A classy method to bypass Content material Safety Coverage (CSP) protections utilizing a mix of HTML injection and browser cache manipulation.
The tactic exploits the interplay between nonce-based CSP implementations and browser caching mechanisms, particularly concentrating on the again/ahead cache (bfcache) and disk cache methods.
Key Takeaways1. Researchers exploit browser caching to bypass Content material Safety Coverage protections.2. CSS methods extract CSP nonce values from meta tags by way of background requests.3. Browser cache manipulation reuses pages with recognized nonces for malicious payloads.4. Vulnerability impacts basic internet safety towards Cross-Web site Scripting assaults.
This analysis demonstrates how attackers can circumvent one of many internet’s most vital safety mechanisms by leveraging the inherent caching conduct of contemporary browsers, probably exposing numerous internet functions to Cross-Web site Scripting (XSS) assaults that have been beforehand considered protected.
CSS Injection with Cache Exploitation
In keeping with the Jorian Woltjer Report, the assault methodology facilities on exploiting the reuse of CSP nonce values by way of browser caching mechanisms.
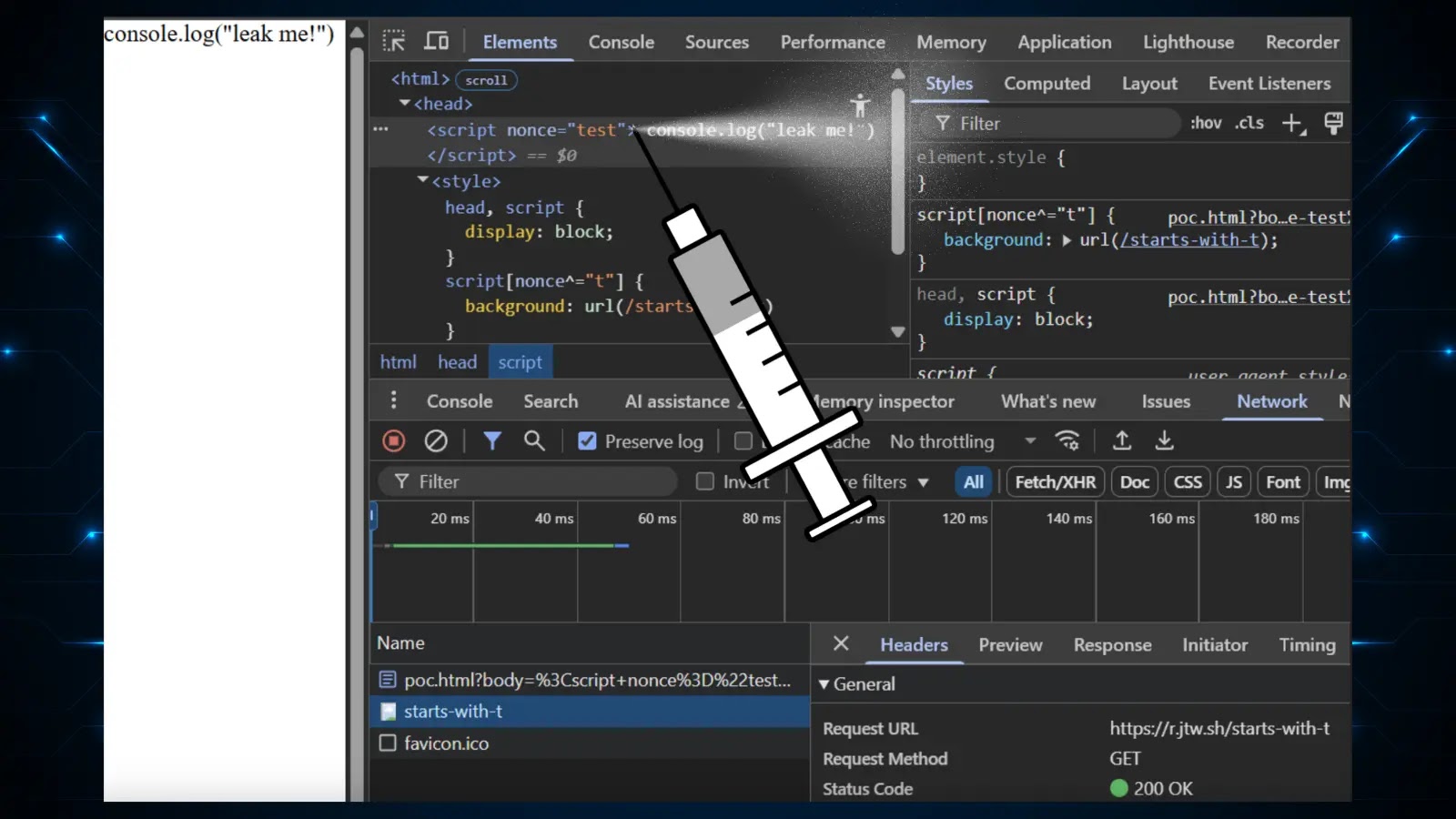
The multi-stage strategy begins with CSS injection to leak nonce values from the goal utility.
The method makes use of CSS attribute selectors to extract nonce values from meta tags containing CSP headers, as demonstrated within the proof-of-concept code:
The analysis crew found that whereas nonce attributes in script tags are protected against CSS selectors for safety causes, the identical values mirrored in meta tag content material attributes stay accessible.
This enables attackers to systematically leak nonce values utilizing CSS injection methods that generate a number of background requests, successfully reconstructing the entire nonce by way of overlapping character sequences.
The assault leverages Cross-Web site Request Forgery (CSRF) vulnerabilities to replace the injected payload whereas sustaining entry to the beforehand leaked nonce.
By exploiting the login endpoint’s lack of CSRF safety, attackers can modify the saved payload by way of type submissions:
The breakthrough lies in manipulating browser cache partitioning and the interplay between bfcache and disk cache.
When bfcache situations fail, reminiscent of sustaining window references, the browser falls again to disk cache, which preserves the unique web page with the recognized nonce whereas permitting dynamic content material updates.
The researchers recognized that cache entries are keyed utilizing Community Isolation Keys, comprising each the top-level web site and current-frame web site, enabling selective cache manipulation.
The exploit requires exact timing and cache administration, using completely different URL parameters to create distinct cache entries.
The method entails loading the goal web page with a novel parameter (/dashboard?xss), leaking the nonce, updating the payload by way of CSRF, loading the identical endpoint with out parameters to replace the profile cache, and at last navigating again to set off the cached web page with the brand new payload.
This analysis reveals vital implications for internet utility safety, as many functions depend on nonce-based CSP as a main protection towards XSS assaults.
The method works throughout fashionable browsers and requires solely two preconditions: the power to leak nonce values by way of HTML injection and separate payload supply mechanisms.
Safety professionals should now contemplate cache conduct when implementing CSP protections, probably requiring extra safeguards reminiscent of cache-control headers and improved nonce technology methods that account for browser caching mechanisms.
Examine reside malware conduct, hint each step of an assault, and make quicker, smarter safety selections -> Strive ANY.RUN now