BruteForceAI, an revolutionary penetration testing framework developed by Mor David, integrates massive language fashions (LLMs) with browser automation to autonomously determine login kinds and conduct subtle brute-force assaults.
By combining AI-driven type evaluation with evasion strategies and complete logging, BruteForceAI streamlines credential-testing workflows, enabling safety groups to uncover weak authentication mechanisms quickly and effectively.
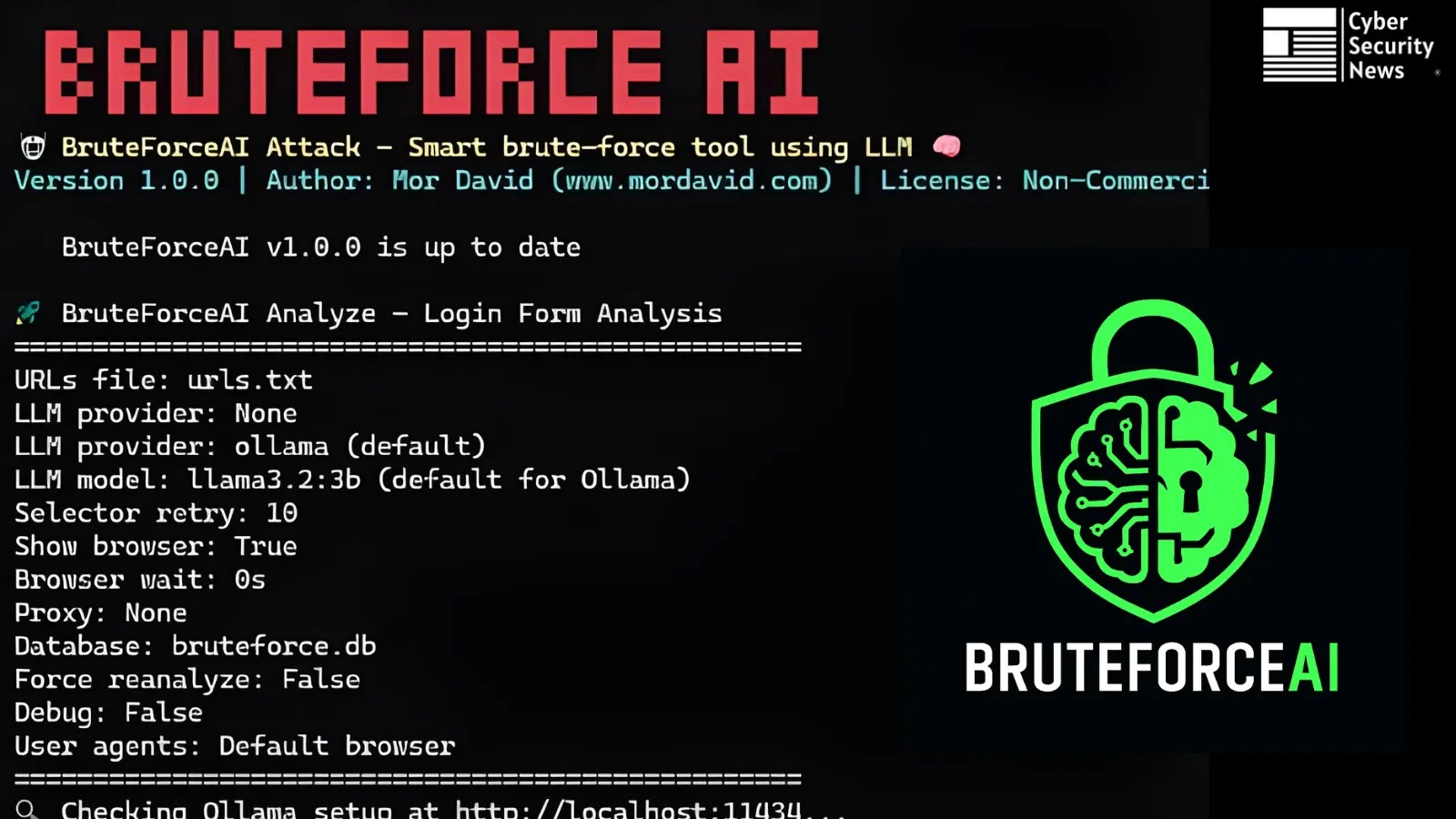
On the core of BruteForceAI lies its two-stage course of. In Stage 1, the device leverages an LLM (through Ollama or Groq) to parse HTML content material and pinpoint login type components and selectors with exceptional accuracy as much as 95% in real-world exams.
The mannequin examines web page buildings, enter fields, and submission endpoints, robotically producing the exact CSS selectors wanted for subsequent exploitation.
Stage 2, the Sensible Assault section, initiates multi-threaded credential testing utilizing the AI-discovered selectors. Customers can select between two modes:
Brute-Drive Mode: Exhaustively cycles by way of username/password combos.
Password-Spray Mode: Exams every password in opposition to a set of usernames to cut back lockouts.
Clever retry logic incorporates suggestions studying and DOM-change detection to validate profitable logins, whereas synchronized delays, jitter, and human-like timing patterns mimic real person habits to evade detection.
BruteForceAI Software Options
BruteForceAI’s superior function set elevates commonplace brute-force instruments with complete evasion and operational capabilities:
Function CategoryCapabilitiesMulti-Threading1–100+ threads with synchronized delays between attemptsEvasion TechniquesRandom Person-Agent rotation, proxy help, configurable jitter, browser visibility controlNotifications & LogsReal-time webhook alerts (Discord/Slack/Groups/Telegram), SQLite database logging, verbose outputOperational ToolsAutomatic replace checks, community retry mechanism, database cleanup, coloured terminal interface
Webhook integration ensures fast notification upon credential success, whereas complete SQLite logging maintains detailed information of each try.
BruteForceAI additionally helps output seize to recordsdata and gives a collection of database administration instructions, together with clean-up and schema inspection.
Set up requires Python 3.8+, Playwright browsers, and commonplace libraries (requests, PyYAML). After cloning the repository from GitHub and operating pip set up -r necessities.txt, customers configure their most popular LLM:
Native (Ollama): Pull llama3.2:3b or llama3.2:1b for balanced or speed-optimized evaluation.
Cloud (Groq): Authenticate with an API key and choose from fashions akin to llama-3.3-70b-versatile (really useful) or options like gemma2-9b-it for light-weight duties.
To investigate targets:
textpython foremost.py analyze –urls targets.txt –llm-provider ollama –llm-model llama3.2:3b
To execute assaults:
textpython foremost.py assault –urls targets.txt –usernames customers.txt –passwords passwords.txt –threads 20 –delay 5 –jitter 2
Moral Issues
BruteForceAI is explicitly designed for licensed penetration testing, safety analysis, and academic functions; misuse in opposition to unauthorized techniques is illegitimate and unethical. Organizations ought to guarantee correct scope and permission earlier than deployment. The writer disclaims legal responsibility for illicit use.
By automating type detection and enriching brute-force methodology with AI-driven intelligence and evasion, BruteForceAI marks a major evolution in credential-testing toolsets enabling purple groups and safety auditors to determine authentication weaknesses with velocity and precision.
Uninterested in Filling Kinds for safety & Compliance questionnaires? Automate them in minutes with 1up! Begin Your Free Trial Now!