The cyberthreat panorama continues to evolve as malicious actors develop more and more refined assault strategies, with the EncryptHub menace group rising as a very regarding adversary.
This rising menace actor, also referred to as LARVA-208 and Water Gamayun, has been making headlines for its aggressive campaigns concentrating on Web3 builders and abusing respectable platforms to ship malicious payloads.
Current experiences point out that 618 organizations worldwide have fallen sufferer to EncryptHub’s community compromises as of February 2025.
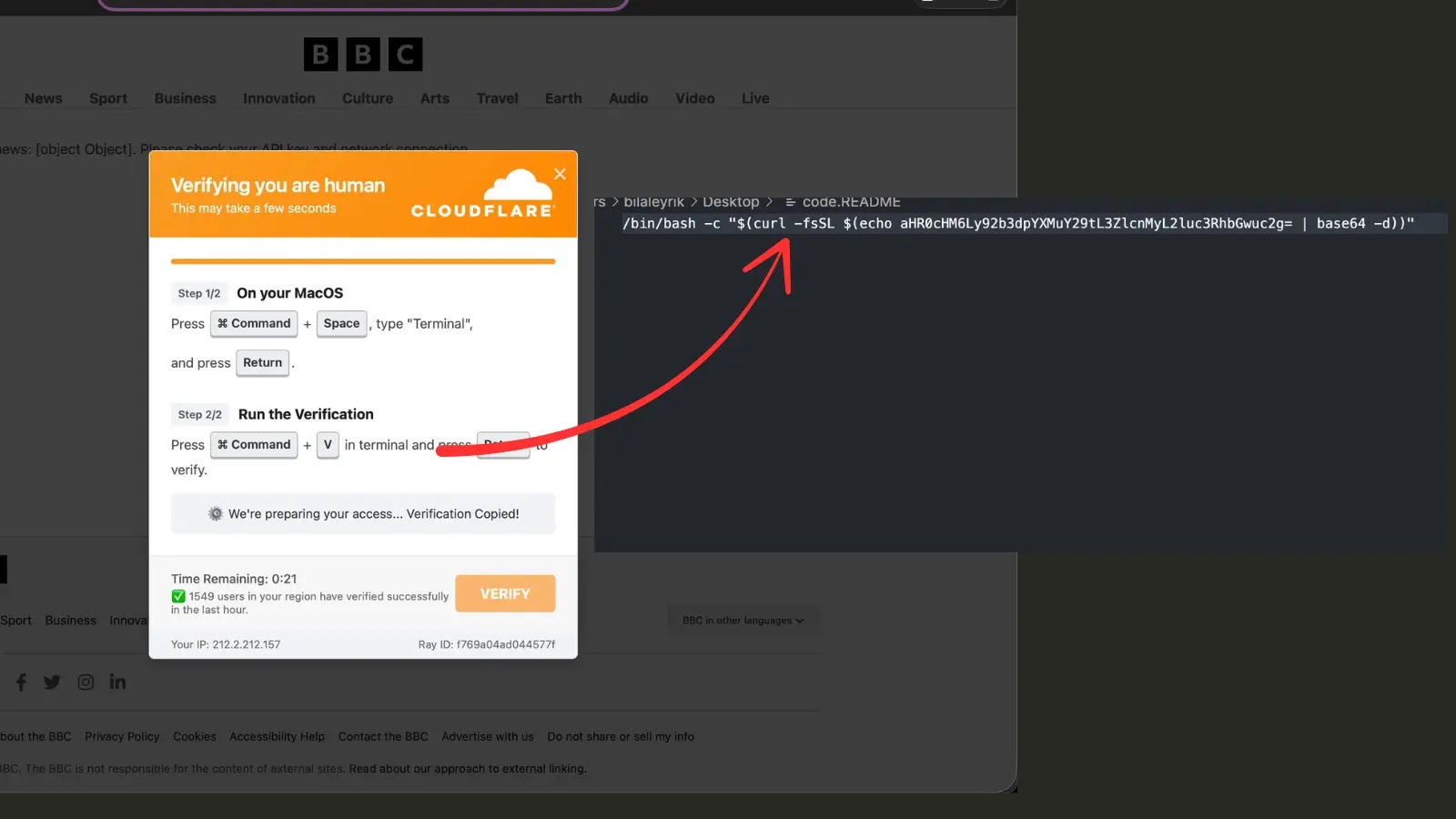
The group’s newest marketing campaign represents a harmful fusion of social engineering techniques and technical exploitation, particularly concentrating on the Microsoft Administration Console by the CVE-2025-26633 vulnerability, dubbed MSC EvilTwin.
This vulnerability permits attackers to execute malicious MSC information by inserting them in strategic listing areas, successfully hijacking respectable system processes.
The assault begins with menace actors impersonating IT assist employees, establishing Microsoft Groups connections with victims, and subsequently deploying malicious payloads to compromised techniques.
Trustwave analysts recognized this refined marketing campaign throughout their ongoing menace analysis actions, uncovering a multi-stage assault chain that mixes social engineering with platform abuse.
Assault chain (Supply – Trustwave)
The researchers noticed attackers executing PowerShell instructions to retrieve preliminary payloads, adopted by the deployment of specialised instruments designed to take care of persistent entry and exfiltrate delicate info.
What makes this marketing campaign significantly noteworthy is the group’s progressive abuse of the Courageous Assist platform, a respectable service related to the Courageous browser, to host and distribute malicious content material.
The assault methodology demonstrates EncryptHub’s dedication to mixing respectable companies with malicious intent, making detection considerably more difficult for conventional safety options.
By leveraging trusted platforms like Courageous Assist, the group can bypass many safety filters that may sometimes flag suspicious obtain sources.
This method highlights a rising development amongst cybercriminals who more and more exploit the belief related to respectable platforms to facilitate their malicious actions.
Evaluation of the MSC EvilTwin Exploitation
The core of EncryptHub’s assault depends on exploiting the CVE-2025-26633 vulnerability by a classy file placement approach.
When victims execute the preliminary PowerShell command, the malware downloads and executes runner.ps1, which serves as the first deployment mechanism for the MSC exploitation framework.
The runner.ps1 script implements a intelligent listing manipulation approach by creating two MSC information with similar names however inserting them in several areas.
The respectable file resides in the usual system listing, whereas the malicious model is strategically positioned within the MUIPath listing, particularly throughout the en-US folder.
This placement exploits the MSC EvilTwin vulnerability’s file loading habits, the place mmc.exe prioritizes information discovered within the MUIPath listing over these in commonplace areas.
Throughout execution, the script dynamically modifies the malicious MSC file by changing the “htmlLoaderUrl” placeholder with EncryptHub’s command-and-control URL.
This modification permits the MSC file to retrieve and execute subsequent payloads immediately from the attacker’s infrastructure.
The method successfully transforms a respectable system utility right into a conduit for malicious code execution, demonstrating the group’s refined understanding of Home windows system internals and their skill to weaponize commonplace administrative instruments for malicious functions.
Enhance your SOC and assist your staff defend what you are promoting with free top-notch menace intelligence: Request TI Lookup Premium Trial.