A brand new proof-of-concept software named EDR-Freeze has been developed, able to putting Endpoint Detection and Response (EDR) and antivirus options right into a suspended “coma” state.
In accordance with Zero Salarium, the method leverages a built-in Home windows operate, providing a stealthier different to the more and more widespread Deliver Your Personal Weak Driver (BYOVD) assaults utilized by menace actors to disable safety software program.
Not like BYOVD strategies, which require introducing a weak driver onto a goal system, EDR-Freeze exploits reputable elements of the Home windows working system.
This strategy avoids the necessity to set up third-party drivers, lowering the danger of system instability and detection. Your entire course of is executed from user-mode code, making it a delicate and efficient strategy to quickly neutralize safety monitoring.
The MiniDumpWriteDump Exploit
The core of the EDR-Freeze method lies within the manipulation of the MiniDumpWriteDump operate. This operate, a part of the Home windows DbgHelp library, is designed to create a minidump, a snapshot of a course of’s reminiscence for debugging functions.
To make sure a constant and uncorrupted snapshot, the operate suspends all threads inside the goal course of whereas the dump is created.
Ordinarily, this suspension is temporary. Nevertheless, the developer of EDR-Freeze devised a way to delay this suspended state indefinitely.
EDR-Freeze Instrument
The first challenges had been twofold: extending the very quick execution time of the MiniDumpWriteDump operate and bypassing the Protected Course of Mild (PPL) safety function that shields EDR and antivirus processes from tampering.
To beat PPL safety, the method makes use of WerFaultSecure.exe, a element of the Home windows Error Reporting (WER) service. WerFaultSecure.exe can run with WinTCB degree safety, one of many highest privilege ranges, permitting it to work together with protected processes.
By crafting the proper parameters, WerFaultSecure.exe will be instructed to provoke the MiniDumpWriteDump operate on any goal course of, together with protected EDR and antivirus brokers.
The ultimate piece of the puzzle is a race-condition assault that turns a momentary suspension into a chronic freeze. The assault unfolds in a fast, exact sequence:
WerFaultSecure.exe is launched with parameters directing it to create a reminiscence dump of the goal EDR or antivirus course of.
The EDR-Freeze software constantly screens the goal course of.
The second the goal course of enters a suspended state (as MiniDumpWriteDump begins its work), the EDR-Freeze software instantly suspends the WerFaultSecure.exe course of itself.
As a result of WerFaultSecure.exe is now suspended, it may by no means full the reminiscence dump operation and, crucially, can by no means resume the threads of the goal EDR course of.
The result’s that the safety software program is left in a everlasting state of suspension, successfully blinded, till the WerFaultSecure.exe course of is terminated, Zero Salarium mentioned.
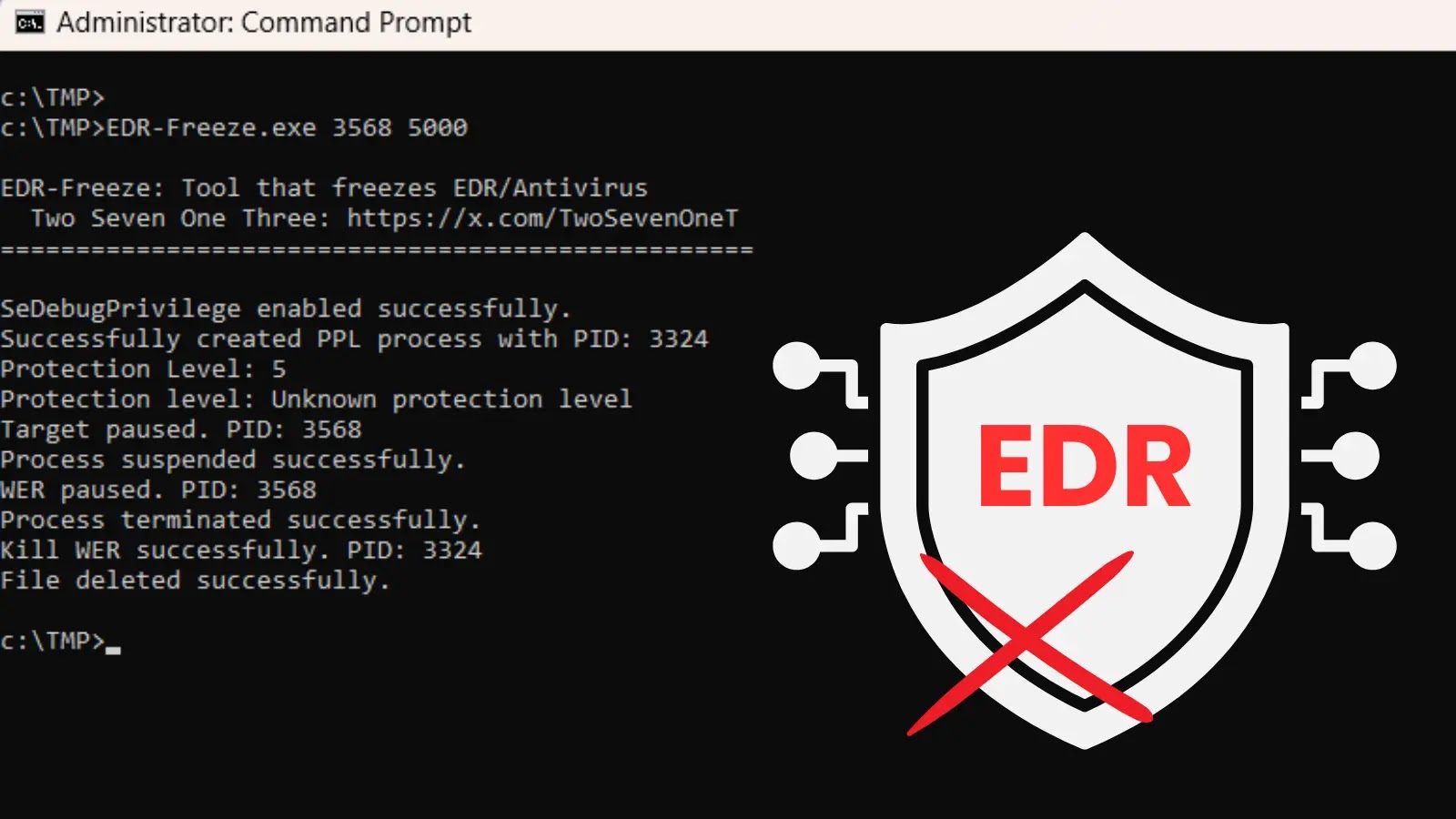
The developer has launched the EDR-Freeze software to exhibit this system. It takes two easy parameters: the Course of ID (PID) of the goal to be frozen and the period of the suspension in milliseconds.
This enables an attacker to disable safety instruments, carry out malicious actions, after which enable the safety software program to renew regular operations as if nothing had occurred.
A check on Home windows 11 24H2 efficiently suspended the MsMpEng.exe strategy of Home windows Defender.
EDR-Freeze Instrument Kills EDR and Antivirus
For defenders, detecting this system includes monitoring for uncommon executions of WerFaultSecure.exe.
If this system is noticed focusing on the PIDs of delicate processes like lsass.exe or EDR brokers, it ought to be handled as a high-priority safety alert requiring fast investigation.
Discover this Story Attention-grabbing! Observe us on Google Information, LinkedIn, and X to Get Extra Instantaneous Updates.