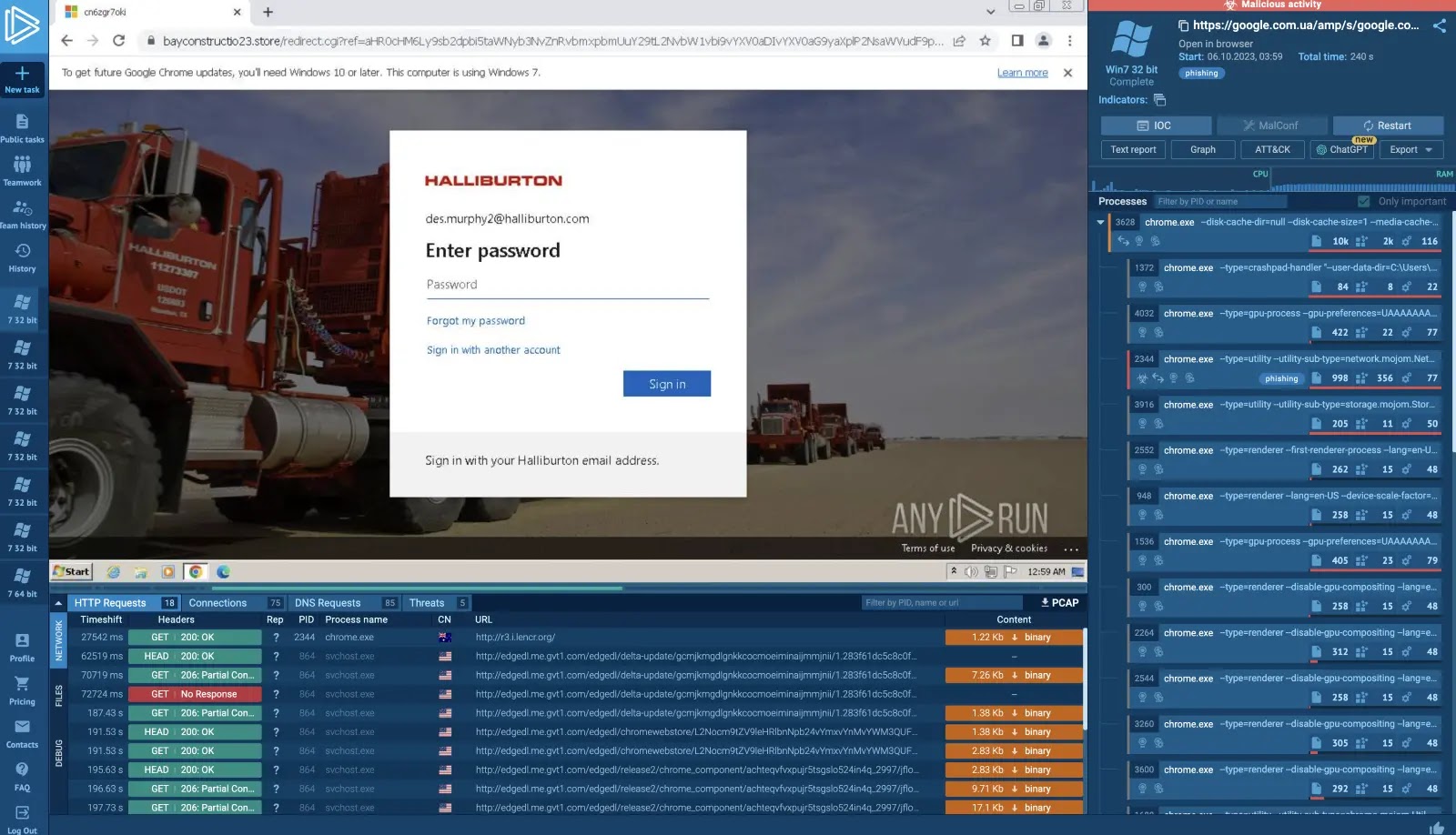
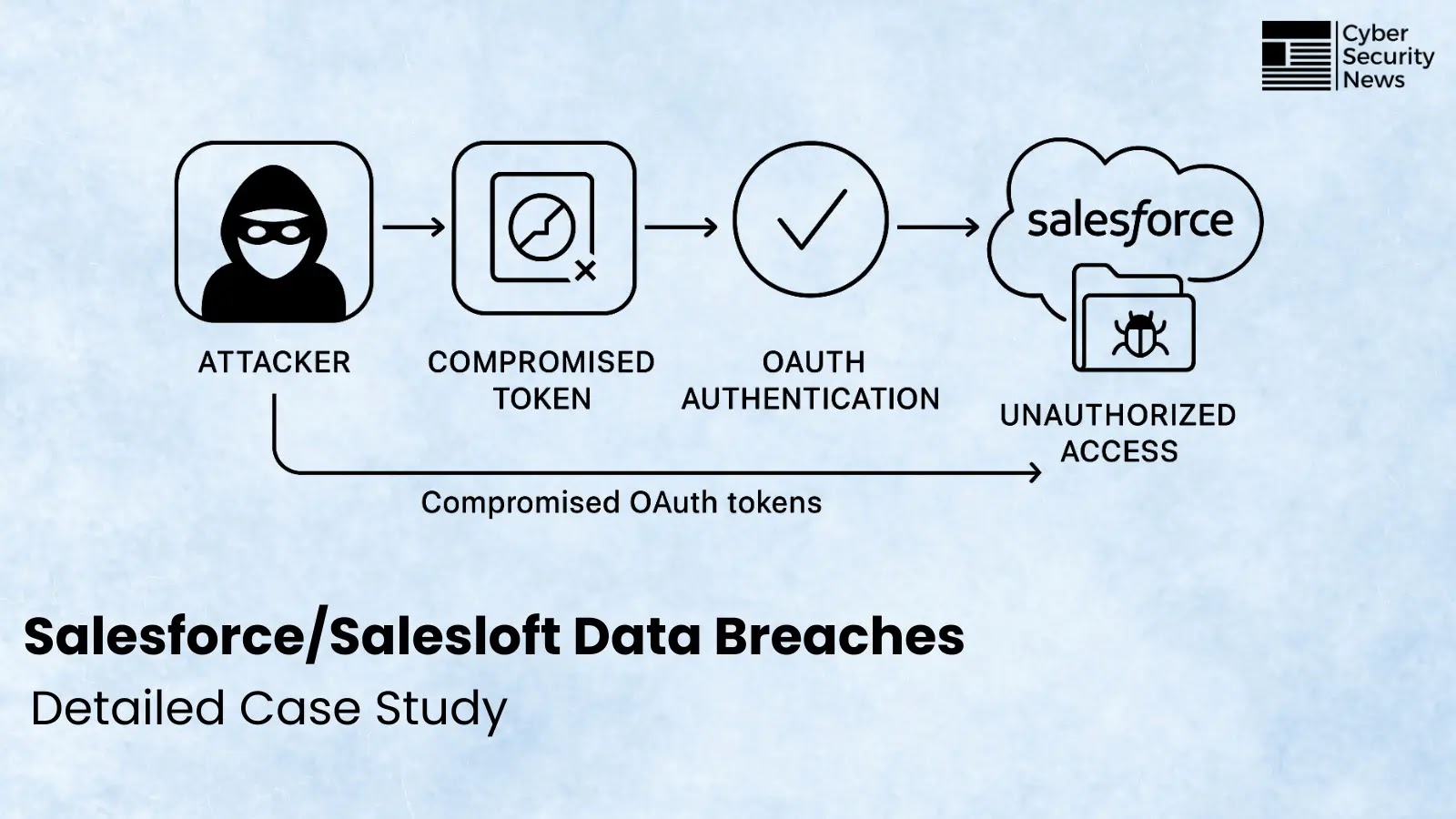
A classy Android distant entry trojan (RAT) has emerged on GitHub, presenting important safety issues for cellular machine customers worldwide.
The malware, publicly out there beneath the repository “Android-RAT” by consumer Huckel789, claims to supply absolutely undetectable (FUD) capabilities that may bypass trendy safety measures and antivirus detection programs.
This malicious software program represents a regarding evolution in cellular malware distribution, leveraging professional platforms to host and distribute harmful payloads.
The RAT operates via a web-based interface requiring no PC set up, making it accessible to risk actors with various technical experience.
Its distribution technique exploits GitHub’s trusted platform standing, doubtlessly bypassing safety filters that usually block malicious downloads from suspicious domains.
The malware’s complete characteristic set consists of keylogging capabilities, credential hijacking, ransomware performance, and complex social engineering instruments designed to deceive customers into granting obligatory permissions.
Safety researcher Huckel789 recognized this explicit pressure as using superior stealth methods particularly engineered to evade detection by fashionable antivirus options and VirusTotal scans.
The malware incorporates anti-emulator and digital machine detection mechanisms, making certain it operates completely on real Android gadgets whereas remaining dormant in safety evaluation environments.
This selective activation strategy considerably complicates conventional malware evaluation workflows utilized by safety professionals.
The Android RAT demonstrates outstanding persistence capabilities, surviving extremely battery optimization modes and numerous energy administration restrictions generally present in Chinese language ROM implementations like MIUI.
Its resource-efficient design permits steady background operation whereas consuming minimal system assets, making detection via efficiency monitoring extraordinarily tough.
Superior Evasion and Communication Structure
The malware’s communication infrastructure represents a classy strategy to command and management operations.
Not like typical RATs that make use of easy base64 encoding for server communications, this variant implements AES-128-CBC encryption with PKCS padding to safe all information transmissions between contaminated gadgets and command servers.
The encryption implementation ensures that community visitors evaluation can’t simply reveal malicious communications, whereas superior obfuscation methods defend the embedded server IP addresses from discovery via static code evaluation.
The RAT’s “Freeze Mode” performance demonstrates explicit innovation in stealth operations, limiting information transmission to 1-3MB over 24-hour intervals whereas sustaining responsiveness to operator instructions.
This strategy minimizes community signatures that might set off safety monitoring programs whereas making certain dependable distant entry capabilities.
The malware can inject its payload into professional functions via a classy dropper module, making preliminary an infection vectors extraordinarily tough to determine via typical safety scanning mechanisms.
Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates, Set CSN as a Most well-liked Supply in Google.