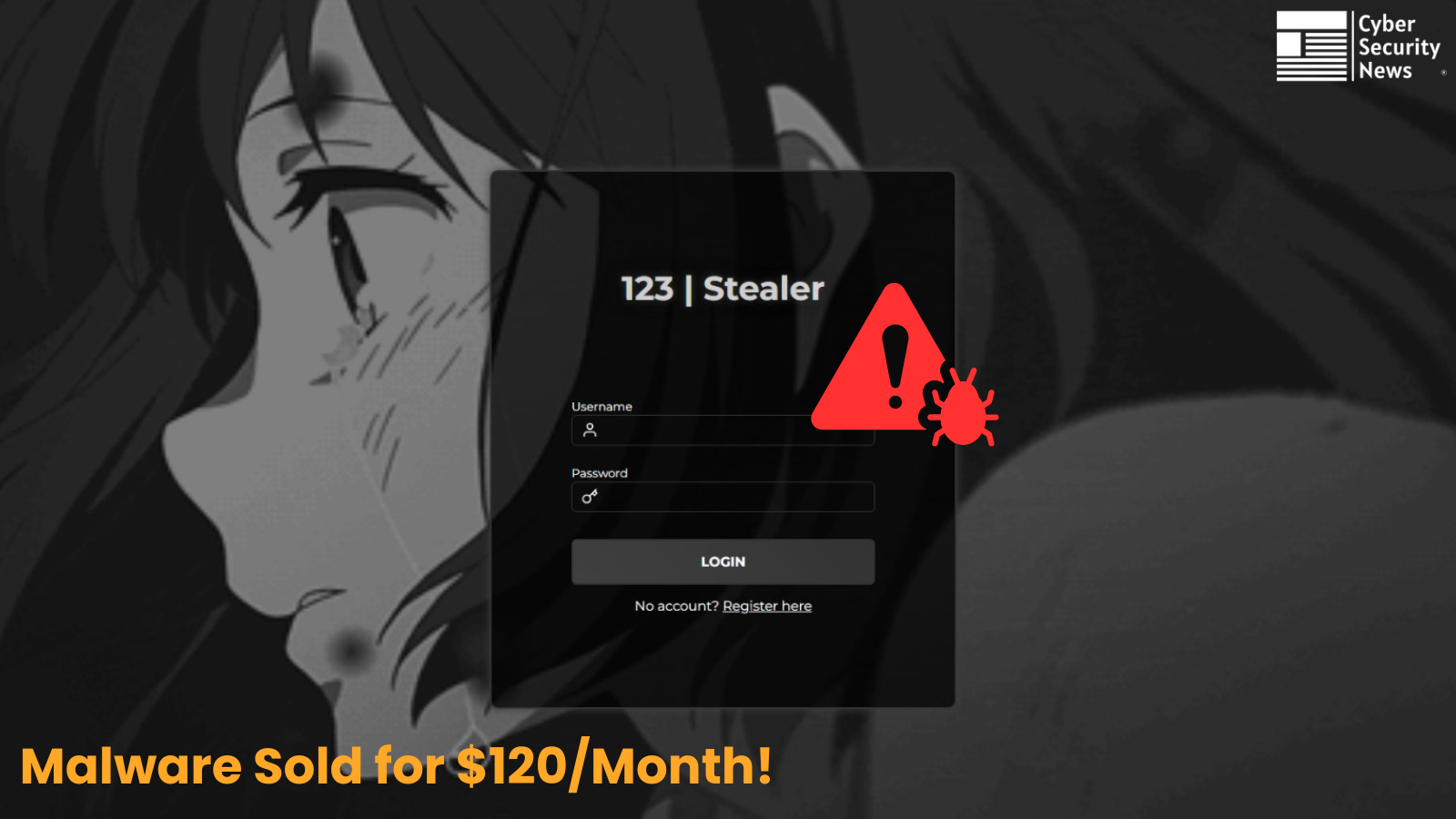
A brand new credential-stealing malware dubbed “123 | Stealer” has surfaced on underground cybercrime boards, being marketed by risk actor “koneko” for $120 per 30 days.
This malware-as-a-service (MaaS) providing represents the most recent evolution in data stealer know-how, combining refined information exfiltration capabilities with a user-friendly administrative interface.
Key Takeaways1. “123 | Stealer” marketed for $120/month by risk actor “koneko” on underground boards.2. C++ coded, DLL-free (~700KB), helps 70+ browser extensions, requires self-hosted proxy servers.3. Steals browser information, passwords, crypto wallets, Discord accounts, and performs file/course of grabbing.4. Skilled presentation however lacks cybercriminal evaluations, making effectiveness unsure
The stealer targets a complete vary of delicate information, demonstrating the rising commercialization of cybercrime instruments.
In keeping with the discussion board commercial, the malware harvests browser information, cookies, saved passwords, cryptocurrency pockets data, and browser extensions.
The risk actor claims the stealer also can carry out course of grabbing and file grabbing operations, making it a flexible instrument for information theft operations.
Risk actor Koneko Gives $120/Month Credential Stealer
123 | Stealer Bypasses AV, Targets Browsers and Crypto Wallets
In keeping with the Kraken Labs report, 123 | Stealer is written in C++, a programming language selection that implies builders prioritized efficiency and low-level system entry.
The malware encompasses a DLL-free stub structure, weighing roughly 700KB, which makes it harder to detect by conventional antivirus options that depend on dynamic hyperlink library (DLL) injection detection strategies.
One notable side is the proxy server requirement. Customers should set up their very own proxy infrastructure utilizing Ubuntu or Debian-based servers, indicating a classy command and management (C2) structure.
Concentrating on browsers
This method permits malware operators to take care of operational safety (OPSEC) whereas distributing infrastructure burden to prospects.
The executive panel reveals in depth browser assist, together with compatibility with over 70 browser extensions.
The stealer targets main Chromium-based browsers reminiscent of Google Chrome, Opera, and Chromium itself, in addition to Gecko-based browsers like Firefox variants.
Standard purposes, together with Discord, Battle.web, and varied cryptocurrency wallets, are additionally throughout the malware’s scope.
Mid-Tier Risk, Prices $120 Month-to-month
The $120 month-to-month subscription mannequin positions 123 | Stealer within the mid-tier market phase of knowledge stealers.
This pricing technique targets each novice cybercriminals and skilled risk actors in search of dependable information exfiltration instruments. The subscription mannequin ensures recurring income for malware authors whereas offering steady updates and assist to prospects.
The discussion board commercial emphasizes that customers are accountable for any detection or drive majeure occasions, indicating that malware authors are trying to restrict their legal responsibility.
Moreover, the service explicitly prohibits operations in Russia, CIS nations, and former Soviet republics, a standard restriction amongst cybercrime providers.
At present, the malware has not obtained public evaluations from different cybercriminals on the discussion board, making its precise effectiveness unverified.
Nevertheless, the skilled presentation of the login interface and complete administrative panel suggests vital improvement funding, indicating this can be a severe risk reasonably than a rip-off operation.
Safety researchers and organizations ought to monitor for 123 | Stealer samples and replace detection signatures to guard towards this rising risk.
Examine stay malware habits, hint each step of an assault, and make sooner, smarter safety selections -> Strive ANY.RUN now