The Cybersecuritynews researcher group uncovered a classy social engineering marketing campaign that’s exploiting the general public’s want without cost web entry, utilizing misleading Wi-Fi portals to trick customers into downloading and executing PowerShell-based malware.
Dubbed the “Clickfix” assault, this technique turns a consumer’s personal browser actions towards them to compromise their system underneath the guise of a easy human verification step.
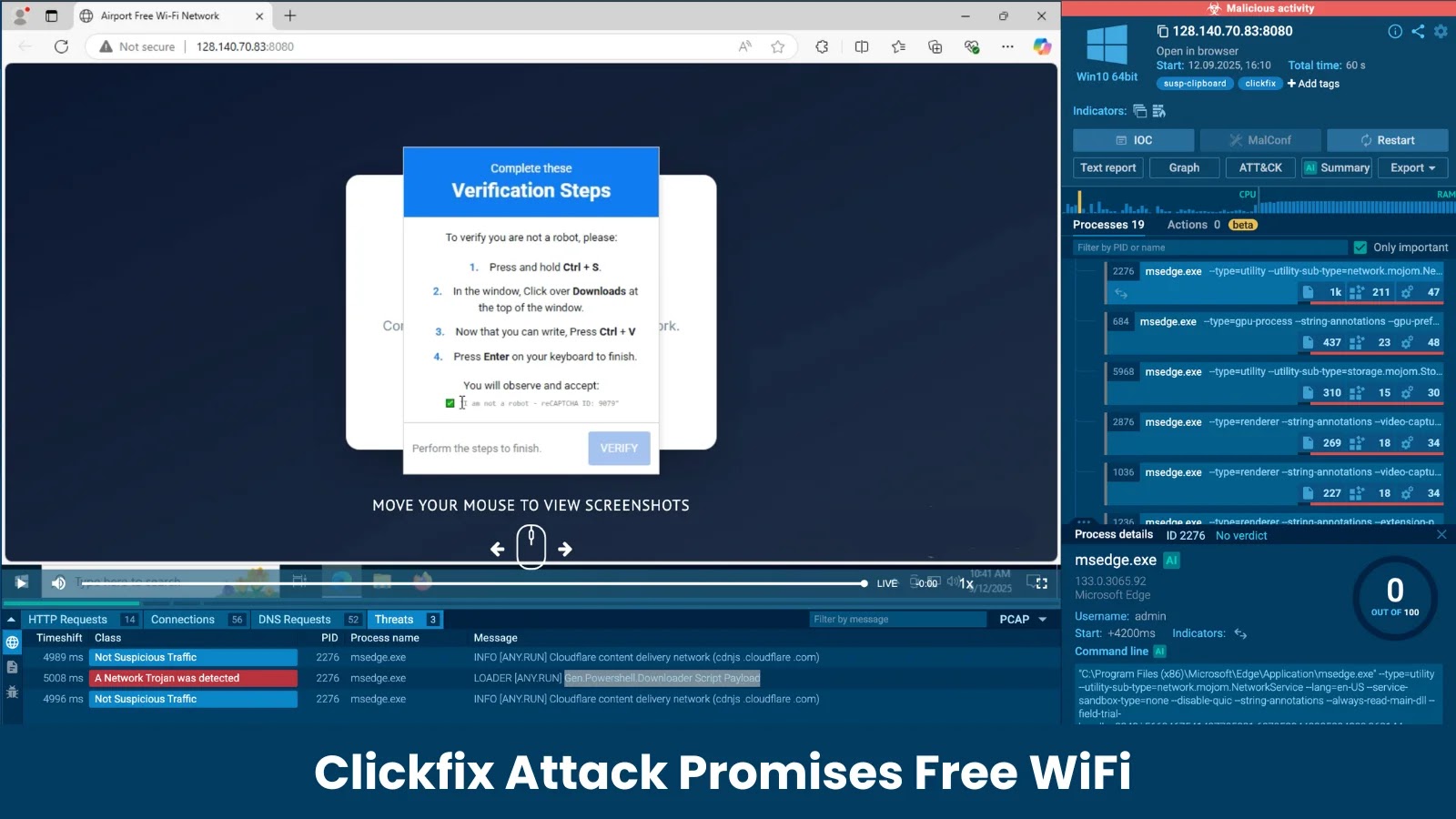
The assault targets on people in public areas like airports, the place the promise of “Free Wi-Fi” is a robust lure. Unsuspecting customers making an attempt to attach are redirected to a professionally designed however pretend captive portal.
Free Wifi Promise (Supply: Cybersecuritynews researcher group)
These pages, typically hosted on insecure IP addresses quite than reputable domains, mimic actual community login screens, full with logos and a CAPTCHA immediate to “show you aren’t a robotic,” a characteristic supposed to construct a false sense of safety.
Misleading Verification Course of
The core of the Clickfix assault lies in its intelligent manipulation of consumer conduct. After a consumer interacts with the pretend CAPTCHA, a pop-up window seems with a set of “Verification Steps.”
As a substitute of a easy click on, the directions information the consumer by way of a particular sequence of keyboard shortcuts: press Ctrl+S to save lots of the net web page, navigate to the browser’s downloads window, and press Enter to open the file, the Cybersecuritynews researcher group stated.
Clickfix popup (Supply: Cybersecuritynews researcher group)
This sequence is a social engineering trick designed to bypass customary browser safety warnings about downloading executable recordsdata.
By instructing the consumer to save lots of the web page and run the file themselves, the attackers successfully get consent to execute malicious code. The downloaded file isn’t a picture or doc however a script that initiates the an infection.
As soon as the consumer unwittingly executes the downloaded file, a malicious PowerShell script is launched.
Evaluation of the assault chain with ANY.RUN Sandbox reveals that this script acts as a downloader, establishing a connection to a command-and-control server to fetch the first malware payload. On this marketing campaign, the payload has been recognized as a community trojan.
File execution (Supply: Cybersecuritynews researcher group)
PowerShell is a robust instrument for attackers as a result of it’s built-in into Home windows and might execute instructions, scripts, and payloads straight in reminiscence, typically evading detection by conventional antivirus options.
The sort of fileless malware can be utilized for a variety of malicious actions, together with stealing delicate data, deploying ransomware, or offering a persistent backdoor for distant entry to the compromised system.
To safeguard towards this risk, customers ought to keep alert when connecting to public Wi-Fi, rigorously look at the URLs of login pages, and be very cautious of any web site that requires uncommon keyboard instructions for verification.
Discover this Story Fascinating! Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates.