AmCache performs a significant position in figuring out malicious actions in Home windows programs. This software permits the identification of each benign and malicious software program execution on a machine.
Managed by the working system and just about tamper-proof, AmCache knowledge endures even when malware auto-deletes itself, making it indispensable in incident response.
AmCache shops SHA-1 hashes of executed information, enabling DFIR professionals to question public menace intelligence feeds corresponding to OpenTIP and VirusTotal and quickly generate indicators of compromise for blocking throughout the community.
The brand new open-source software, launched by Kaspersky researchers, simplifies the parsing of the Amcache.hve registry hive, automating IOC extraction and menace intelligence lookups to speed up menace detection and containment.
AmCache-EvilHunter is a command-line utility written in Python that ingests the C:WindowsAppCompatProgramsAmcache.hve file and extracts key metadata entries.
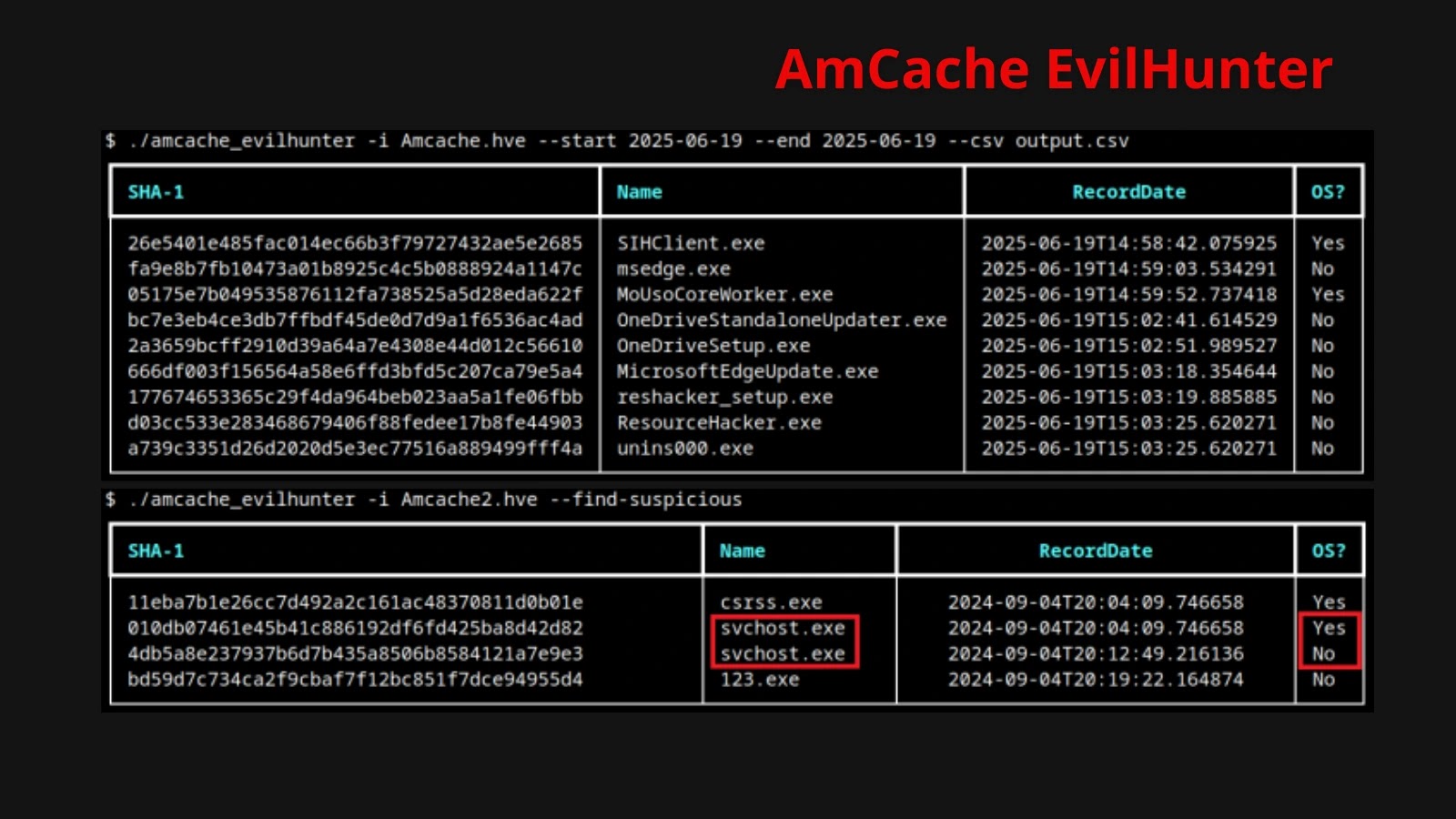
It parses crucial registry keys InventoryApplicationFile, InventoryDriverBinary, InventoryApplication, and InventoryApplicationShortcut—to disclose file paths, writer knowledge, LinkDate timestamps, binary varieties (32-bit vs. 64-bit), and SHA-1 hashes. A pattern invocation appears to be like like this:
Fundamental utilization of AmCache-EvilHunter
This command filters information by date vary, outputting a CSV of all executables current between September 1 and September 30, 2025.
CSV end result
The FileID discipline comprises the hash with 4 main zeroes, whereas Dimension and IsOsComponent flags assist analysts distinguish system binaries from potential malware.
Kaspersky said that AmCache-EvilHunter’s standout options embrace built-in menace intelligence integration and superior filtering choices.
The –find-suspicious flag applies heuristics—corresponding to one-letter names (1.exe), random hex filenames, and customary typo variants like scvhost.exe to focus on anomalous entries.
Suspicious information identification
Extra flags, –missing-publisher and –exclude-os, additional cut back noise by filtering out signed OS elements. For every recognized hash, customers can invoke:
This triggers automated lookups towards VirusTotal and Kaspersky OpenTIP, appending detection counts and menace classification tags to the output.
Analysts may search particular key phrases or ProgramId values utilizing –search “winscp.exe” to substantiate the presence of deleted or transient instruments.
AmCache-EvilHunter makes use of the Registry Python library to load the REGF-formatted hive whereas iterating by way of its subkeys and values.
Its modular structure permits builders to increase help for customized IOC feeds or combine with SOAR platforms. Binaries and scripts can be found on GitHub for each Home windows and Linux deployments.
By automating parsing, filtering, and menace lookups, AmCache-EvilHunter considerably cuts guide effort and accelerates DFIR workflows.
Incident responders can quickly reconstruct execution timelines, pinpoint stealthy rootkits through InventoryDriverBinary, and generate sturdy IOCs from InventoryApplicationFile entries.
As adversaries more and more make use of self-erasing malware, this software ensures that essential execution proof isn’t misplaced.
Observe us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to function your tales.