A brand new ClickFix marketing campaign is tricking customers with a faux Home windows replace that runs of their browser. Known as “Faux OS Replace,” this rip-off takes benefit of individuals’s belief within the acquainted blue display of dying (BSOD) from Microsoft.
It delivers malware and reveals how social engineering could be more practical than technical methods.
Cybersecurity researcher Daniel B., who works on the UK’s Nationwide Well being Service, first noticed the assault final month whereas probing malicious on-line threats.
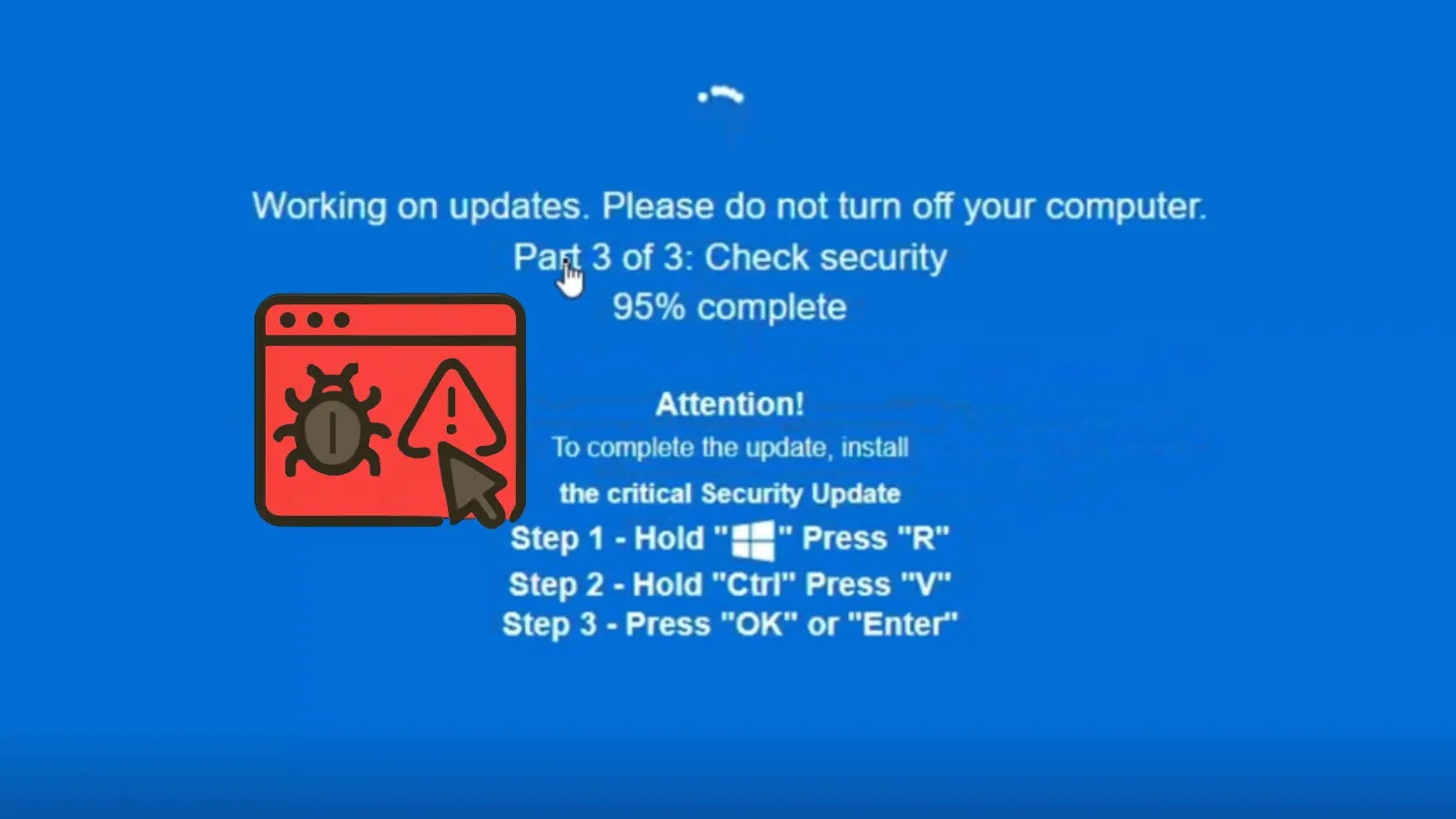
As detailed in his LinkedIn publish, the rip-off operates totally on the area groupewadesecurity[.]com. Merely visiting the positioning typically through malvertising or spam hyperlinks triggers a full-screen overlay mimicking a Home windows OS crash or replace immediate.
The faux BSOD, full with error codes and progress bars, seems on each PCs and smartphones, creating panic and urgency.
What units this other than earlier ClickFix variants is its multi-step deception. After the preliminary display, victims are instructed to carry out three “handbook fixes” utilizing keyboard shortcuts: urgent Ctrl+Alt+Del to “restart companies,” getting into a bogus command in a simulated command immediate, and at last downloading a “restoration device” from a linked malicious web site.
In actuality, these actions grant attackers distant entry or set up infostealers and ransomware loaders. The marketing campaign’s sophistication lies in its cross-device compatibility and avoidance of fast redirects, making it tougher for browser protections to flag.
ClickFix assaults, which trick customers into “fixing” non-existent points through clicks, have plagued browsers since 2020. However as attackers refine their techniques using hyper-realistic graphics, localized languages, and well timed lures tied to actual occasions like Patch Tuesday, this variant proves particularly insidious.
Consultants warn that such campaigns spotlight a essential hole: whereas endpoint detection instruments catch many automated threats, human error stays the weakest hyperlink.
“Person vigilance and common cybersecurity coaching are as very important as firewalls,” notes a spokesperson for the UK’s Nationwide Cyber Safety Centre (NCSC).
Organizations ought to prioritize consciousness packages that simulate these situations, alongside browser extensions equivalent to uBlock Origin to dam suspicious domains.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.