When you suppose phishing is simply clicking a nasty hyperlink and touchdown on a faux login web page, Tycoon2FA will show you fallacious. This new wave of phishing-as-a-service isn’t enjoying the outdated sport anymore; it’s operating a 7-stage impediment course constructed to put on down each people and machines.
It’s already slipping previous trusted safety instruments. If SOC groups can’t expose it in time, the harm might be completed earlier than anybody even is aware of it’s there.
Let’s have a look at the way it works and what it takes to cease it.
Targeted on Excessive-Worth Targets
Tycoon2FA isn’t going after random inboxes, it’s intentionally concentrating on accounts that may unlock important programs and delicate information.
Authorities and navy companies.
Monetary establishments, from world banks to regional insurers.
Current campaigns have struck the US, UK, Canada, and Europe. Information from ANY.RUN exhibits that 26% of Tycoon2FA circumstances concerned banking-sector analysts, which is a transparent proof this package goes after sectors the place a single stolen login might trigger extreme monetary harm or nationwide safety dangers.
How Tycoon2FA Beats Defenses in 7 Steps
When detonated in a sandbox, Tycoon2FA reveals a fastidiously engineered 7-step path; every stage designed to dam automated instruments, exhaust analysts, and conceal the ultimate phishing panel till the very finish.
Verify Actual Case: Multi-Stage Tycoon2FA Assault
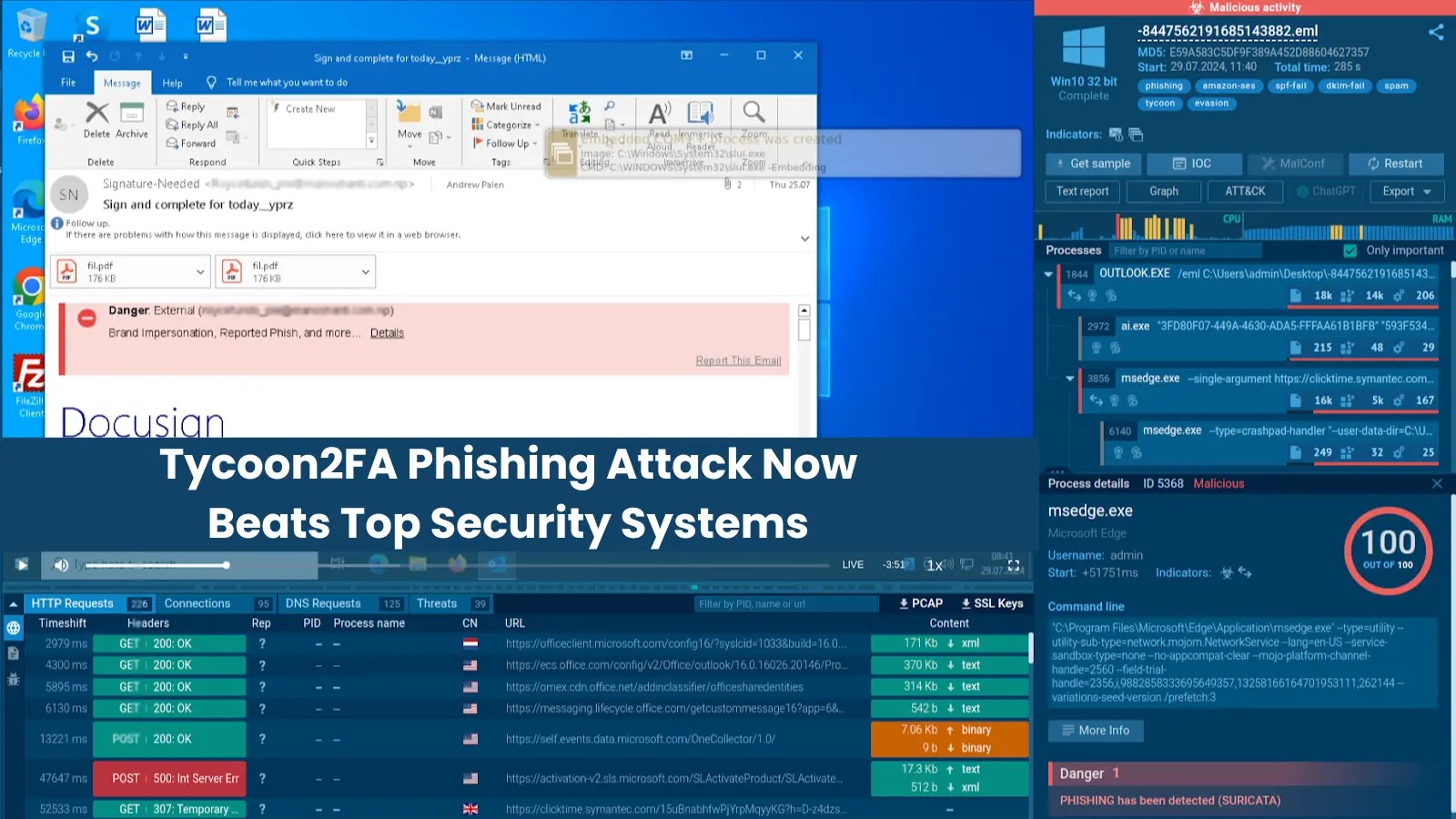
Evaluation of multi-stage Tycoon2FA assault inside ANY.RUN sandbox
In a current ANY.RUN evaluation session, Tycoon2FA’s total phishing chain was uncovered in simply minutes.
By operating the pattern with Automated Interactivity enabled, the sandbox didn’t cease at static evaluation; it simulated actual consumer habits, clicking hyperlinks, finishing CAPTCHAs, urgent buttons, and navigating multi-step redirects.
That is the place the detonation actions panel on the best aspect of the sandbox proves its price. It exhibits the important thing steps taken throughout execution and gives helpful hints to assist analysts hold the session shifting.
For junior analysts particularly, it’s a simple strategy to comply with the circulation and keep away from getting caught at difficult phases.
Detonation actions part with hints used to maintain the session shifting
Uncover the total scope of any assault, from hidden redirects to ultimate payload, in minutes, whereas gathering each IOC and behavioral indicator alongside the way-> Strive ANY.RUN with 14-day trial
1. Phishing e mail hyperlink
The chain begins with a voicemail-themed phishing e mail, urging the sufferer to click on a “Hear Right here” hyperlink. Automated interactivity clicks it instantly, beginning the evaluation with out handbook enter.
2. PDF obtain immediate
The hyperlink opens a “Obtain PDF” immediate disguised as a brand new voice message. The sandbox downloads the file immediately, preserving metadata for additional inspection.
3. Hyperlink contained in the PDF
Opening the PDF reveals one other embedded hyperlink. ANY.RUN detects and follows it routinely, guaranteeing no redirection step is missed.
Embedded hyperlink analyzed inside ANY.RUN sandbox
4. Cloudflare Turnstile CAPTCHA
A CAPTCHA problem seems to dam automated scanners. The sandbox completes it with out human assist, shifting the evaluation ahead.
5. “Press & Maintain” human verification
A second anti-bot verify requires a press-and-hold motion. Automated interactivity simulates this gesture, unlocking the following stage.
6. E-mail validation web page
The sufferer is prompted to “confirm” their e mail deal with earlier than persevering with; a step typically used to verify the goal is human and matches the attacker’s supposed profile.
E-mail verification web page uncovered inside interactive sandbox
7. Tycoon2FA phishing panel
The ultimate stage is a faux Microsoft login web page designed to steal credentials. ANY.RUN totally renders the web page, information site visitors, and logs indicators for additional investigation.
Why Sandbox Evaluation Ought to Be in Each SOC Workflow
Assaults like Tycoon2FA show that static instruments alone can’t sustain. Multi-stage phishing kits intentionally stall automated scanners with human-verification steps, disguise their ultimate payloads, and use domains that may stay undetected on VirusTotal for days.
By integrating an interactive sandbox into the SOC workflow, groups can:
Minimize investigation time: Automated interactivity handles repetitive consumer actions (CAPTCHAs, button clicks, redirects) so analysts can see your entire assault path in minutes as an alternative of hours.
Expose hidden payloads: Even multi-step phishing chains like Tycoon2FA are totally executed, revealing the ultimate phishing panel, community requests, and indicators.
Enhance detection accuracy: Behavioral evaluation uncovers malicious logic that signatures alone can’t catch.
Help junior analysts: The detonation actions panel gives clear, guided hints so much less skilled group members can comply with advanced chains with out stalling.
Enrich risk intelligence: Each session generates IOCs, behavioral patterns, and community indicators prepared to be used in detection guidelines and risk hunts.
With this strategy, SOC groups see the whole lot the attacker sees, and so they get it quick sufficient to behave earlier than the phishing marketing campaign strikes on to its subsequent goal.
Begin your 14-day trial of ANY.RUN and run your personal evaluation of suspicious recordsdata or hyperlinks. Watch each stage unfold, seize the proof you want, and construct detections that cease it chilly.