A complicated new cyberthreat marketing campaign has emerged that mixes impersonation of trusted information sources with misleading safety verification prompts to trick customers into executing malicious instructions on their methods.
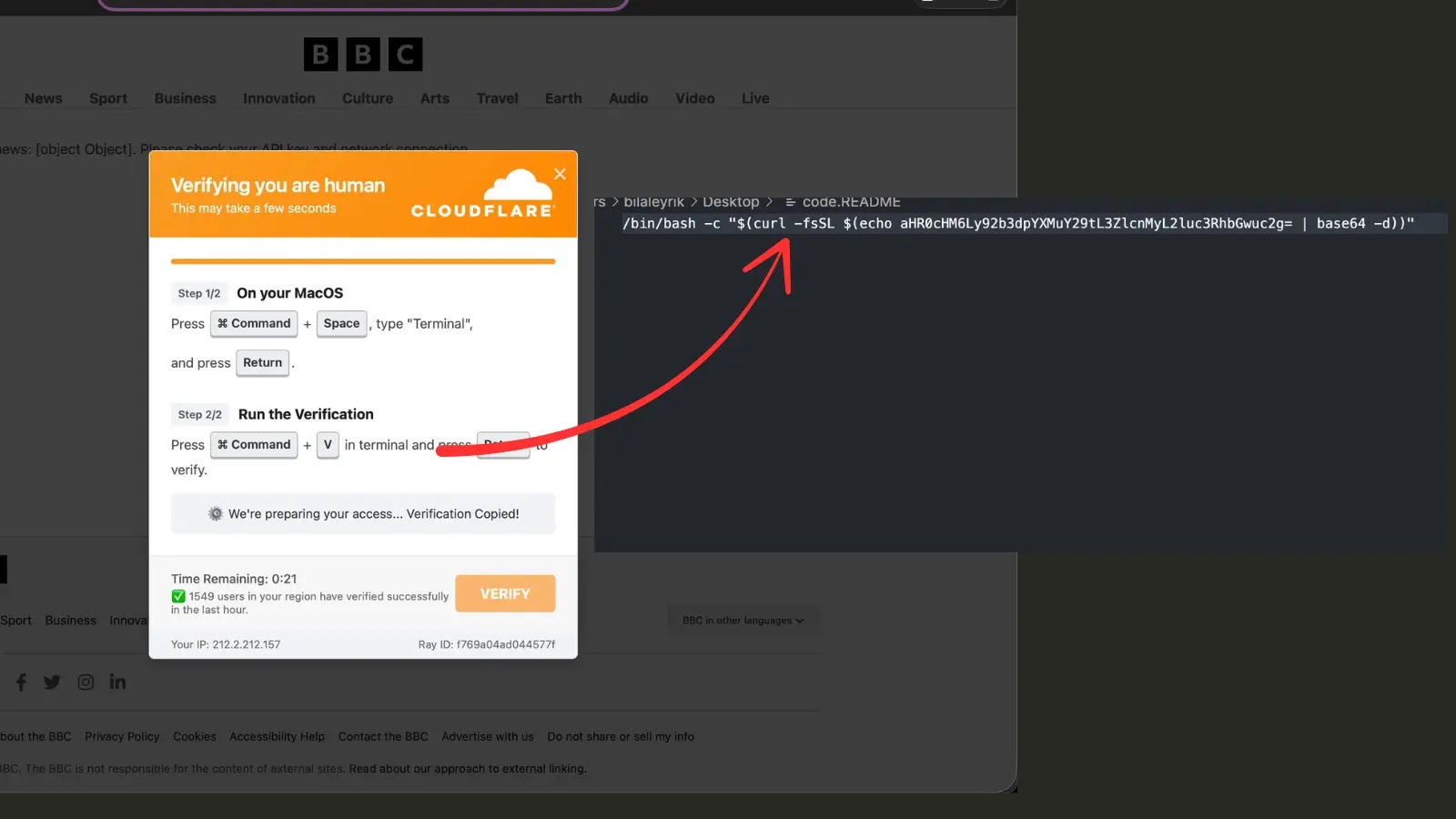
In keeping with a Reddit submit, the ClickFix assault masquerades as reputable BBC information content material whereas using faux Cloudflare verification screens to ship malware.
How the Assault Works
The assault begins when customers expertise what seems to be reputable internet advertising or search outcomes. Upon clicking, victims are redirected to a convincing duplicate of a BBC information web site populated with articles stolen from reputable sources.
Nonetheless, as an alternative of genuine information content material, the faux website serves as a supply mechanism for a extra alarming function.
After looking the fabricated information website, customers encounter what seems to be a regular Cloudflare safety verification web page. These pages are pixel-perfect replicas of real Cloudflare Turnstile challenges, full with authentic-looking logos and Ray ID footers that lend an air of legitimacy.
The faux verification web page shows the acquainted “Confirm you might be human” checkbox that customers have grown accustomed to seeing throughout the web.
Nonetheless, when customers try to finish the verification, they obtain directions to carry out a collection of seemingly routine steps:
Press Home windows + R to open the Run dialog.
Press Ctrl + V to stick a verification command.
Press Enter to execute the command.
What customers don’t notice is that clicking the verification button has already loaded a malicious PowerShell command into their system’s clipboard.
The command they paste and execute shouldn’t be a reputable verification instrument, however moderately malicious code designed to obtain and set up varied sorts of malware.
The ClickFix method has skilled explosive progress all through 2024 and 2025. In keeping with ESET’s Menace Report, ClickFix assaults surged by over 517% within the first half of 2025, making it the second commonest assault vector after phishing and accounting for practically 8% of all blocked assaults.
This social engineering method exploits customers’ pure tendency to rapidly remedy technical issues, notably when offered with authoritative-looking prompts from trusted providers like Cloudflare.
The assault’s effectiveness stems from its skill to bypass conventional safety measures by convincing customers to execute malicious code on their very own methods voluntarily.
Rising Menace Panorama
Cybersecurity researchers have recognized a number of variants of this assault concentrating on completely different platforms and providers. Past faux BBC information websites, attackers have been noticed impersonating varied trusted entities, together with Microsoft, Google Chrome, and even transportation and logistics software program particular to sure industries.
The malware delivered by these campaigns is various and harmful. Safety corporations report ClickFix assaults resulting in the deployment of knowledge stealers, ransomware, distant entry trojans, cryptominers, and even customized malware from nation-state-aligned risk actors. Well-liked malware households distributed by these campaigns embody Lumma Stealer, DarkGate, AsyncRAT, and NetSupport.
What makes these assaults notably regarding is their subtle evasion capabilities. The malicious PowerShell instructions usually retrieve Base64-encoded payloads from legitimate-seeming providers and embody anti-analysis options that terminate execution in the event that they detect digital machine environments.
This permits them to evade conventional safety scanning and obtain zero detection throughout many antivirus platforms.
The faux Cloudflare pages are professionally crafted to incorporate genuine advertising textual content copied immediately from Cloudflare’s official web site, making them extraordinarily troublesome to differentiate from reputable verification screens.
Some variants even show faux progress indicators and success messages to additional persuade customers that they’re finishing a reputable safety course of.
Latest developments past ClickFix strategies embody Safety researcher mr d0x recognized a brand new variant referred to as FileFix that leverages Home windows File Explorer as an alternative of the Run dialog, instructing customers to stick malicious instructions into the file explorer tackle bar.
This evolution demonstrates how risk actors proceed to adapt their methods to take care of effectiveness as consciousness grows.
Mitigations
Organizations and people can take a number of steps to guard in opposition to these assaults. Boston School IT and different safety consultants suggest by no means executing unsolicited instructions from web sites, no matter how reputable they seem. Key defensive measures embody:
Disabling the Home windows Run dialog by Group Coverage or registry modifications to forestall execution of malicious instructions.
Coaching customers to acknowledge faux verification screens and suspicious command prompts.
Implementing behavioral monitoring to detect uncommon PowerShell or command-line exercise.
Sustaining up to date safety software program with behavioral evaluation capabilities.
Safety professionals emphasize that reputable providers like Cloudflare by no means require customers to work together immediately with their working system or execute terminal instructions as a part of verification processes. Any web site requesting such actions needs to be instantly thought of suspicious and prevented.
The cybersecurity neighborhood has responded to the ClickFix risk with enhanced detection capabilities and consciousness campaigns. Microsoft has been monitoring particular campaigns underneath risk actor designations like Storm-1865, whereas safety corporations like ESET and Proofpoint have developed specialised detection guidelines for figuring out ClickFix assaults.
The fast evolution and rising sophistication of ClickFix assaults spotlight the continuing problem of defending in opposition to social engineering methods that exploit human psychology moderately than technical vulnerabilities.
As these assaults change into extra prevalent, continued vigilance and consumer training stay vital elements of cybersecurity protection methods.
This newest marketing campaign, combining faux BBC information websites with fraudulent Cloudflare verification, represents a regarding escalation within the complexity and deception employed by cybercriminals, underscoring the necessity for heightened consciousness and sturdy safety measures throughout all ranges of web utilization.
Discover this Story Attention-grabbing! Observe us on LinkedIn and X to Get Extra Instantaneous Updates.