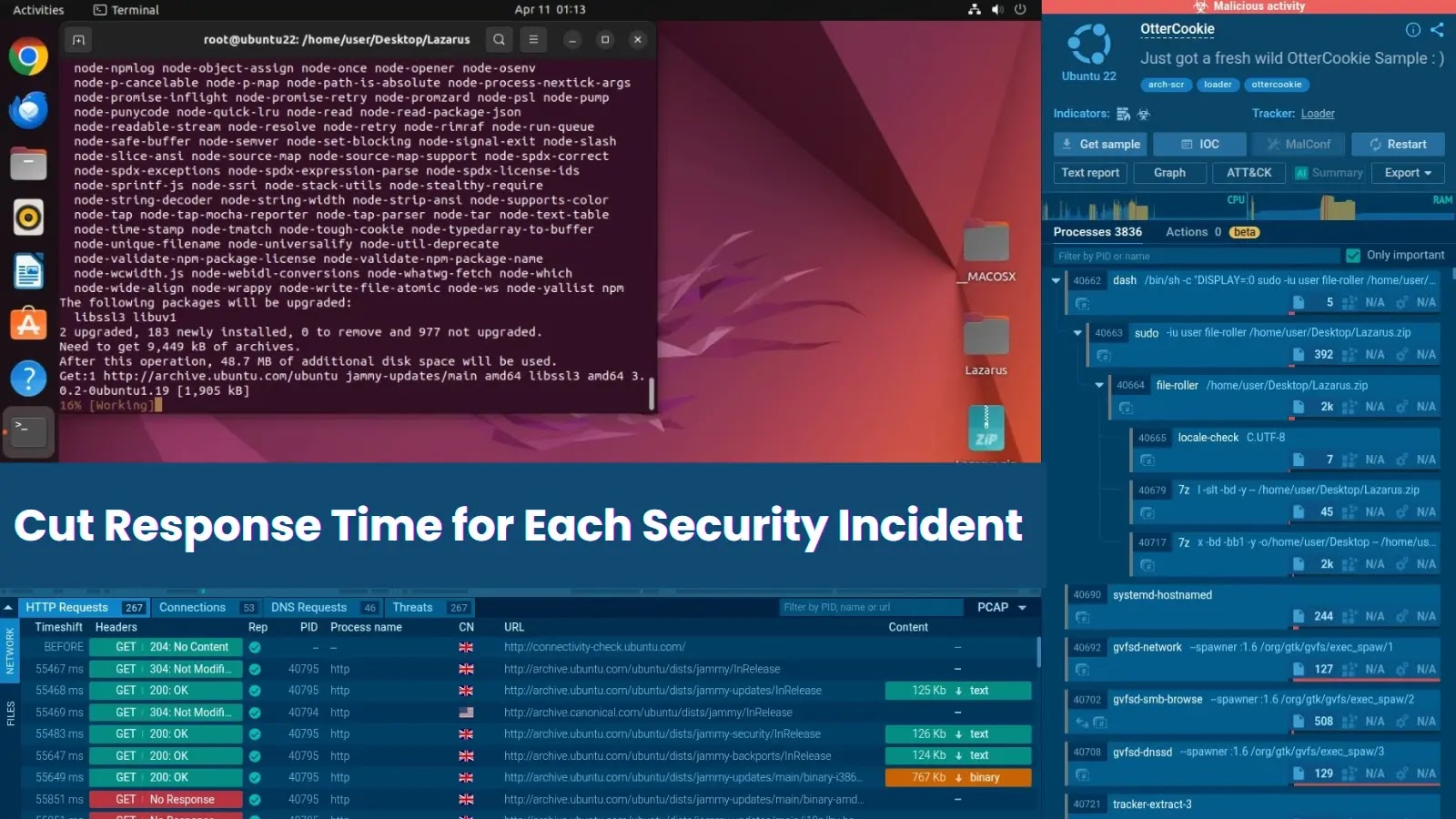
A important flaw in Home windows Kerberos authentication that considerably expands the assault floor for credential relay assaults in Energetic Listing environments.
By abusing how Home windows shoppers deal with DNS CNAME responses throughout Kerberos service ticket requests, attackers can coerce methods into requesting tickets for attacker-controlled providers, bypassing conventional protections.
Abuse circulation chart (Supply: Cymulate)
The Assault Vector
The vulnerability facilities on a elementary conduct: when a Home windows shopper receives a DNS CNAME file, it follows the alias. It constructs the Ticket Granting Service (TGS) request utilizing the CNAME hostname because the Service Principal Title (SPN).
An attacker positioned on-path to intercept DNS site visitors can exploit this to pressure victims into requesting service tickets for attacker-chosen targets.
The approach requires an attacker to determine DNS man-in-the-middle capabilities by way of ARP poisoning, DHCPv6 poisoning (MITM6), or related strategies.
The sufferer is redirected to the attacker’s server, which responds with 401 to pressure Kerberos authentication. (Supply: Cymulate)
When a sufferer makes an attempt to entry a reputable area asset, the malicious DNS server responds with a CNAME file pointing to an attacker-controlled hostname, together with an A file resolving to the attacker’s IP handle.
This causes the sufferer to authenticate in opposition to the attacker’s infrastructure utilizing a ticket supposed for the attacker’s goal service.
Assault Capabilities and Affect:
Affect AreaDescriptionRCERemote code execution by way of ADCS Net Enrollment (ESC8)Relay AttacksCross-protocol relays (HTTP→SMB, HTTP→LDAP)Lateral MovementUnauthorized entry and community spreadImpersonationUser impersonation with out passwords
Testing confirmed exploitation works on default configurations throughout Home windows 10, Home windows 11, Home windows Server 2022, and Home windows Server 2025.
The assault succeeds in opposition to unprotected providers, together with SMB, HTTP, and LDAP, when signing or Channel Binding Tokens (CBT) aren’t enforced. The vulnerability was responsibly disclosed to Microsoft in October 2025.
DNS poisoning redirects the sufferer to a malicious goal, forcing a Kerberos TGS request. (Supply: Cymulate)
In response, Microsoft applied CBT help for HTTP.sys. It launched patches throughout supported Home windows Server variations in January 2026 safety updates, tracked as CVE-2026-20929.
Nonetheless, this mitigation solely addresses HTTP relay eventualities. The underlying DNS CNAME coercion primitive stays unchanged, leaving different protocols susceptible.
Proof of Idea
Researchers launched a modified model of the MITM6 instrument on GitHub with CNAME poisoning capabilities. The instrument helps focused CNAME poisoning in opposition to particular domains or all DNS queries.
Consists of DNS-only mode for ARP poisoning integration, and allows passthrough for important infrastructure connectivity. Exploitation requires Python 3.x and a Linux working system.
A file for adcs-server.mycorp.native pointing to the attacker’s IP (Supply: Cymulate)
Cymulate Analysis Labs advises organizations to implement layered defenses:
Safety LayerRecommended ControlPurposeSMB SecurityEnforce SMB signing on all servers past area controllersPrevents SMB relay and man-in-the-middle attacksDirectory ServicesRequire LDAP signing and implement LDAPS Channel Binding Tokens (CBT) the place supportedProtects in opposition to LDAP relay and credential interceptionWeb ServicesMandate HTTPS with CBT for all inner HTTP servicesMitigates NTLM relay assaults over HTTPDNS InfrastructureHarden DNS servers and think about DNS over HTTPS (DoH)Reduces DNS spoofing and site visitors manipulation risksKerberos MonitoringMonitor anomalous TGS requests focusing on uncommon SPNsDetects potential Kerberos abuse or lateral movementThreat DetectionAlert on cross-protocol authentication patternsIdentifies NTLM/Kerberos relay and protocol abuse makes an attempt
The analysis underscores a important safety actuality: Kerberos itself doesn’t inherently stop relay assaults. Enforcement of safety lies on the service degree.
After DNS poisoning, the sufferer connects to the attacker’s rogue HTTP or SMB server.(Supply: Cymulate)
Disabling NTLM alone is inadequate; organizations should explicitly implement anti-relay protections throughout each Kerberos-enabled service to get rid of relay danger successfully.
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.