Safety researchers at ANY.RUN have uncovered a brand new malware marketing campaign delivering the BRAODO Stealer, which depends on public GitHub repositories to host and stage its payloads.
This marketing campaign employs a number of evasion strategies and scripting layers to complicate detection and evaluation, making it more durable for conventional safety instruments to catch.
What We Know About BRAODO Stealer
BRAODO is designed to steal information. On the time of study, it was able to exfiltrating delicate data whereas retaining a low profile.
The ultimate payload is written in Python, obfuscated with pyobfuscate, and accommodates customized Base64-encoded strings appended to the script, doubtless used to cover credentials or configuration information.
It doesn’t use encryption or packers. As an alternative, it hides within the noise of on a regular basis scripting instruments and depends on staged supply to keep away from detection.
Every stage cleans up after itself, lowering the variety of artifacts left behind. As soon as executed, the stealer quietly deletes the preliminary archive and will get to work.
Step-by-Step Breakdown Of The BRAODO Assault
Let’s take a better have a look at the total assault chain utilizing the ANY.RUN sandbox session talked about beneath.
The interactive atmosphere makes it doable to securely observe every stage of the assault, from the preliminary script execution to the ultimate payload supply.
For safety groups, this type of visibility is essential. It helps analysts hint malicious habits in actual time, perceive how threats evolve throughout phases, and accumulate clear proof, all with out exposing manufacturing techniques to threat.
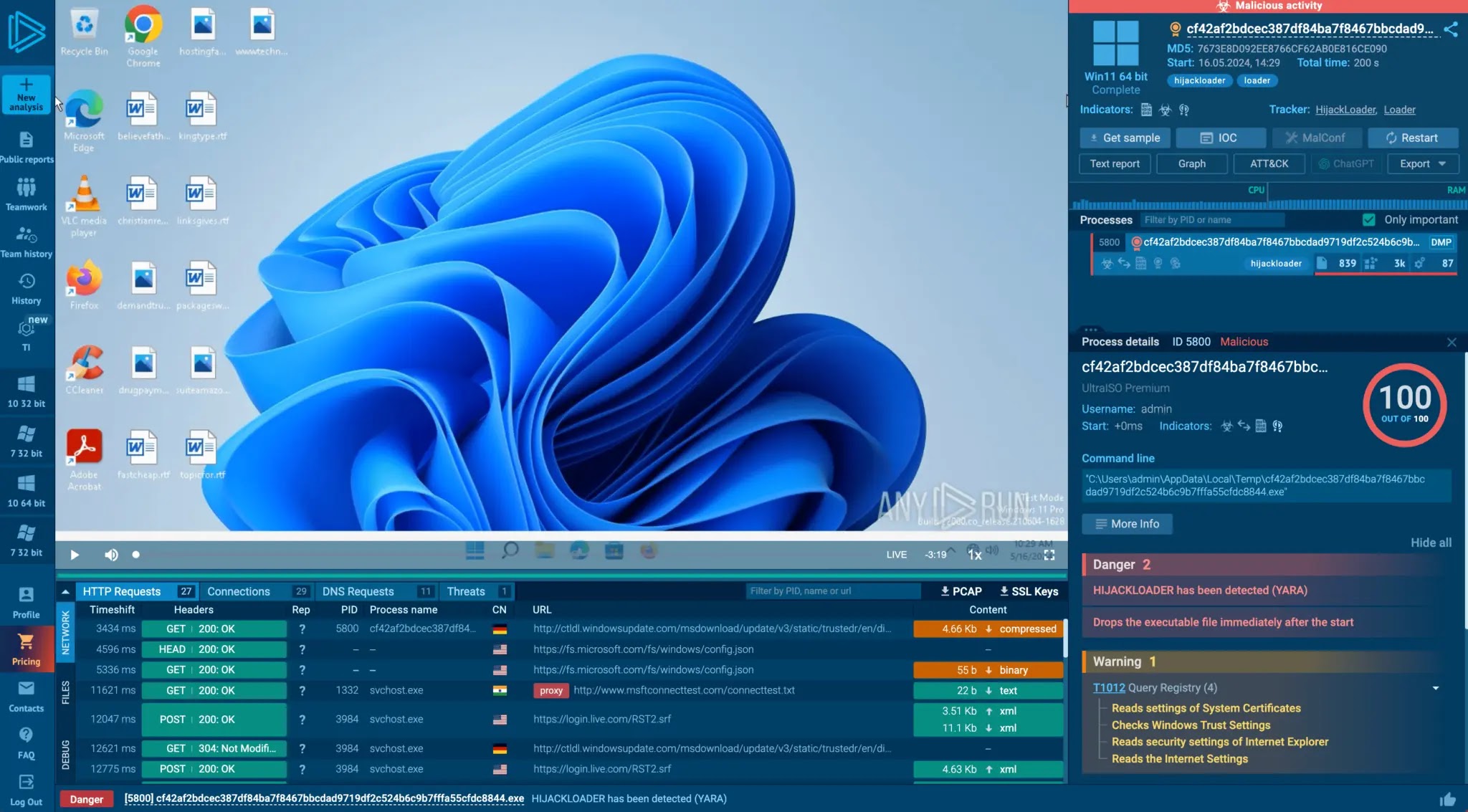
View evaluation session with BRAODO Stealer
BRAODO Stealer detected inside ANY.RUN sandbox
Preliminary BAT File
The marketing campaign begins with the execution of a .BAT file. Whereas it could look innocent at first look, the script features a command that launches PowerShell utilizing cmd.exe.
Importantly, PowerShell is run in hidden mode, that means no console window seems, retaining the method invisible to the person. This step marks the beginning of a silent, multi-stage an infection chain.
The BAT recordsdata used on this marketing campaign are obfuscated and include deceptive feedback to hinder evaluation
Examine malware in actual time, uncover each stage of an assault, and make sooner safety choices; all in a secure and intuitive atmosphere. -> Strive ANY.RUN now
Obtain From GitHub
Utilizing PowerShell, the malware reaches out to a public GitHub repository to obtain the subsequent stage.
The downloaded file is one other BAT script, however it’s deliberately disguised as a .PNG file, prone to bypass detection and lift fewer suspicions in transit or at relaxation.
The file is saved to the %temp% listing and instantly executed, persevering with the an infection. This exercise is clearly captured in ANY.RUN’s Script Tracer.
.bat file found by ANY.RUN’s Script Tracer
Script Tracer robotically maps these actions with out requiring handbook deobfuscation or digging via uncooked logs.
It exhibits every operate name, obtain URL, and execution timestamp, serving to analysts rapidly reconstruct the malware’s habits with minimal effort.
Cleanup And Persistence
As soon as the second-stage BAT file runs, it launches one other PowerShell script. This script performs a number of duties:
Removes artifacts from the sooner phases to make evaluation tougher.
Forces TLS 1.2 to make sure encrypted connections to the distant host.
Downloads an extra payload from uncooked.githubusercontent[.]com, once more abusing GitHub’s uncooked content material supply.
GitHub abuse seen with the assistance of ANY.RUN’s Script Tracer
Drops this payload into the Startup folder, permitting it to robotically run when the system reboots.
Creation of recordsdata in Startup listing uncovered inside ANY.RUN sandbox
This step ensures persistence and helps preserve management over the contaminated system.
Closing Payload In ZIP
Subsequent, the script downloads the primary malware element, the BRAODO Stealer, which is delivered as a ZIP archive.
The ZIP file is extracted into the C:UsersPublic listing, a generally abused location in malware campaigns because of its low visibility.
This motion will also be seen in ANY.RUN’s Script Tracer:
.zip file extracted into the Public listing, detected inside ANY.RUN sandbox
The extracted Python script is then executed utilizing python.exe. At this level, the BRAODO stealer turns into energetic on the system and begins finishing up its meant duties, particularly, information assortment and exfiltration.
The script itself is obfuscated with pyobfuscate and accommodates appended Base64-encoded strings, which can maintain configuration particulars or embedded payloads.
Put up-Execution Cleanup
After execution, the script deletes the unique ZIP archive, wiping one of many few traces left behind. This cleanup step makes forensic evaluation tougher and helps the malware stay undetected longer.
Nonetheless, inside ANY.RUN’s interactive sandbox, each stage of the assault is clearly logged and traceable.
Analysts can view the total execution chain intimately, from the preliminary script to the ultimate cleanup, making it a lot simpler to grasp the stealer’s habits and collect indicators of compromise.
What This Assault Means For Analysts, SOC Groups, And Companies
The BRAODO Stealer marketing campaign highlights a rising pattern: attackers are leaning on authentic platforms like GitHub and on a regular basis scripting instruments to quietly transfer via
techniques. For various roles throughout cybersecurity and enterprise, this has particular implications:
For analysts: Multi-stage threats like BRAODO require full visibility throughout scripts, file actions, and system adjustments. Instruments like ANY.RUN assist velocity up investigations by mapping every step robotically.
For SOC groups: Relying solely on static detection or conventional endpoint instruments isn’t sufficient. Visibility into real-time habits, particularly throughout preliminary entry and payload deployment, is crucial to catch stealthy malware early.
For companies: A single malicious script embedded in an electronic mail or file can result in full system compromise.
Worker gadgets, cloud entry, and weak lateral monitoring make stealthy stealers like BRAODO an actual menace to delicate information and compliance.
Whether or not you’re defending a small community or monitoring a whole bunch of endpoints, real-world evaluation like this can assist you keep forward of evolving threats earlier than they slip via the cracks.
Detect Threats Sooner Earlier than They Trigger Harm
Campaigns like BRAODO present how trendy malware is constructed to mix in. Nonetheless, with the best instruments, even essentially the most layered, stealthy infections may be uncovered in minutes.
ANY.RUN’s interactive sandbox helps safety groups:
Detect threats early earlier than they will escalate into breaches
Velocity up investigations by giving analysts full visibility into suspicious habits
Cut back response time with clear insights that get rid of guesswork
Make higher choices with context-rich evaluation you possibly can belief
Shield your infrastructure by testing malware in a secure, remoted atmosphere
Collaborate extra successfully with shared classes and team-based workflows
Begin your 14-day trial of ANY.RUN and expertise full visibility into malware habits in a secure, managed atmosphere.