Current cybersecurity intelligence has uncovered a complicated infiltration marketing campaign orchestrated by North Korean state-sponsored risk actors, particularly the Jasper Sleet group, who’ve systematically penetrated Western organizations by fraudulent employment schemes.
This operation, concentrating on primarily Web3, blockchain, and cryptocurrency corporations, represents a big evolution in North Korean cyber warfare techniques, eliminating the necessity for conventional exploitation strategies by securing professional company entry by misleading hiring practices.
Two crucial information leaks, surfacing in mid-August 2025, have offered unprecedented perception into the operational construction and methodologies employed by these DPRK IT staff.
The primary leak uncovered 1,389 electronic mail addresses allegedly utilized by North Korean operatives to safe abroad employment, whereas a second leak revealed 28 extra addresses alongside operational paperwork, expense spreadsheets, and inside communications.
These breaches have illuminated the industrial-scale nature of the operation, revealing systematic id fabrication, technological infrastructure, and complex social engineering techniques designed to bypass typical safety screening processes.
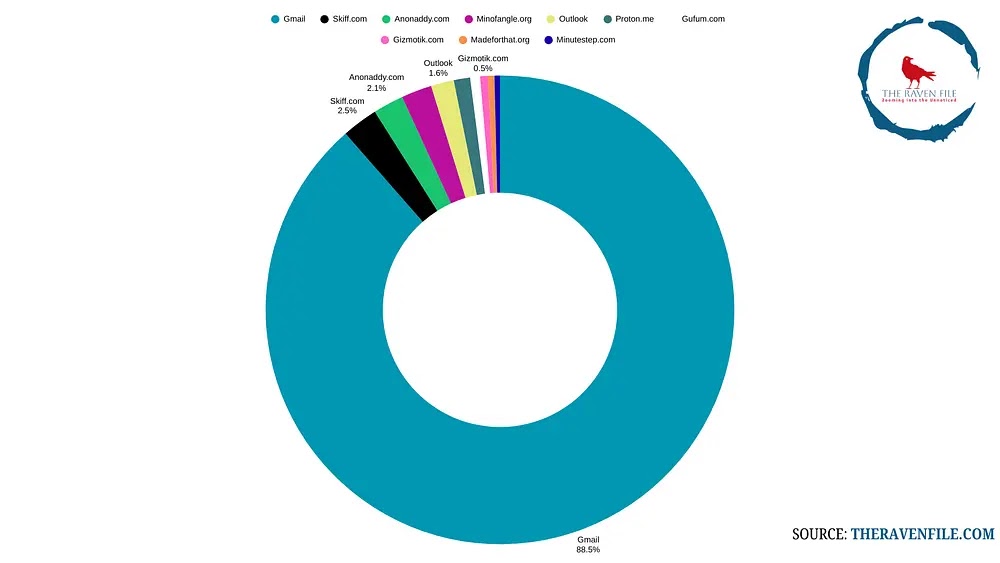
Completely different electronic mail domains detected (Supply – The Raven File)
THE RAVEN FILE analysts recognized crucial patterns inside the uncovered electronic mail addresses that function potential crimson flags for organizations conducting recruitment processes.
The analysis reveals that these risk actors display outstanding consistency of their operational safety practices, using particular naming conventions, non permanent electronic mail companies, and strategic age manipulation to create convincing skilled personas.
Affected TEMP and Privateness electronic mail platforms (Supply – The Raven File)
Evaluation of the compromised credentials signifies in depth use of privacy-focused electronic mail suppliers, with 29 out of 63 recognized electronic mail domains being non permanent electronic mail companies, whereas professional suppliers like Gmail and Skiff have been extensively compromised for operational functions.
E mail Sample Evaluation and Operational Infrastructure
The forensic examination of the leaked electronic mail addresses reveals systematic patterns that mirror each operational self-discipline and cultural influences within the risk actors’ id development methodology.
THE RAVEN FILE researchers famous that roughly 11 electronic mail addresses contained delivery years starting from 1990 to 1995, suggesting deliberate age concentrating on to current candidates inside optimum hiring demographics for know-how positions.
The naming conventions display strategic psychological manipulation, incorporating animal references (Dragon, Tiger, Lion, Bear), shade associations (Blue, Gold, Pink), and technology-focused terminology (Dev, Code, Tech, Software program) to create authentic-appearing skilled identities.
Password evaluation reveals regarding safety practices that paradoxically aided within the operation’s publicity. Essentially the most ceaselessly used password sample “123qwe!@#QWE” appeared throughout a number of accounts, suggesting centralized password administration or shared operational protocols.
Two distinctive passwords, “Xiah” and “Jay231,” appeared completely inside this dataset and have been absent from the Have I Been Pwned database, indicating attainable operational significance or inside reference codes.
The prevalence of QWERTY keyboard patterns in password development helps intelligence assessments relating to the risk actors’ technological setting and suggests systematic password technology protocols relatively than particular person creativity.
Uncovered DPRK IT Employee Credentials:-
The investigation revealed in depth use of superior privateness instruments, together with Octo Browser for fingerprint obfuscation, FaceSwap know-how for video interview manipulation, and complex proxy networks by companies like IPRoyal.
Organizations should implement enhanced screening protocols, together with deepfake detection instruments, complete background verification processes, and systematic evaluation of applicant communication patterns to determine potential infiltration makes an attempt earlier than granting system entry.
Increase your SOC and assist your group defend your small business with free top-notch risk intelligence: Request TI Lookup Premium Trial.