Cybersecurity researchers have recognized a complicated new phishing marketing campaign that exploits GitHub’s OAuth2 machine authorization move to compromise developer accounts and steal authentication tokens.
This rising risk represents a big evolution in social engineering techniques, leveraging legit GitHub performance to bypass conventional safety measures and achieve unauthorized entry to supply code repositories, CI/CD pipelines, and delicate mental property.
The assault approach mirrors established Azure Lively Listing machine code phishing strategies which have plagued enterprise environments for years, however now targets the developer ecosystem via GitHub’s platform.
Not like typical phishing approaches that depend on fraudulent web sites or malicious hyperlinks, these assaults abuse GitHub’s native machine code authentication course of, making them significantly troublesome to detect and block utilizing normal safety controls.
Following latest high-profile provide chain assaults together with the tj-actions incident, Praetorian analysts famous that GitHub entry has develop into more and more worthwhile to risk actors searching for to compromise software program improvement pipelines.
The researchers recognized that these machine code phishing assaults have achieved success charges exceeding 90% when performed through cellphone calls to builders, demonstrating the approach’s effectiveness in opposition to even security-conscious targets.
GitHub Machine Code Authentication move (Supply – Praetorian)
The impression of profitable assaults extends far past particular person account compromises.
As soon as attackers receive GitHub OAuth tokens with applicable scopes, they’ll exfiltrate proprietary supply code, entry GitHub Actions secrets and techniques for lateral motion, execute malicious code on self-hosted runners, and doubtlessly backdoor essential repositories to launch provide chain assaults affecting hundreds of downstream customers.
The preliminary machine code web page (Supply – Praetorian)
The centralization of improvement infrastructure round GitHub has made these assaults significantly enticing to risk actors searching for most impression from minimal effort.
Assault Mechanism
The GitHub machine code phishing course of follows a methodical five-step method that exploits the inherent belief mannequin of OAuth2 machine authorization.
The assault begins when risk actors generate machine codes via GitHub’s OAuth API, sometimes requesting broad permissions together with person, repository, and workflow scopes.
The next code snippet demonstrates the preliminary request:-
curl -X POST
-H “Settle for: software/json”
-d “client_id=01ab8ac9400c4e429b23&scope=person+repo+workflow”
Authentication dealer (Supply – Praetorian)
Attackers usually make the most of legit consumer IDs comparable to Visible Studio Code’s identifier (01ab8ac9400c4e429b23) to cut back person suspicion in the course of the authorization course of.
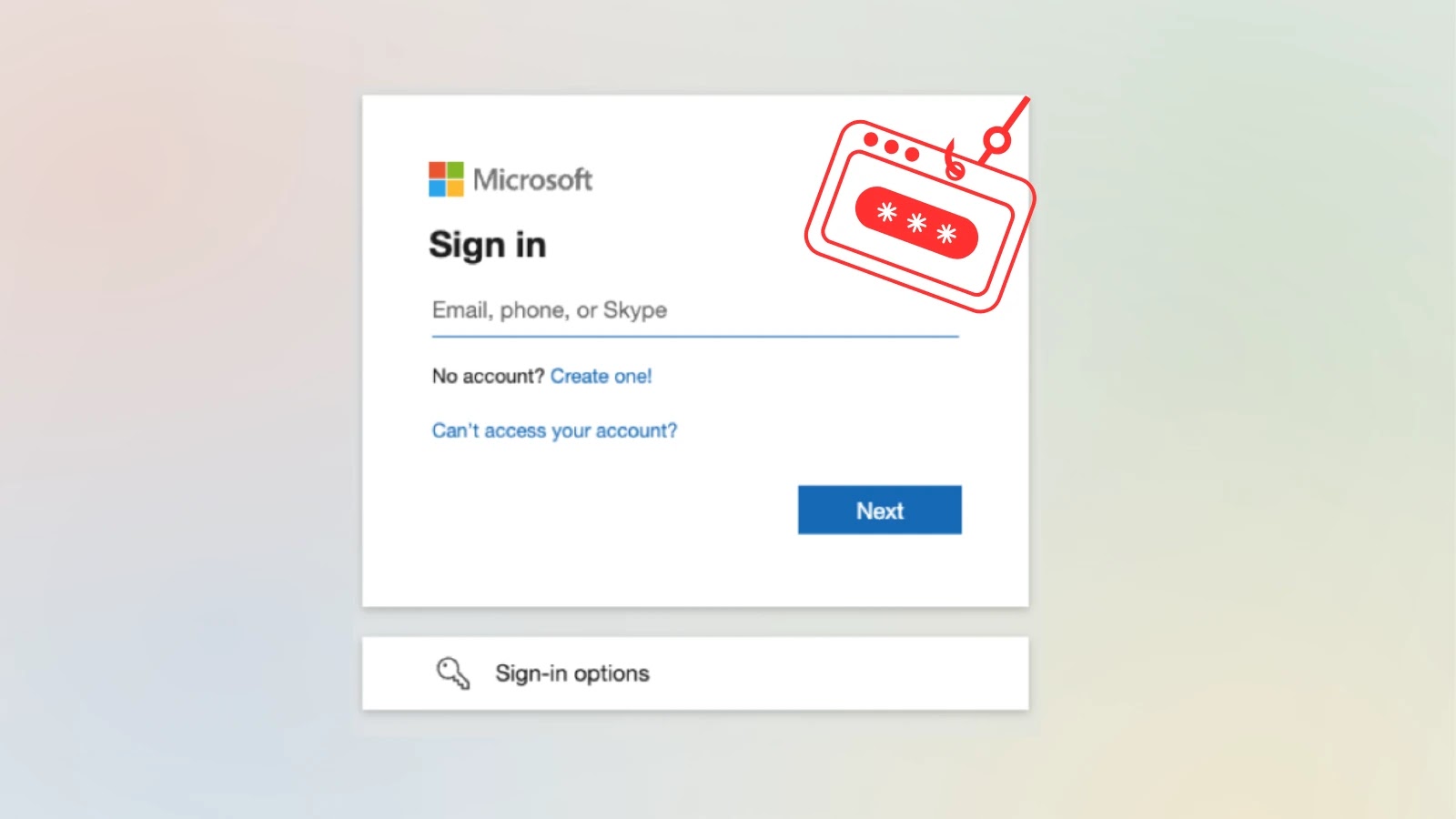
The server response features a machine code for token retrieval, a six-digit person code, the verification URL ( and a 15-minute expiration window.
The social engineering section includes convincing builders to navigate to the verification URL and enter the offered code.
Praetorian researchers have documented numerous profitable pretexts, together with impersonating helpdesk personnel claiming machine registration updates are required or IT employees conducting safety verification procedures.
As soon as victims full the authentication move and authorize the applying, attackers retrieve the OAuth token utilizing the unique machine code.
This token offers persistent entry to the sufferer’s GitHub sources, enabling complete reconnaissance and knowledge exfiltration actions.
The approach’s effectiveness stems from its use of legit GitHub performance, making it practically unattainable to tell apart malicious machine code requests from real authentication makes an attempt with out extra context or behavioral evaluation.
Automate risk response with ANY.RUN’s TI Feeds—Enrich alerts and block malicious IPs throughout all endpoints -> Request full acces