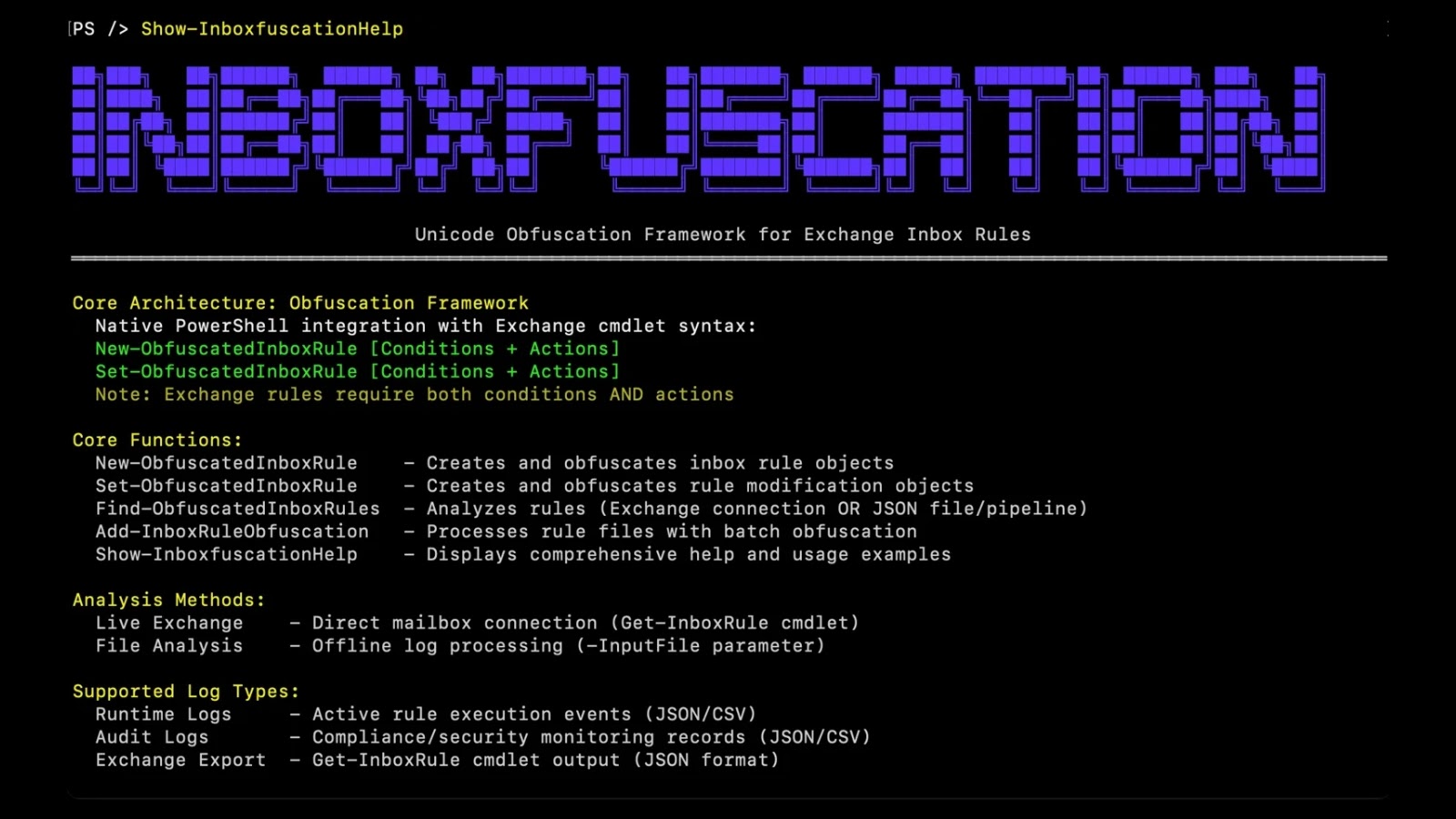
Attackers more and more exploit Microsoft Alternate inbox guidelines to take care of persistence and exfiltrate knowledge inside enterprise environments.
A newly launched instrument, Inboxfuscation, leverages Unicode-based obfuscation to craft malicious inbox guidelines that slip previous typical safety controls.
Developed by Permiso, the Inboxfuscation framework demonstrates how attackers can weaponize Alternate’s rule engine, creating stealthy persistence mechanisms that evade each human assessment and code-based detection.
Unicode-Primarily based Evasion
Conventional inbox rule assaults relied on clear-text key phrases and easy actions reminiscent of forwarding or deleting messages.
Such guidelines are simply flagged by keyword-based detection and regex matching. Inboxfuscation transforms this paradigm by substituting ASCII characters with visually equivalent Unicode variants, injecting zero-width characters, manipulating bidirectional textual content, and mixing a number of obfuscation methods.
For instance, the phrase “secret” will be obfuscated as:
Permiso said that by exploiting character classes reminiscent of MATHEMATICAL ALPHANUMERIC SYMBOLS (U+1D4B6), ZERO-WIDTH SPACES (U+200B), and RIGHT-TO-LEFT OVERRIDE (U+202E), attackers can create guidelines that seem benign in Alternate’s Get-InboxRule output but functionally match delicate key phrases.
Alternate’s Get-InboxRule
Inboxfuscation additionally introduces useful obfuscation tips, reminiscent of guidelines that ahead emails into the Calendar folder or insert null characters (u0000) to render guidelines invisible and unretrievable.
Detection and Mitigation Methods
Typical detection instruments fail towards Unicode obfuscation as a result of they assume ASCII-based sample matching and visible similarity.
Inboxfuscation’s detection framework extends Permiso’s Arbiter Detection module to research occasions throughout mailboxes and reconstruct multi-step rule creation behaviors. Key elements embody:
Character Class Evaluation
Helps JSON, CSV, Alternate export, and Microsoft 365 Graph API logs.
Rule Audit and Historic Evaluation
Structured output consists of rule_name, mailbox, risk_score, and unicode_char_count.
To mitigate this risk, safety groups ought to implement Unicode-aware detection guidelines, carry out complete inbox rule audits, and simulate obfuscated guidelines in testing environments.
Organizations should replace Alternate monitoring pipelines to flag suspicious Unicode classes and leverage sandboxed environments to examine rule normalization behaviors.
Though these Unicode obfuscation methods haven’t but been noticed in reside assaults, their technical feasibility exposes a important blind spot in e mail safety postures.
By proactively adopting Inboxfuscation’s detection framework and understanding the mechanics of Unicode-based evasion, defenders can keep forward of rising APT techniques and shield enterprise communications from stealthy persistence methods.
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.