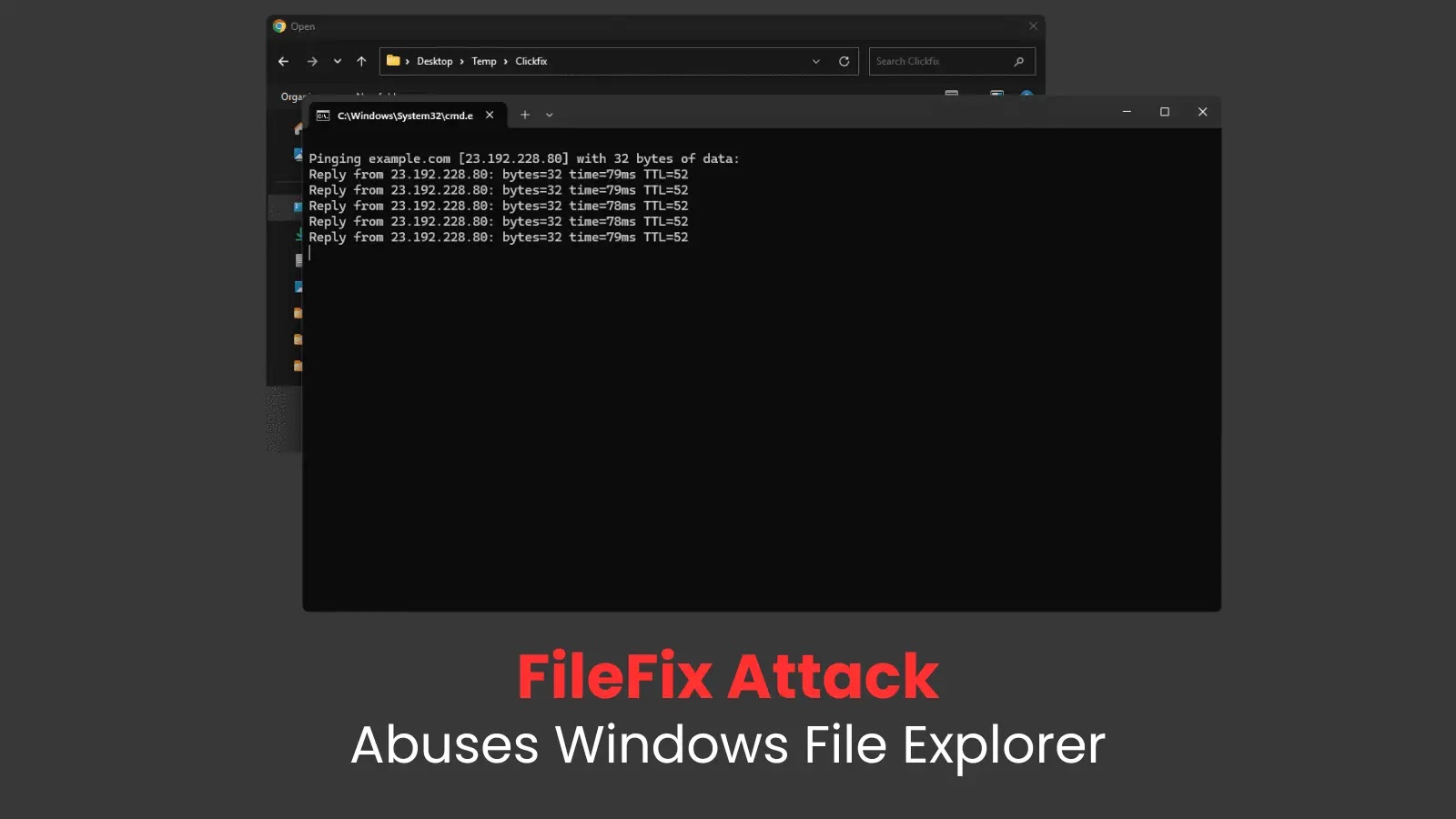
A novel social engineering approach referred to as “FileFix” that exploits Home windows File Explorer’s handle bar performance to execute malicious instructions, presenting a harmful various to the more and more in style ClickFix assault methodology.
The approach, found by safety researcher mr.d0x, leverages browser file add performance to open Home windows File Explorer and methods customers into executing PowerShell instructions by means of the handle bar slightly than the standard Home windows Run Dialog.
Command Execution Supply: mr.d0x
This methodology circumvents many safety consciousness coaching applications that concentrate on recognizing Run Dialog-based assaults.
ClickFix assaults have emerged as a big menace since early 2024, with cybersecurity corporations reporting a surge in these social engineering campaigns.
The approach usually entails faux error messages or CAPTCHA prompts that instruct customers to repeat and paste malicious instructions into the Home windows Run Dialog (Home windows Key + R).
In line with current menace intelligence stories, ClickFix campaigns have been noticed distributing numerous malware households, together with AsyncRAT, DarkGate, Lumma Stealer, and NetSupport RAT.
The assaults have been adopted by a number of menace actors, from particular person cybercriminals to nation-state teams similar to Russia-linked APT28 and Iran-linked MuddyWater.
How FileFix Exploits File Explorer
The FileFix assault methodology begins with a convincing phishing webpage that mimics authentic file-sharing companies. When customers click on an “Open File Explorer” button, JavaScript robotically copies a malicious PowerShell command to the clipboard whereas concurrently triggering the browser’s file add dialog.
Assault Stream – Picture Credit (Cybersecuritynews.com)
The file add performance causes Home windows File Explorer to open, at which level the assault depends on social engineering to information customers by means of the execution course of.
The malicious webpage gives directions for customers to stick what they imagine is a file path into the File Explorer handle bar utilizing Ctrl+L, however the clipboard really incorporates a hidden PowerShell command, mr.d0x stated.
A key facet of the assault entails command obfuscation, the place the malicious PowerShell script is concatenated with a faux file path after a remark image, making it seem authentic to unsuspecting customers. For instance: Powershell.exe -c ping instance.com # C:firminternal-securefiledriveHRPolicy.docx
The assault exploits Home windows File Explorer’s skill to execute instructions instantly from the handle bar, a characteristic that many customers are unaware of.
Safety researchers have documented how File Explorer can run numerous system instructions, together with PowerShell, Command Immediate, and different utilities, when entered into the handle bar.
The researchers have additionally recognized a secondary variation that entails downloading executable information and leveraging the truth that applications executed by means of File Explorer’s handle bar have their Mark of the Internet (MOTW) attribute eliminated. This might probably bypass sure safety controls that depend on MOTW for menace detection.
The FileFix approach represents an evolution in social engineering assaults, shifting past the standard ClickFix methodology whereas sustaining related effectiveness. The assault is especially regarding as a result of it operates solely throughout the browser atmosphere and depends on authentic Home windows performance.
Cybersecurity consultants suggest monitoring for suspicious little one processes spawned by browsers, significantly cmd.exe and PowerShell.exe, in addition to different system utilities. Organizations must also replace their safety consciousness coaching to incorporate File Explorer-based assault vectors alongside conventional Run Dialog methods.
As phishing assaults proceed to evolve with a reported 202% improve in total phishing messages in 2024, the emergence of FileFix demonstrates how menace actors repeatedly adapt their methods to bypass safety measures and consumer consciousness applications.
The simplicity and effectiveness of those browser-based assaults underscore the continuing problem of defending in opposition to human-targeted social engineering campaigns.
Stay Credential Theft Assault Unmask & On the spot Protection – Free Webinar