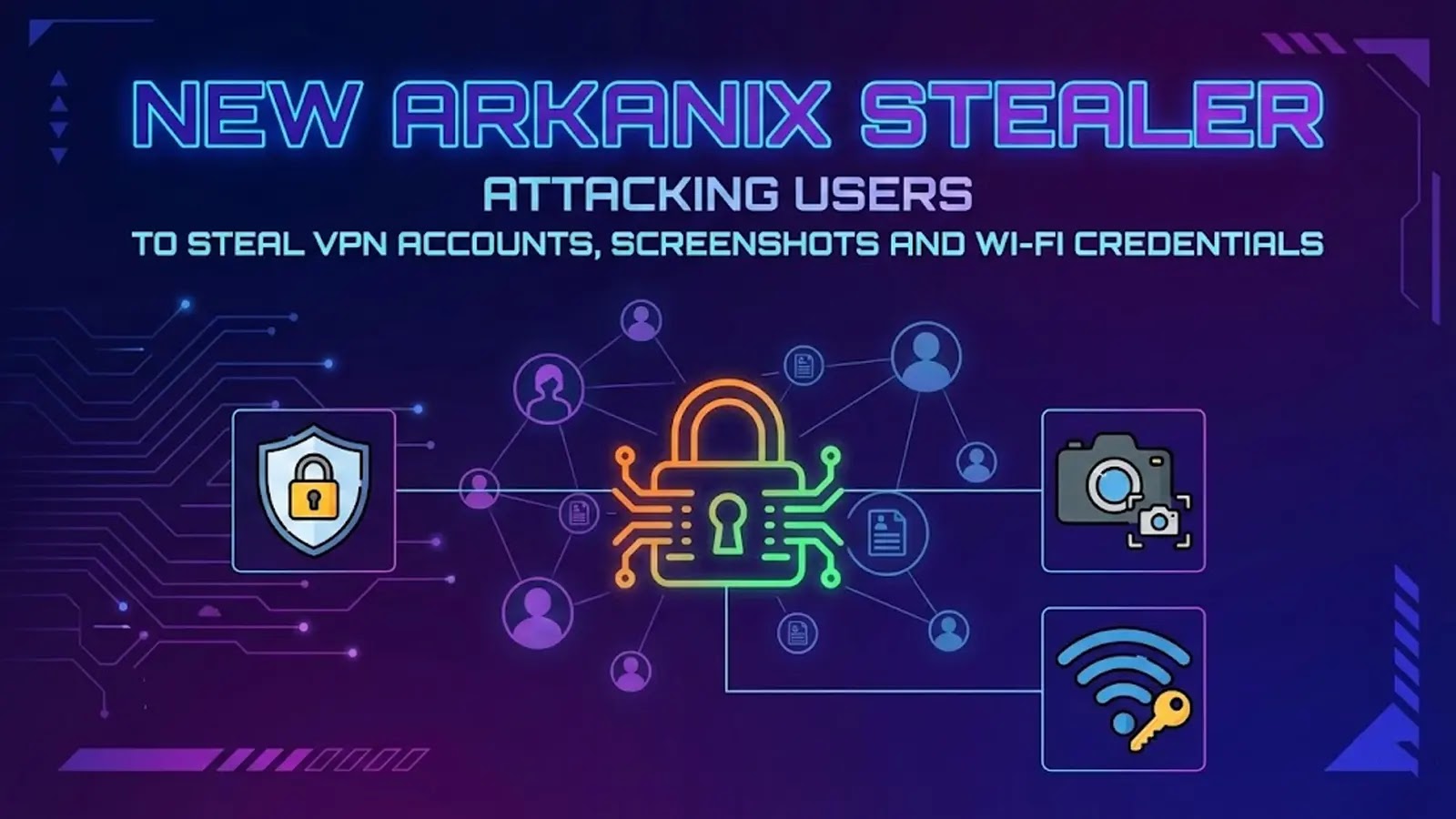
The Arkanix stealer is a brand new malware household now spreading within the wild. It targets house customers and small workplaces that depend on VPN shoppers and wi-fi networks for every day work.
As soon as energetic, it focuses on stealing VPN account knowledge, Wi‑Fi profiles, browser credentials, and desktop screenshots.
This provides attackers direct entry to non-public networks and a transparent view of what the sufferer is doing.
Early assaults use easy however efficient lures. Victims are tricked via pretend software program downloads, cracked instruments, or e-mail hyperlinks that drop a small loader.
This loader then pulls the primary Arkanix payload from a distant server and runs it with out drawing consideration.
The entire chain is constructed to seem like a standard installer, which helps it mix into routine person exercise.
G Information Cyber Protection safety analysts recognized Arkanix throughout an investigation into new data‑stealing campaigns.
Their telemetry confirmed repeated theft of VPN profiles and Wi‑Fi keys from techniques in Europe and different areas, with the identical code base behind the assaults.
Additional evaluation revealed a modular design that lets operators change targets shortly, from browser knowledge to screenshots or different recordsdata.
As soon as loaded, Arkanix scans the system for VPN configuration recordsdata, password shops, and saved wi-fi profiles. It exports them right into a single archive, provides contemporary screenshots from the energetic desktop, after which sends the whole lot to a command‑and‑management (C2) server.
Internet panel login display screen (Supply – G Information)
Community captures present outbound HTTPS requests that disguise this theft inside encrypted visitors, making it tougher to identify.
An infection chain and knowledge theft
The principle binary runs easy however centered code to gather knowledge. A typical sample is a loop that walks recognized paths for VPN and Wi‑Fi knowledge, then posts them to the C2 endpoint:-
for every(path in target_paths){
grab_files(path);
}
take_screenshot();
upload_to_c2(zip_all());
A configuration panel utilized by the malware writer controls which modules run, similar to Wi‑Fi theft or screenshot seize.
Configuration choices (Supply – G Information)
This whole technical breakdown reveals that Arkanix is constructed for direct entry: steal VPN accounts, map Wi‑Fi networks, watch the display screen, after which let intruders transfer into these environments with little or no effort.
Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates, Set CSN as a Most well-liked Supply in Google.